Web Honeypots
PROJECTS


In Cybersecurity, staying ahead of malicious actors is a constant challenge. Today, I'm excited to share a project that I've been working on to contribute to the fight against cyber threats: a custom-built web honeypot.
What is a Web Honeypot?
A web honeypot is a security mechanism designed to lure in attackers by simulating a vulnerable environment. The idea is to attract malicious actors and monitor their activities, allowing us to study their methods, gather valuable intelligence, and strengthen our defenses against real-world attacks.
The primary goal of my web honeypot is to observe and analyze the tactics, techniques, and procedures (TTPs) used by attackers in the wild. By creating a convincing yet controlled environment, I can safely capture data on intrusion attempts, identify new threat vectors, and understand the behavior of different types of attackers. This information is crucial for developing more effective security strategies and improving the overall security posture of systems.
How It Works
My honeypot is designed to mimic a typical web application, complete with potential vulnerabilities that are commonly targeted by attackers. It features:
Simulated Login Pages: To attract brute-force attacks and credential stuffing
Fake Data: To simulate real user information and entice data theft attempts.
The system logs every interaction, capturing detailed information about the attack methods, IP addresses, payloads, and more. This data is then analyzed to identify patterns and potential threats.
Now let's talk about the honeypot
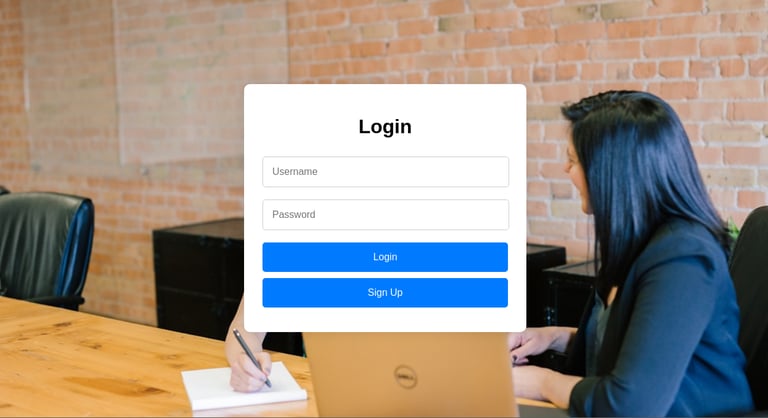
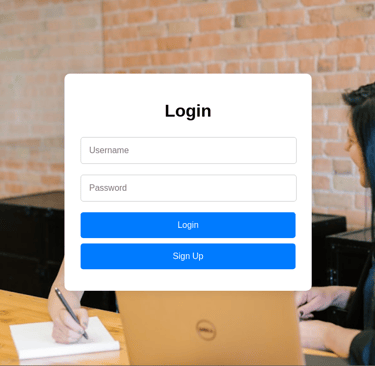
the first thing the attacker sees will be a login page where they can sign up or login, eventually they may end up using brute force but what they don't know is the login page will capture their Ip address and browser data immediately they click any of the buttons.
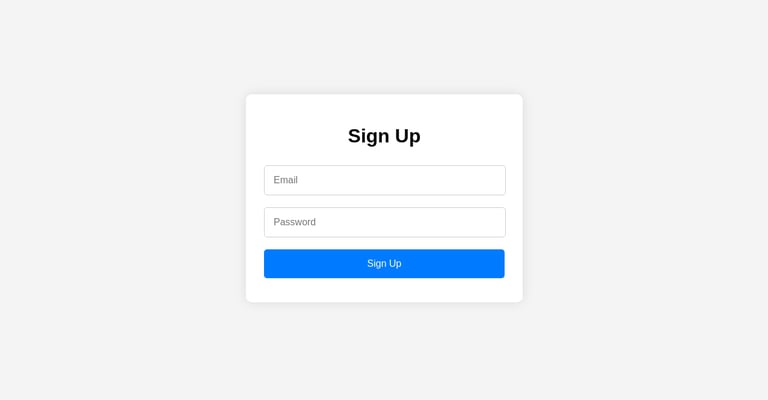
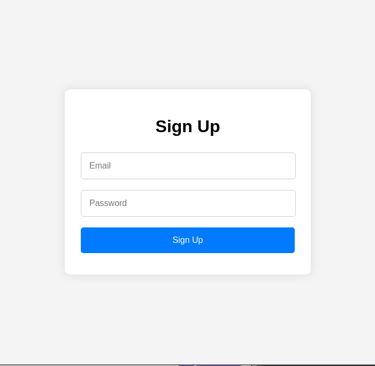
If they choose to sign up just to gain access, we record their inputs
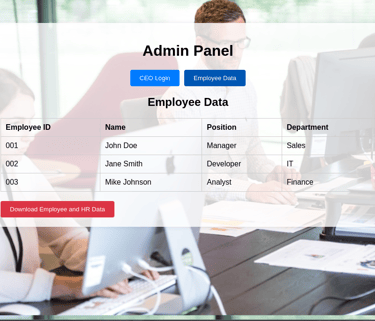
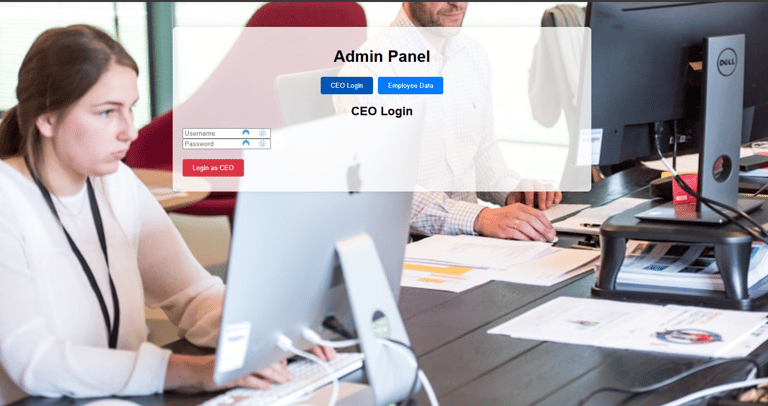
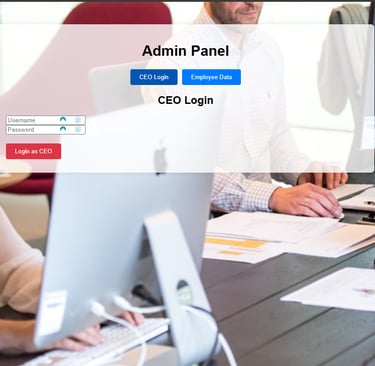
Once they have logged in or signed up, they will be presented with a fake admin panel and if you look closely, you will see a "Download Employee and HR Data" below. this may likely interest the attacker and they will try to download the data.
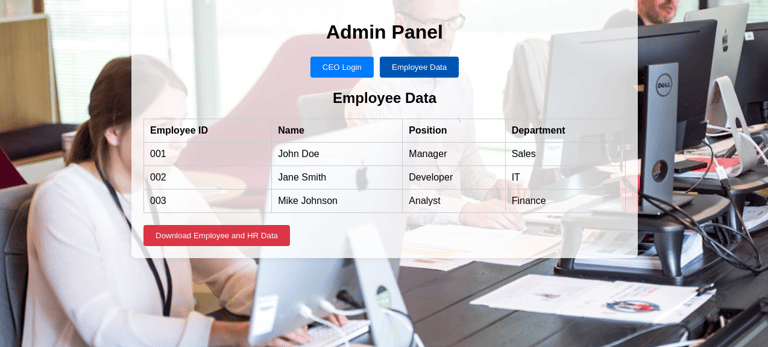
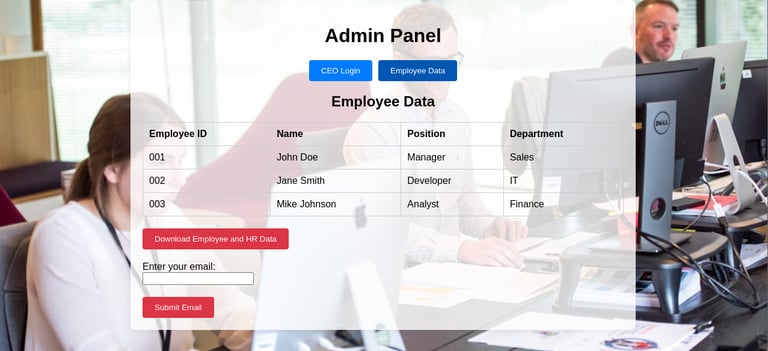
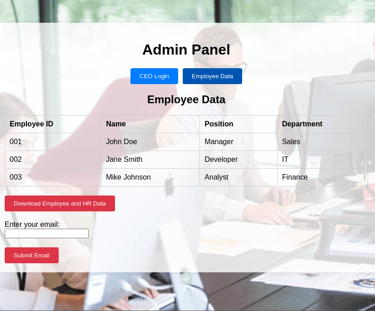
Immediately they click the button, they are prompted for an email address to receive the files, and their inputs would be recorded as well.
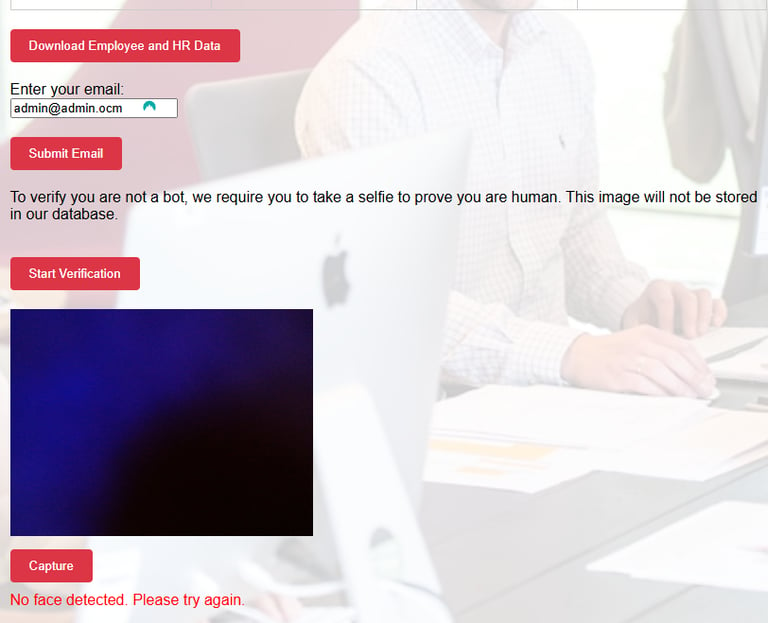
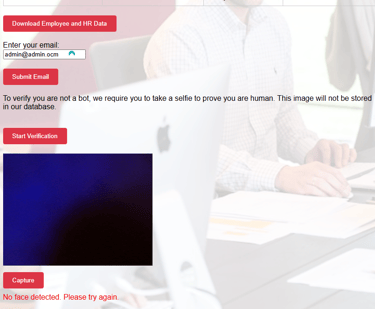
5. After providing an email address, they will be prompted to verify they are not a bot and are assured that their image would not be stored in our database but that's just a joke ha-ha.
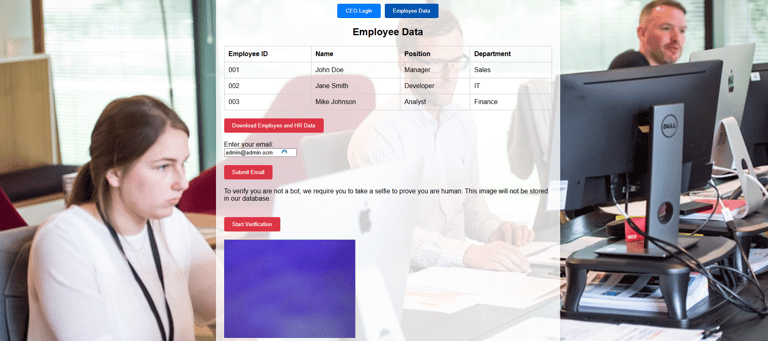
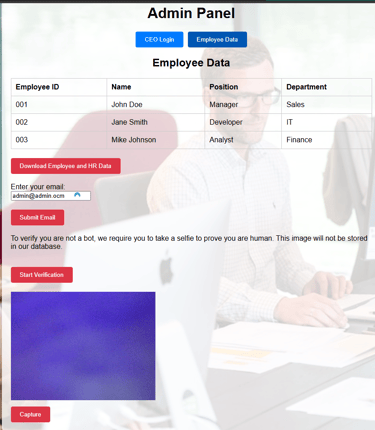
As usual some might want to be smart and not show their face or try to be slick, but little do they know that we have some technologies in place to detect their face. In other words, once they hit capture, the frame is scanned for the presence of a human face and if it finds no human face it won't accept the image.
Lastly, they will see a Ceo login page at the top which they might try to brute force or use an SQL injection attack to bypass login.
If you have questions or contributions about my project, feel free to reach me using the "Contact" form on this site.
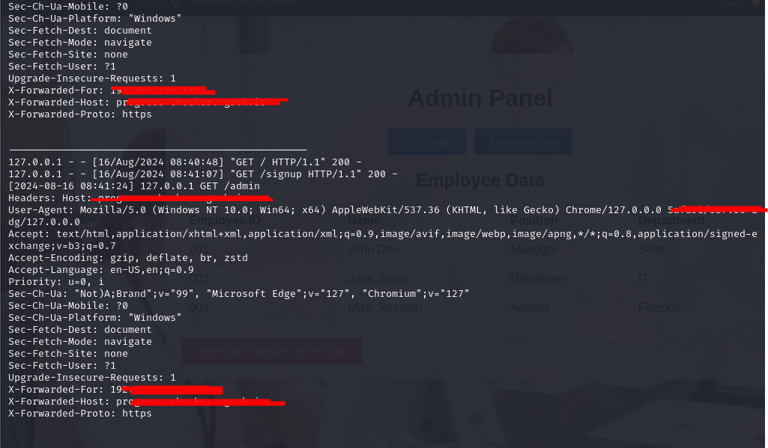
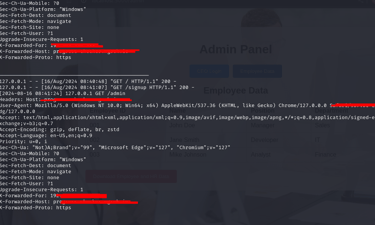
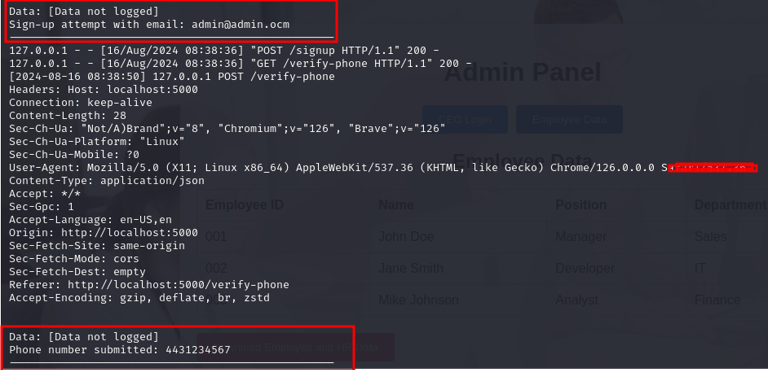
Now let's take a look at our logs
