Viruses: The Unseen Enemies of Your Computer
BLOGS


We’ve all heard the word “virus,” especially when it comes to computers, but what exactly is a computer virus?
What’s a Computer Virus?
Imagine a computer virus like a really annoying prankster who sneaks into your house and makes copies of themselves. Before you know it, there are hundreds of them, causing chaos. In the digital world, a virus is just a sneaky piece of software that copies itself over and over. Sometimes, it just spreads, but other times it can really mess up your computer by deleting files, stealing your data, or making your system slow down.
The key thing to remember is that a virus is all about self-replication—meaning it’s designed to make more copies of itself. That’s what makes it a virus, just like how real-world viruses spread from one person to another.
Real-Life Examples of Viruses
To help you understand, let’s look at a few famous viruses:
FakeAV.86: This virus pretends to be an antivirus program but is actually a Trojan horse—meaning it tricks you into thinking it’s helpful when it’s actually harmful. It first popped up in 2012 and targeted Windows computers. So, instead of protecting your computer, it sneaks in and causes trouble.
Flame: Discovered in 2012, Flame is like the James Bond of viruses. It was designed for spying and could do all sorts of sneaky things like recording what was happening on the screen and monitoring network traffic. Flame even had the ability to change its behavior depending on the antivirus software on the computer it infected, making it super hard to catch.
Wannacry: This virus caused a global panic in 2017 by encrypting files on computers and demanding a ransom in Bitcoin to unlock them. What’s crazy is that a fix for this virus was available before it hit, but many people hadn’t updated their systems—showing how important it is to keep your software up to date!
Emotet: This one tricked people by pretending to be a scanned copy of Edward Snowden’s memoir. Once someone opened the attachment, it would download a botnet—a network of infected computers that could be controlled remotely.
Locky: Like a digital kidnapper, Locky would encrypt your important files and then demand money to give them back. It was smart enough to even encrypt data on networked drives, not just the infected computer.


Different Types of Viruses
Not all viruses are the same. Here are a few types:
Macro Viruses: These are like tiny pranksters hiding in office documents. When you open a file, the virus activates and starts spreading.
Memory-Resident Viruses: These set up camp in your computer’s memory and stay there until you turn off your computer.
Multi-partite Viruses: These overachievers attack your computer in multiple ways at once, like messing with your hard drive and corrupting files.
Polymorphic Viruses: These are shape-shifters, changing how they look to avoid being caught by antivirus software.
How Do These Viruses Affect Forensics?
When it comes to catching the bad guys behind these viruses, it’s a bit like detective work. Viruses can be easy to find but hard to trace back to their creators. Investigators look for clues like how the virus behaves and what files it targets. They also check if all the infected computers have something in common, like visiting the same website.
But tracking down who made the virus? That’s the tricky part. It’s a slow process that involves piecing together tiny bits of information, much like solving a puzzle.
Logic Bombs: Another Digital Nasty
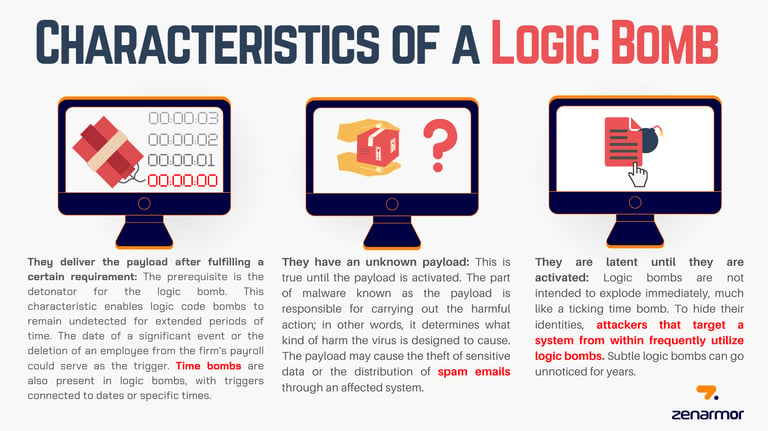
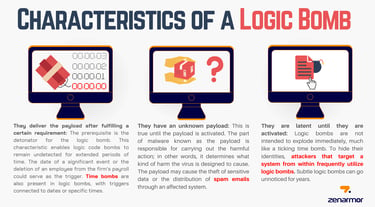
Now, let’s talk about something similar but a bit different—a logic bomb. A logic bomb is like a ticking time bomb inside your computer. It’s a piece of malware designed to do damage when certain conditions are met, like on a specific date or after a certain number of logins.
For example, in 2019, a programmer named David Tinley planted logic bombs in his employer’s spreadsheets. These bombs would go off and cause problems, forcing the company to call him to fix it, so he could keep getting paid. Not cool, right?
Forensics and Logic Bombs
Investigating a logic bomb is a bit easier than tracing a virus. The nature of the logic bomb itself usually gives investigators clues about who planted it—typically, someone with access to the system and knowledge of programming. Traditional detective work, like figuring out who had the motive, also comes into play.
Conclusion
Viruses and logic bombs are just two of the many digital threats out there. While viruses are all about spreading and causing chaos, logic bombs are more targeted and often more personal. Understanding these digital enemies helps us better protect our computers and data—and reminds us why it’s so important to keep our software updated and be cautious about what we download!
