Unveiling Hidden Messages: How Forensic Investigators Detect and Extract Steganography
BLOGSHACKS


In today’s world, where technology is embedded into our daily lives, even digital crimes have grown more sophisticated. One of the more elusive techniques used by criminals to hide sensitive or illegal information is steganography. Steganography involves hiding data within ordinary files like images, audio, or video, so it is invisible to the ordinary eye. Unlike encryption, which scrambles data to make it unreadable, steganography disguises the existence of the message altogether.
In this blog, we’ll talk about through the steps forensic investigators follow to uncover hidden information within computer files. Using forensic tools, I will demonstrate how to detect and extract these hidden messages. By the end, you’ll understand not only how steganography works but also how investigators can reveal the secrets hidden beneath the surface.
Understanding Steganography: What It Is and Why It Matters
Steganography has a long history, originating from the Greek words “steganos,” meaning hidden, and “graphia,” meaning writing. Its primary purpose is to embed secret information inside files that appear harmless. In ancient times, people would use methods like invisible ink or codes within letters to send secret messages. But in today’s digital world, criminals can hide data in seemingly normal digital files, such as images, without raising suspicion.
Modern digital steganography allows users to embed data within the code of an image or audio file so that the file looks unaltered. The hidden information could be anything from confidential messages to illegal content. For forensic investigators, detecting this hidden data is critical because it can provide crucial evidence in legal cases, such as fraud, data theft, or even terrorism.
The challenge? The hidden data is virtually undetectable without special tools. Let’s explore the tools and methods investigators use to reveal these hidden messages.
Step 1: Detecting Steganography Tools on a Suspect’s Computer
Before searching for hidden data, the first step is to identify whether the suspect has used any steganography software. If we can find steganography programs on the suspect’s computer, it’s a clear sign that they might be hiding data. To do this, we use Paraben’s E3, a powerful forensic tool designed for analyzing digital evidence.
What is Paraben’s E3?
Paraben’s E3 is a comprehensive forensic tool used by investigators to examine digital devices. It allows analysts to recover deleted files, extract hidden data, and even detect the presence of steganography software. With Paraben’s E3, investigators can scan the contents of a suspect’s hard drive and search for specific programs or software that might have been used to conceal data.
How We Use Paraben’s E3 to Detect Steganography Software
The first thing we do is open Paraben’s E3 on our investigation workstation. Once the tool is running, we need to use something called a hash database. A hash database contains the digital fingerprints (or hash values) of known software programs. By comparing these fingerprints with the files on the suspect’s computer, we can determine if the suspect has used any steganography tools.
To do this, we attach the hash database by clicking on the Hashes tab in Paraben’s E3 and selecting Attach Existing Database. This connects the database to the tool, allowing us to search for any known steganography software.
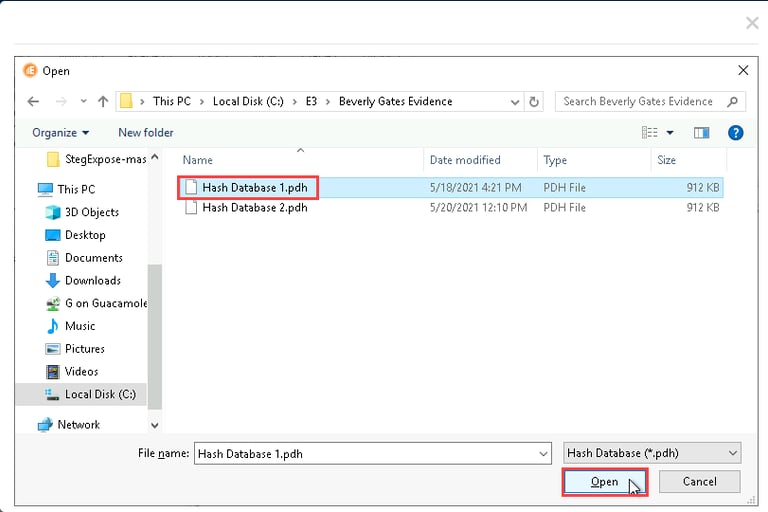
Once the database is attached, we run a search. Paraben’s E3 scans the suspect’s computer for any software that matches the hashes in the database. If a match is found, it indicates the presence of steganography tools, such as OpenPuff, which is one of the most common programs used to hide data.
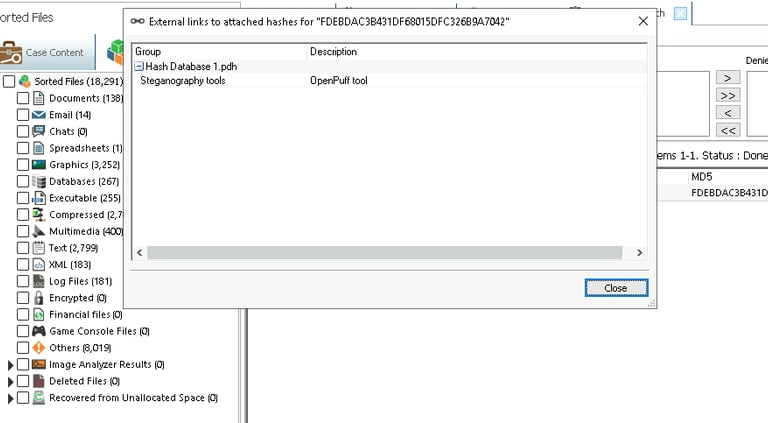
By finding steganography tools on the suspect’s computer, we’ve established that they likely used these programs to hide data, making it necessary to proceed to the next step.
Step 2: Identifying Files with Hidden Data Using StegExpose
Now that we know the suspect has steganography software installed, the next step is to figure out which files contain hidden data. We can’t go through every single file manually, so we use a tool called StegExpose to quickly scan multiple files for hidden information.
What is StegExpose?
StegExpose is a command-line steganalysis tool designed specifically for forensic investigators. Its primary purpose is to scan a collection of image files and identify any that may contain hidden data. The tool uses various algorithms to detect suspicious modifications in files—particularly those used to conceal information with steganography.
How We Use StegExpose to Find Hidden Data
We start by exporting image files from the suspect’s computer for analysis. Using Paraben’s E3, we browse through the suspect’s directories and export a folder that contains images—such as a folder named “Received.” These files could potentially be hiding sensitive information.
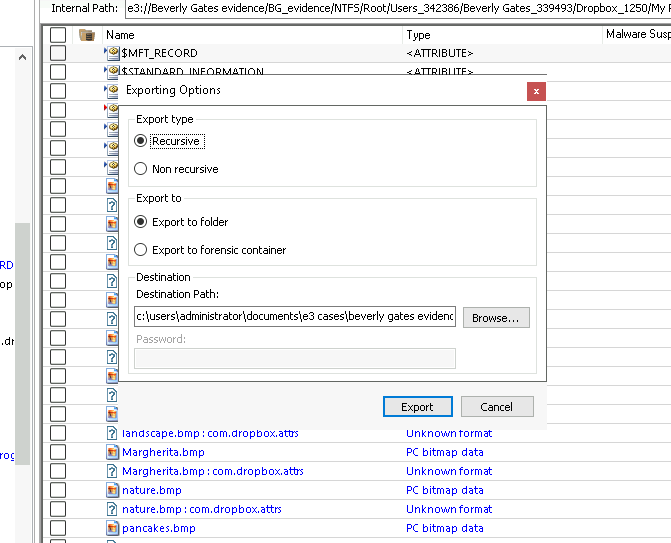
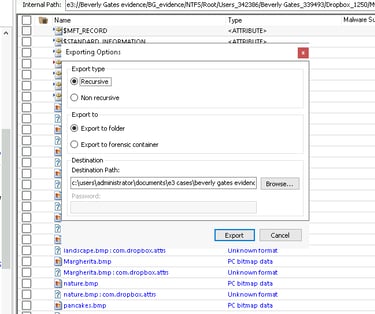
Once the files are exported, we open the Command Prompt on our forensic workstation. This is where we run StegExpose. We type a command to run StegExpose on the exported images. The tool analyzes each file and identifies any that contain hidden data by scanning for irregularities, such as manipulated pixels or metadata.
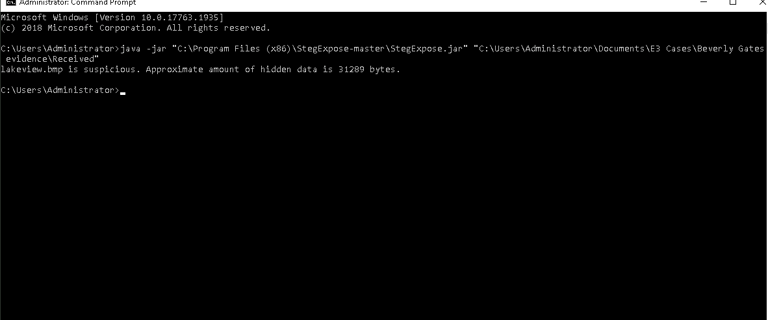
The command we type looks something like this:
After running the command, StegExpose flags any image files that contain hidden data. It even provides the size of the hidden data, giving us a clue as to what might be hidden inside the file.
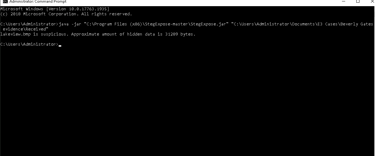
To verify the flagged image, we can open it in Microsoft Paint. While we may not be able to see the hidden data with our eyes, visually inspecting the file allows us to confirm that this is the correct file to investigate further.
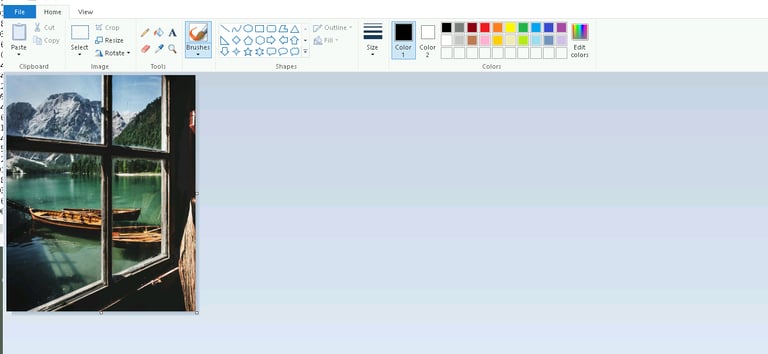
Now that we’ve identified the file, it’s time to extract the hidden data.
Step 3: Extracting Hidden Data Using OpenPuff
Identifying the file with hidden data is just the beginning. To retrieve the actual hidden information, we need to use a tool capable of extracting the concealed message. This is where OpenPuff comes in.
What is OpenPuff?
OpenPuff is one of the most widely used steganography tools. It allows users to both hide and extract data from digital media files, such as images, audio, and video. OpenPuff is particularly popular because of its professional-grade encryption features, which make it difficult for anyone to access the hidden data without the correct passphrase.
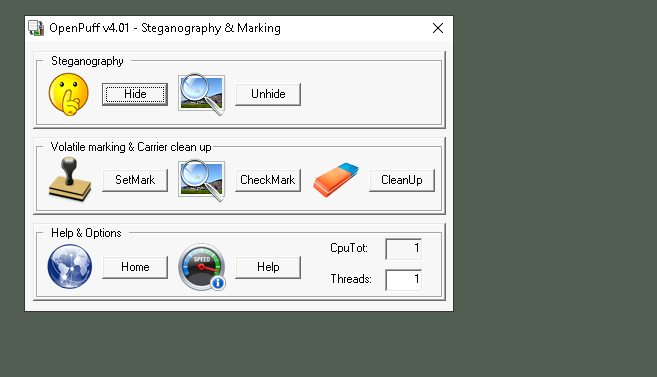
How We Use OpenPuff to Extract Hidden Data
First, we open OpenPuff by double-clicking the OpenPuff - Shortcut on our workstation desktop. Now that we’ve identified the file with hidden data (let’s say it’s an image called Lakeview.png), we need a passphrase to unlock the hidden information.
Luckily, while analyzing the suspect’s directory, we discovered a ReadMe file that might contain the passphrase. We open the file, and sure enough, it contains a single word that seems to be the key to unlocking the hidden data.
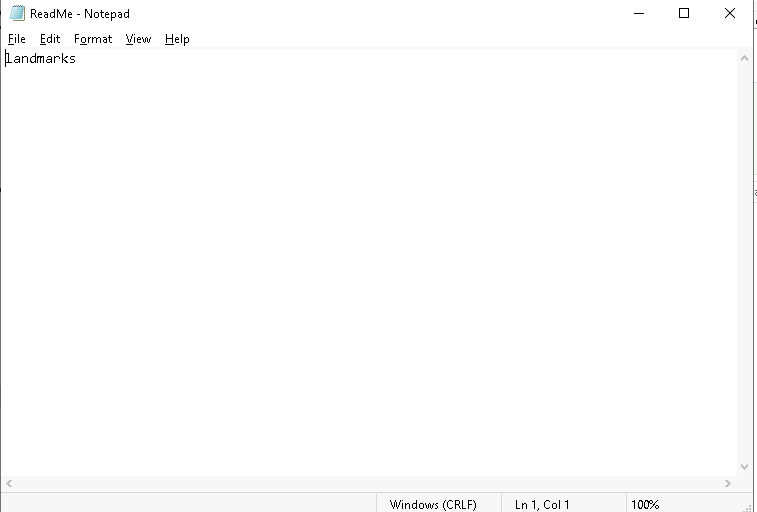
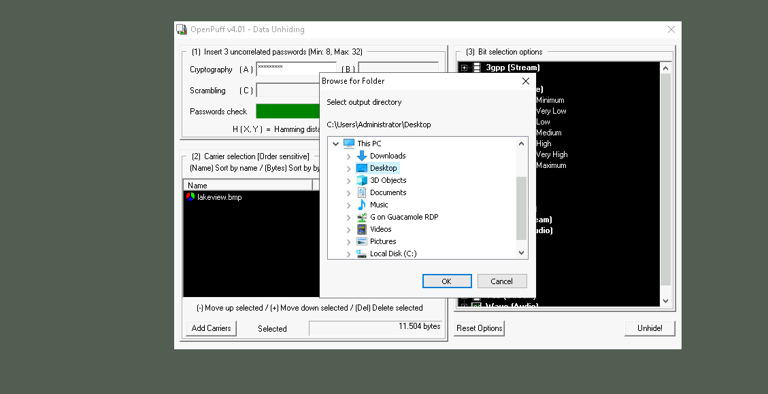
Next, we return to OpenPuff and click the Unhide button. Here, we input the passphrase we found in the ReadMe file. We then load the suspicious image file (Lakeview.png) and select the appropriate encryption method, ensuring that OpenPuff will decrypt the data.
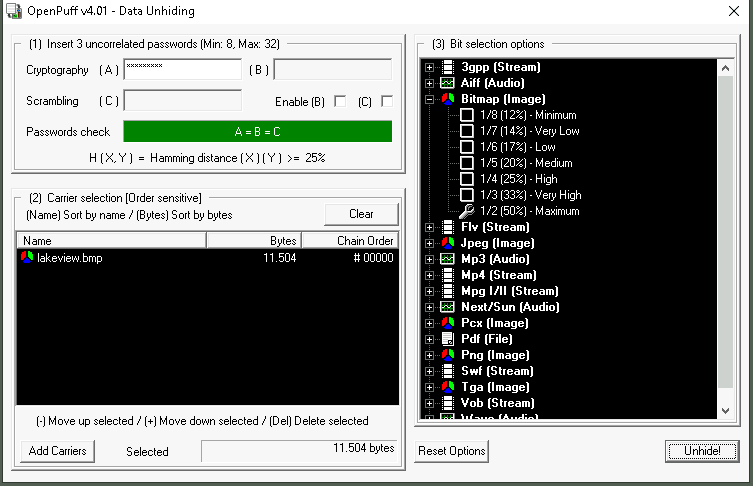
After we’ve set everything up, we click the Unhide! button, and OpenPuff extracts the hidden data from the image. The data is saved to the desktop as a new file, which could contain anything from secret communications to illegal information.
Step 4: Reviewing the Extracted Data
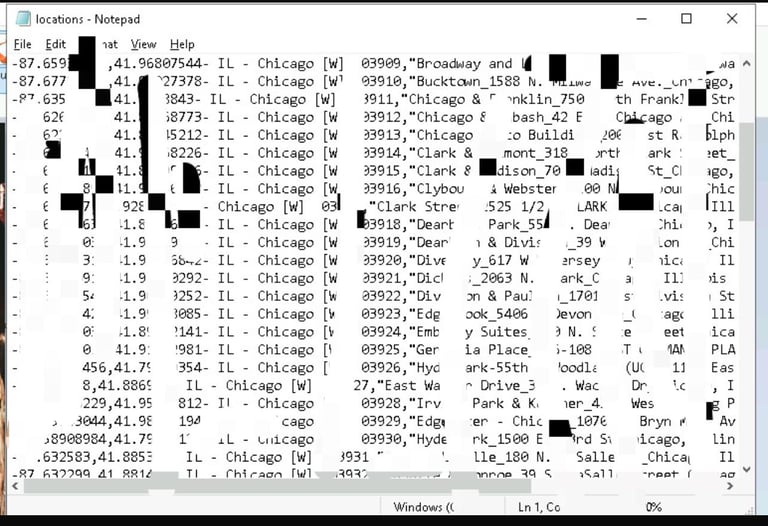
With the hidden data extracted, the final step is to open and review the file. This extracted file could be a text document, another image, or any type of data that the suspect may have hidden. The contents could provide critical evidence in a legal investigation, linking the suspect to illegal activities.
We double-click the extracted file to examine its contents. In some cases, this might reveal incriminating evidence, such as illegal transactions, private communications, or even sensitive documents the suspect wanted to keep hidden.
Conclusion: The Power of Steganography in Digital Forensics
Steganography is a sophisticated method for hiding information, but with the right tools and knowledge, forensic investigators can detect and expose even the most well-hidden data. From using Paraben’s E3 to detect steganography software, to identifying suspicious files with StegExpose, and finally extracting hidden messages with OpenPuff, the process of uncovering concealed data is both fascinating and essential in solving digital crimes.
Forensic investigators play a crucial role in revealing the truth that lies beneath the surface, ensuring that even the most covert communications can’t stay hidden forever. Whether it’s identifying illegal activities or recovering vital information, the ability to detect and extract hidden data is a vital skill in the world of digital forensics.


