Understanding Remote Access Trojans (RATs): A Comprehensive Guide
BLOGS


Imagine this: you’re browsing the internet or downloading what seems to be a harmless file, unaware that someone, somewhere, has just gained full control of your computer. They can view your files, log every keystroke, and even activate your webcam without your knowledge. This is the reality of Remote Access Trojans (RATs), a silent yet devastating threat that can turn your device into a hacker’s playground.
RATs are malicious programs that disguise themselves as legitimate files or applications, often hiding in email attachments, software downloads, or shady websites. Once installed, they grant attackers remote access to your system, enabling them to steal data, monitor your activity, and execute commands. Protecting yourself from such attacks is essential, and it begins with vigilance and proactive security practices.

The Importance of Safe Browsing
Your first line of defense against RATs is developing safe browsing habits. Avoid clicking on unverified links or downloading files from unknown sources, even if they appear legitimate. Hackers often disguise RATs in cracked or pirated software, so steer clear of websites offering these. While they may promise free software, they can cost you your privacy—or worse.
Visiting only trusted websites and scrutinizing unexpected email attachments or downloads can significantly reduce your risk of exposure. Think twice before clicking, and always verify the source.
Equip Yourself with Robust Security Software
Having strong security software is non-negotiable in today’s cyber landscape. Antivirus and anti-malware programs can detect and neutralize threats before they infiltrate your system. Regular updates ensure that your software stays effective against the latest malware variants.
Firewalls are another critical layer of defense, monitoring incoming and outgoing network traffic to prevent unauthorized access. Together, these tools create a solid shield against RATs and other cyber threats.
Keep Your Systems Updated
Outdated systems and software are like open doors for hackers. Cybercriminals often exploit known vulnerabilities in older versions of operating systems and applications. Regular updates close these gaps, making it harder for attackers to gain access. Enabling automatic updates ensures you never miss critical security patches, keeping your system protected at all times.
Add an Extra Layer with Two-Factor Authentication
Two-factor authentication (2FA) provides an added layer of security for your accounts. By requiring a second form of verification, such as a code from an authentication app or a hardware token, 2FA makes it significantly harder for attackers to access your accounts—even if they have your password. It’s a simple but effective measure that can make a world of difference.
Stay Informed and Share Knowledge
Knowledge is power when it comes to cybersecurity. Learning to recognize phishing attempts and social engineering tactics can prevent you from falling victim to schemes that trick you into handing over sensitive information. Educate your family, friends, and coworkers about these risks. A community that understands the basics of cybersecurity is a safer one for everyone.
A Real-World Example: The Infamous njRAT
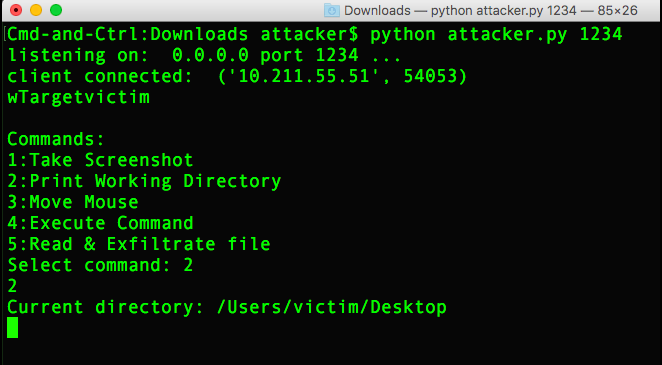
The dangers of RATs are best exemplified by njRAT, a notorious malware used by cybercriminals to infiltrate systems worldwide. This powerful RAT has been employed to steal login credentials, monitor webcams, and execute commands remotely. Cases like this highlight the need for constant vigilance and robust cybersecurity practices to keep such threats at bay.
Identifying and Eliminating RATs
If you suspect your system has been compromised by a RAT, immediate action is essential. Start by running a comprehensive scan with updated antivirus and anti-malware software to detect and remove the threat. Pay attention to unusual system behavior, such as unexplained slowdowns, high network activity, or unexpected pop-ups. These can be telltale signs of malware.
Inspect running processes using tools like Task Manager or Activity Monitor to identify unfamiliar programs. If all else fails, perform a clean reinstall of your operating system. While time-consuming, this method ensures the RAT is completely eradicated from your system.
