Uncovering Cybersecurity Breaches Using Forensic Analysis: Giggly Goofo Breach
BLOGS


In cybersecurity, incidents such as data breaches are not a matter of "if" but "when." An effective Incident Response (IR) process is essential for minimizing damage, recovering quickly, and most importantly, uncovering how the breach occurred. This blog will walk you through a thorough forensic investigation using advanced tools such as NetWitness Investigator (RWA) and Paraben’s E3, focusing on the critical steps required to investigate a data breach.
The Incident: A Breach at Giggly Goofo
In this scenario, Giggly Goofo, a game development company, experienced a serious security breach involving the exfiltration of sensitive data. As an incident responder, my objective was clear: determine how the breach occurred, identify the malicious actors, and find out whether any insiders were involved.
The two primary pieces of evidence provided for the investigation were:
Network traffic (PCAP file): A capture of all network traffic during the suspected time of the breach.
A forensic disk image: A full image of a suspected employee’s computer, which could contain key evidence of insider involvement.
Analyzing Network Traffic with NetWitness Investigator
The first step in the forensic investigation was to analyze the network traffic to understand how the breach occurred. NetWitness Investigator (RWA), a powerful network analysis tool, was used to examine the PCAP file. This file contained a record of all network activity during the suspected time of the breach.
Step 1: Importing and Visualizing Network Traffic
After loading the PCAP file into NetWitness Investigator, I used the tool’s Time Graph feature to visualize the volume of network sessions over time. The graph immediately revealed a significant spike in activity on July 13, 2021, at 3:33 PM. This spike suggested abnormal behavior, potentially involving data exfiltration.
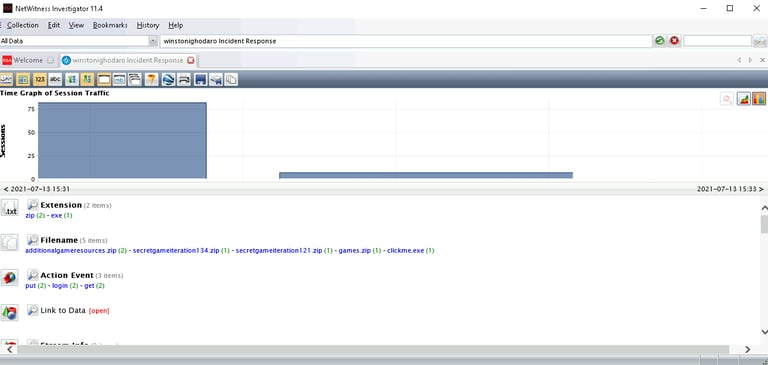
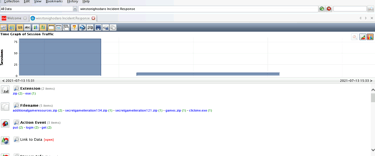
Step 2: Investigating the Sessions Involved
Next, I drilled down into the specific network sessions around the time of the spike. Focusing on the Source IP Addresses, one address—157.165.0.25—stood out. This was an external IP address that connected with one of Giggly Goofo’s internal systems, an unusual and concerning event.
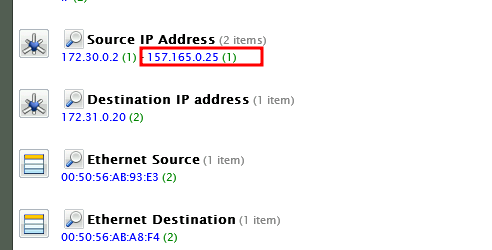
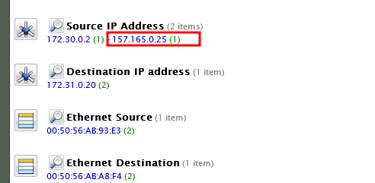
By investigating the session that occurred at 3:33 PM, I discovered an FTP transfer involving a significant amount of data. The credentials used for the transfer—GigglyGoofoDev and password Il0veC0d!nG—suggested that someone had either compromised these login details or had been granted unauthorized access.
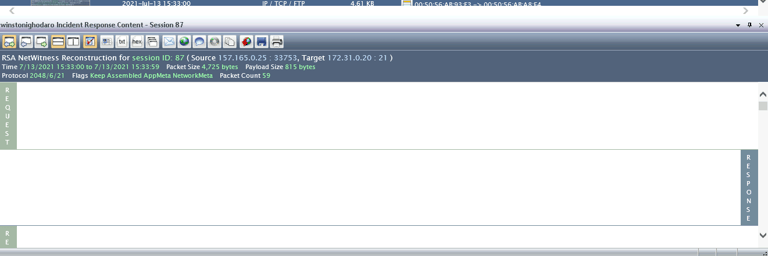
The files transferred included several .zip files, indicating that large, potentially sensitive data was being exfiltrated from Giggly Goofo’s network. The presence of this session confirmed that a breach had occurred, and data had been stolen using the company’s own FTP service.
Uncovering Insider Involvement with Paraben’s E3
Having identified the external data transfer, the next step was to investigate whether any internal employees were involved. There was a suspicion that an employee might have facilitated the breach. To investigate this, I used Paraben’s E3, a comprehensive forensic analysis tool, to examine the disk image of the suspected employee’s computer.
Step 1: Loading and Examining the Disk Image
I loaded the disk image into Paraben’s E3, which provided a complete snapshot of the employee’s machine, including emails, documents, and logs. One of the key areas to investigate was the employee’s email database, as it could provide insight into whether they had communicated sensitive information to external actors.
Step 2: Searching for Email Evidence
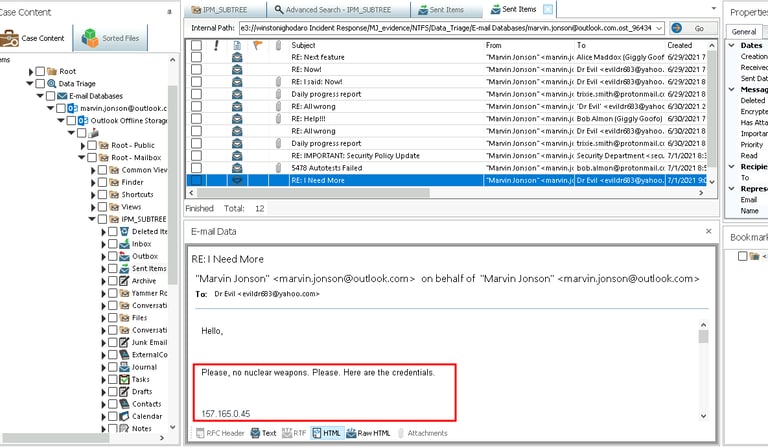
Using Paraben’s Advanced Search functionality, I searched the email database for any reference to FTP credentials. The search revealed a startling discovery: the employee had sent an email containing the FTP login credentials to an external party, Dr. Evil. The email, which included the username and password, gave Dr. Evil full access to the company’s internal systems.
The timestamps on the email aligned perfectly with the time of the FTP transfer I had identified earlier during the network traffic analysis. This email was a critical piece of evidence, confirming that the employee had knowingly provided access to sensitive systems.
Step 3: Investigating System Changes
Beyond the email evidence, further analysis of the disk image revealed that the employee had installed a keylogger on their machine, potentially under the instruction of Dr. Evil. This keylogger would allow the attacker to capture all keystrokes, including login details for various systems within the company.
Using Paraben’s Email Analysis feature, I uncovered a phishing email prompting a team member to install an update or risk paying a fine. This explains how the keylogger got into the victim's computer.
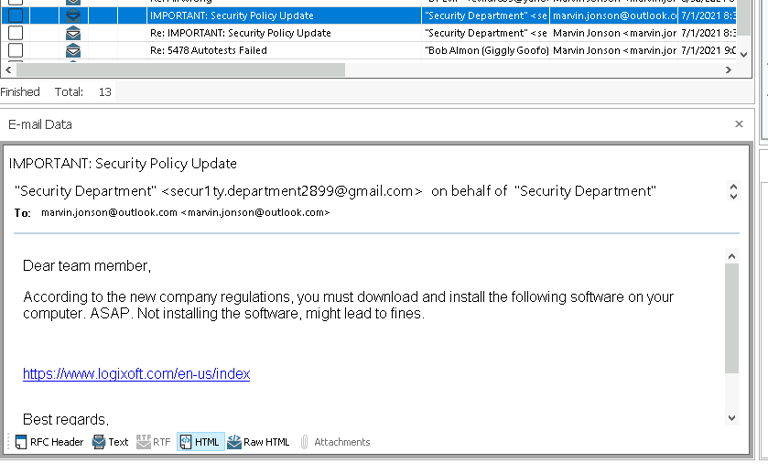
Compiling the Incident Response Report
With the evidence gathered from both the network traffic analysis and the disk image investigation, I compiled a detailed Incident Response Report. This report documented:
Timeline of the Breach: The exact times when the breach occurred, from the FTP transfer at 3:33 PM to the insider’s email communications with Dr. Evil.
Scope of the Breach: The systems and data affected, including the FTP server used to exfiltrate the data.
Key Evidence: Screenshots and logs showing the FTP transfer, the email containing credentials, and the installation of malicious software.
Next Steps: Recommendations for securing the company’s network, including tighter controls on internal access to sensitive credentials and increased monitoring of internal communications.
This report served as a comprehensive documentation of the breach and was crucial for both internal reviews and potential legal actions against the employee involved.
Conclusion: Lessons Learned from the Forensic Investigation
This incident response investigation underscored the importance of using advanced forensic tools like NetWitness Investigator and Paraben’s E3 to uncover the full scope of a cyber breach. By meticulously analyzing network traffic and system data, I was able to identify both external and internal actors responsible for the data theft.
The key takeaway from this investigation is that a thorough incident response must involve both network analysis and internal forensic investigations. External threats are often paired with insider involvement, and tools like RWA and Paraben’s E3 allow investigators to gather the evidence needed to address both.
As organizations continue to face sophisticated cyber threats, having a robust incident response process in place is essential. By following the steps outlined in this guide, incident responders can uncover key details in any breach, secure their systems, and protect their organization from future attacks.
