The Best Hacking Games to Play in 2024
BLOGS


If you’re trying to learn hacking concepts or processes and want a more engaging experience, hacking games may be a good option.
Hacking games can provide an engaging and fun experience while teaching you some basic penetration testing concepts.
While no video game can emulate real hacking and remain simplified and accessible to a broad audience, they can offer an excellent way to accelerate your learning.
Our readers often ask us how realistic hacking games are, and if you can learn hacking from a video game.
In this article, you’ll find out more about this as we walk you through some fun hacking games that provide a good level of realism while still being educational.
Ready? GO!
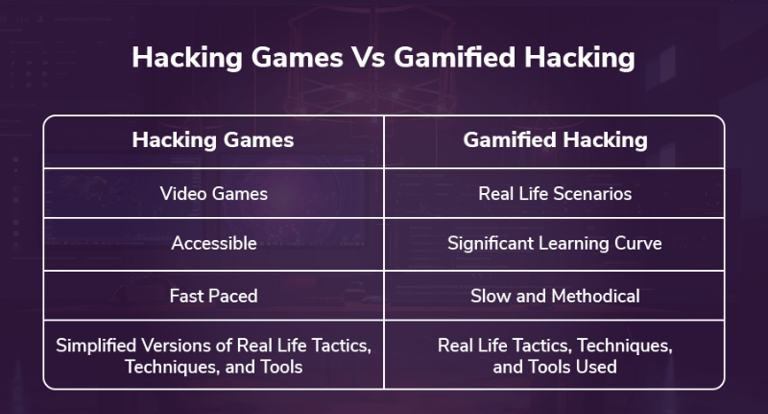
Hacking Games vs Gamified Hacking
Before diving into which games are out there, you must know the difference between gamified hacking and hacking games.
Gamified Hacking is real hacking but in a CTF-like (Capture the Flag) environment. Several services offer Gamified Hacking, such as HTB (Hack the Box) or TryHackMe.
With gamified hacking services, you can learn real-life hacking skills. However, starting out with the real thing can be difficult, as hacking is a complex and lengthy process.
So, having something to bridge that gap between considering cyber security and compromising a real system can be essential to your growth. This area of learning is where hacking games can come into play in a fun way.
Hacking games are, simply put, video games that have hacking elements. Often, they are streamlined versions of gamified hacking situations to be more entertaining to casual audiences.
Hacking Games often simulate tools like Nmap but limit the possible options and features. Tools are often streamlined to the point that a three-step process in a real penetration test is just one simple command.
Both gamified hacking and hacking games have their place in the learning process.
Many people start with hacking games to see if they are interested in hacking and then move on to gamified hacking to build upon the basic concepts they learned in hacking games.
Now, let's dive into some of the best games to help you learn cyber security!
1. ThreatGEN: Red vs Blue
Steam Score: 89%
Summary
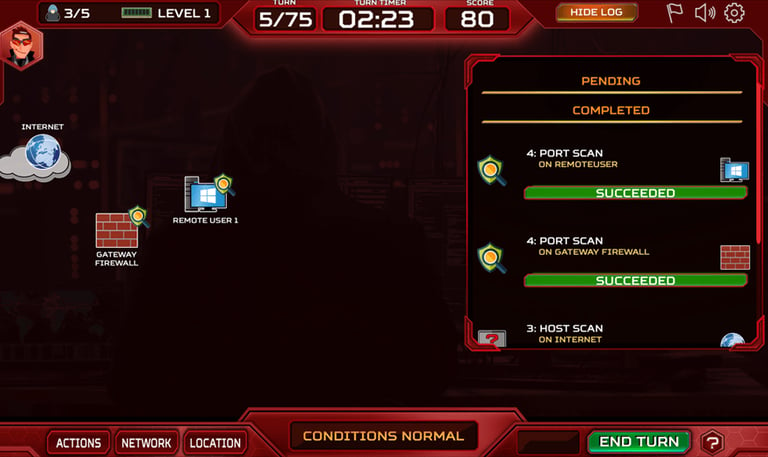
ThreatGEN: Red vs. Blue is a turn-based and primarily educational game.
It’s extremely detailed and shows the process of a typical red team vs blue team engagement from start to finish.
ThreatGEN doesn't have a story; each match is independent. The objective of each one depends on which team you are playing as.
The red team’s objective is to compromise as much of the blue team's network as possible. Meanwhile, the blue team's objective is to defend their network as effectively as possible.
Gameplay and Features
The gameplay varies depending on which team you’re playing as.
As the red team, you start with no knowledge of the network you are attacking or what is vulnerable.
You must use your “hacker” resources to uncover everything as you go and research new tools and attacks throughout the game as you discover vulnerabilities.
The blue team starts with full knowledge of the network and starts to harden it against attacks from the red team throughout the game.
The blue team has to manage money, staff, and system uptime, all while working to track down the red team.
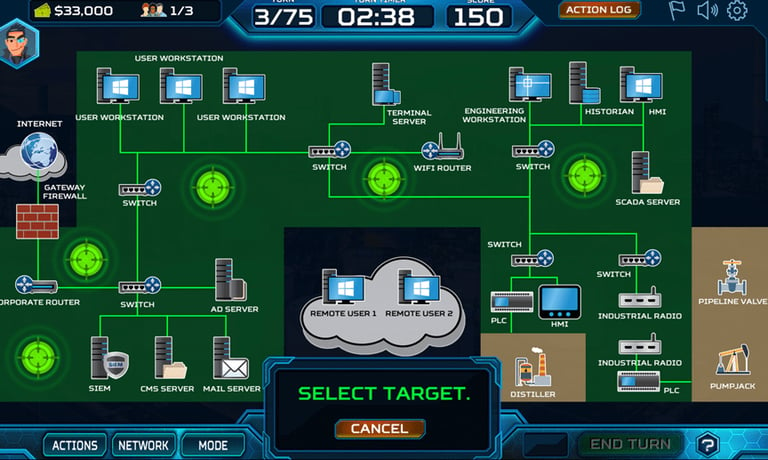
Both teams must research new tools and methods to improve their chances of winning or countering the other team.
For the red team, it just takes a hacker and time. For the blue team, it takes time, staff, and money. The blue team has many more moving parts to keep track of, similar to real life.
Realism and Educational Value
The concepts and processes used in this game are extremely accurate to real life.
You could easily transfer the knowledge you gained in this game directly to your learning, as the game does a great job of outlining the flow of a real attack from both sides.
It also has a built-in wiki that explains how to play the game, diving deeply into cyber security industry concepts.
At any point, if you want to learn more about the attack you are doing on the red team, you can pull up the wiki and read further. The content inside of the wiki is accurate and easily digestible.
This applies to the blue team as well. If you are curious about what a certain action is or does, you can pull up the wiki and check. This gamification of industry concepts really helps to accelerate your learning—even with complex topics like Digital Forensics and Incident Response.
However, if you want to learn hands-on skills, this game is not enough. No names of real-life tools are used, and no explanations as to how the found vulnerabilities are exploited or mitigated exist within the game.
Not learning hands-on skills at this stage is not necessarily bad, as understanding the hacking process is also essential.
You may know complex tools like Mimikatz or others exist, but knowing at what stage of an attack to apply them is also critical.
Overall, this game is a great tool to become more familiar with cyber security concepts.
You’ll learn the typical red team engagement process and the strategies blue teams use to defend against malicious actors.
Both of which are very relevant and directly transferable to your learning. Many of the same topics and processes are covered in certifications like the CompTIA Security+.

2. Hacker Simulator
Steam Score: 76%
Summary
This real-time game, Hacker Simulator, places you in the shoes of a black hat hacker who takes on jobs from shady customers. Your main objective is to gain as much reputation and money as possible by completing various hacking jobs.
Gameplay and Features
Hacker Simulator strives to emulate the life of a black hat hacker. You will use cut-down and simplified versions of some real-life tools to achieve the assigned jobs, all while jumping between wifi networks to avoid police detection. You’ll also need to clear your tracks in a simplified manner after each hack.
You can walk around your apartment and an alleyway just outside, where you’ll collect PC parts you can purchase to upgrade your computer. You can also buy new hacking tools and cryptocurrency mining equipment to make money passively.
The game features a simulated Linux style desktop that allows you to move windows and have any layout you want, similar to any modern operation system.
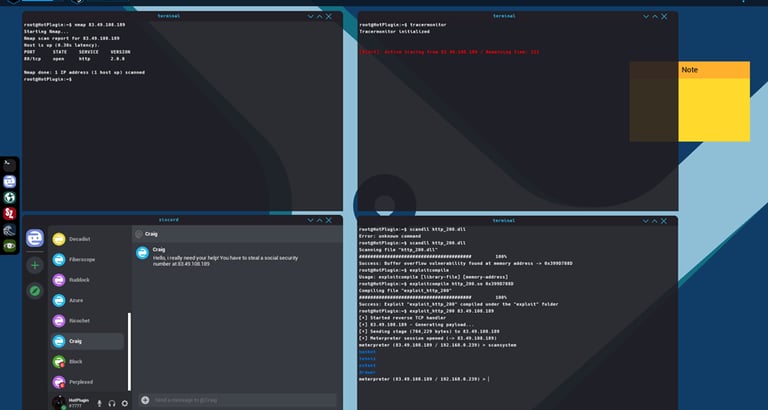
Realism and Educational Value
Hacking Simulator offers realistic elements and educational value.
While you’ll need more than hopping local wifi networks to avoid law enforcement in real life, it does introduce the concept of evasion techniques. And the simplified commands strike a good balance between real syntax and fun.
While simplified, the tools and methods used are rather accurate. The process of conducting a social engineering attack in the game is similar to real life, as is the process of scanning host machines to find vulnerabilities. It even uses real port numbers for the protocols you’ll discover.
The game gets less convincing when it comes to the exploitation of vulnerabilities.
While searching for vulnerabilities in real life is time-consuming and tedious, the game makes it very simple. This is a good idea in a video game, but from an educational standpoint, it only teaches the player a minimal amount.
Hacking Simulator also features several stand-in versions of real tools. The common file transfer tool File-Zilla and the Tor Browser are featured in a knock-off fashion. There are several other tools replaced by a similarly named replica that perform roughly the same tasks as they do in real life, which can be a good way to learn what tools are good for certain activities.
Overall, Hacking Simulator is a fun game with semi-realistic elements that could help you learn hacking techniques.
While you won’t be able to take the commands you used in the game directly to something like a CTF or practice lab, it would assist you in having a rough idea of what steps you should be taking.
However, it wouldn’t teach you how to identify a vulnerability on a real machine.

3. Hacknet
Steam Score: 93%
Summary
Hacknet focuses heavily on the story of a recently deceased master hacker named Bit, who created the ultimate hacking operation system, Hack-OS (similar to Kali Linux or Parrot OS).
Bit’s death triggers a failsafe that reaches out to your character to investigate his death and keep Hack-OS from falling into the wrong hands.
Gameplay and Features
Hacknet has quite a large amount of mechanics and features. There’s a rather realistic emulation of a real Linux-based terminal as your primary hacking method, and a dynamic network map is featured as you progress through a network.
It also features an intuitive and cool-looking GUI (Graphical User Interface). It features fully navigable target computers that allow you to do anything you would like to them—even delete their entire system.
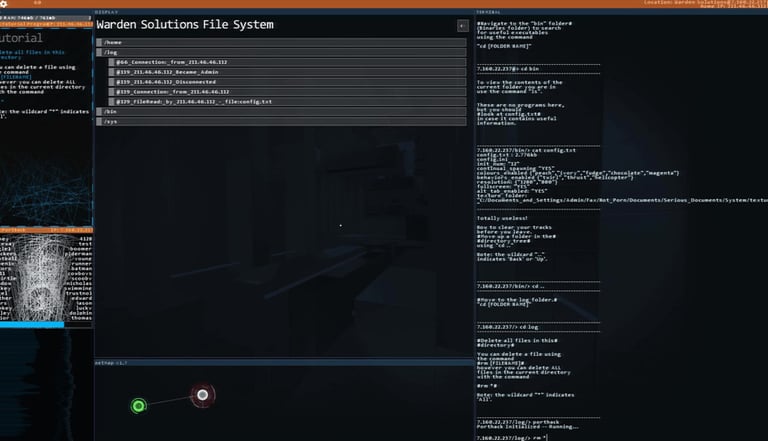
There is also a timed component in some networks. Occasionally, a network will have security measures that actively trace your connection once you start to hack their systems. In these cases, you must do your work quickly and get out while covering your tracks.
Realism and Educational Value
Hacknet strives to be realistic in many areas while having several gamified mechanics.
The navigation of systems via the command line is extremely realistic, and the directory structure of target systems and networking information is also very similar to real life.
Many of the terminal commands you use are real Linux commands. However, the syntax of most hacks you employ is quite basic. This can be a good thing from an entertainment standpoint as it reduces the game's complexity and keeps the hacking tempo quite high.
You’ll not learn coding from this game, but you’ll learn quite a bit during your playthrough, including some real Linux command line commands, networking knowledge, Linux file system structure, and general hacking concepts.
All of this knowledge can be directly transferred to your learning. However, none of the hacks you use are true to life in their syntax or capability. The game is more about the puzzle of performing a hack than a true-to-life simulation.
Overall, Hacknet is a great tool for getting some experience of what it feels like to be a hacker.

4. TIS-100
Summary
TIS-100’s primary objective is to repair corrupted code to uncover the mysteries of an old assembly-based system. As you progress, you discover secrets about the person who created the system and for what purpose.
Gameplay and Features
The gameplay of TIS-100 mainly revolves around inputting assembly commands to fix a section of corrupted code.
You do this by solving a puzzle that changes from level to level. To solve puzzles you’ll have plan a lot and go through trial and error.
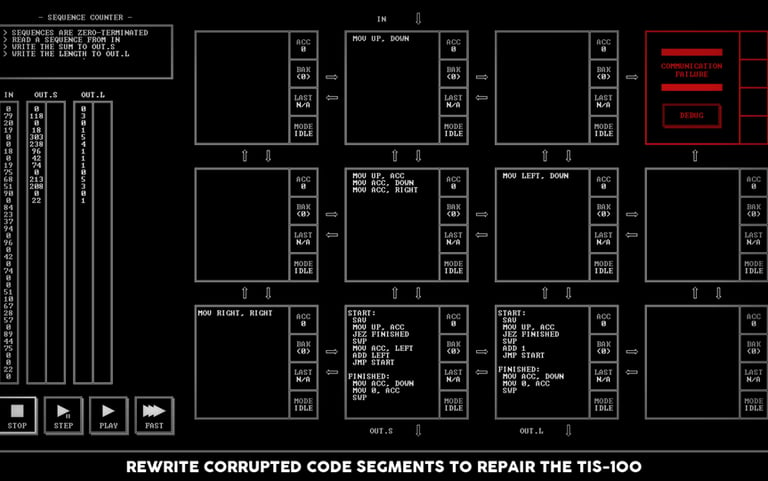
TIS-100 does not feature an upgrade system or any other meaningful progression systems. The entirety of the gameplay revolves around solving puzzles.
Minimizing the number of instructions and nodes you use to solve them is the primary challenge.
Realism and Educational Value
TIS-100 is extremely realistic and educational. It’s a true-to-life simulation of assembly language programming. While the goal is to solve a puzzle rather than create a program, the methods used in the game are the same as in real life.
You’ll learn a lot about assembly language.
Since code is typically broken down into assembly language during reverse engineering, you can directly apply these skills to your learning. This game would give you a strong foundation in assembly that you can use to undertake more complex cyber security topics, like training in reverse engineering.
TIS-100 has a very steep learning curve. This isn’t a game you could just pick up and start playing in a few minutes, and it’ll take some time to understand. Thankfully, it includes a manual to help you comprehend the assembly language mechanics and how it’s used inside the game.
Overall, TIS-100 is a great learning experience if you want to get into topics like reverse engineering. If you want to dive deeply into some programs and how they work, knowing assembly is invaluable in malware analysis.

