Step-by-Step Guide to Mobile Device Forensics: Investigating iOS and Android
ARTICLES


Mobile devices hold an immense amount of data, often becoming the centerpiece of investigations. From text messages and notes to app usage and photos, these devices store the digital fingerprints of their users. This blog outlines the steps I took to analyze an iPhone and an Android device using Paraben’s E3 forensic tool. By following this guide, you’ll see how forensic investigators uncover and document evidence in a case.
Case Scenario: The Bonnie and Clyde Investigation
Two suspects, Bonnie and Clyde, are under investigation for car theft. Their iPhone and Android devices are suspected of containing crucial evidence. My task as a digital forensic investigator was to analyze these devices, uncover relevant data, and compile the findings into a forensic report.
Investigating the iPhone
Step 1: Setting Up the Case
The first step was to create a new case in Paraben’s E3 forensic tool and import the iPhone data. This data had been previously acquired, allowing for an in-depth analysis of the device.
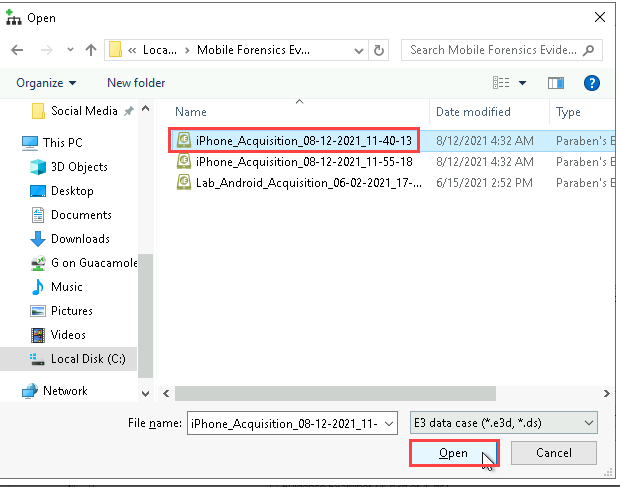
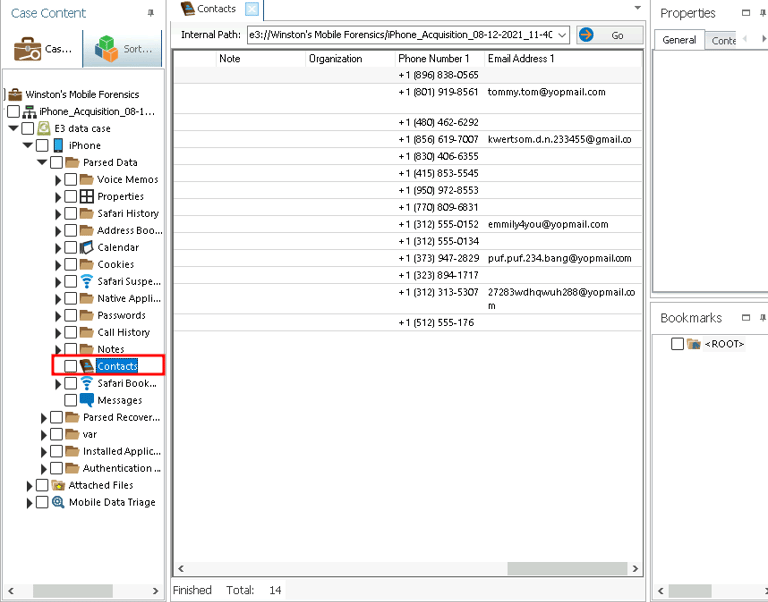
Step 2: Reviewing Contacts
I analyzed the contacts on the iPhone to identify individuals who could be linked to the suspects. This step revealed potential accomplices and provided a clearer picture of their network.
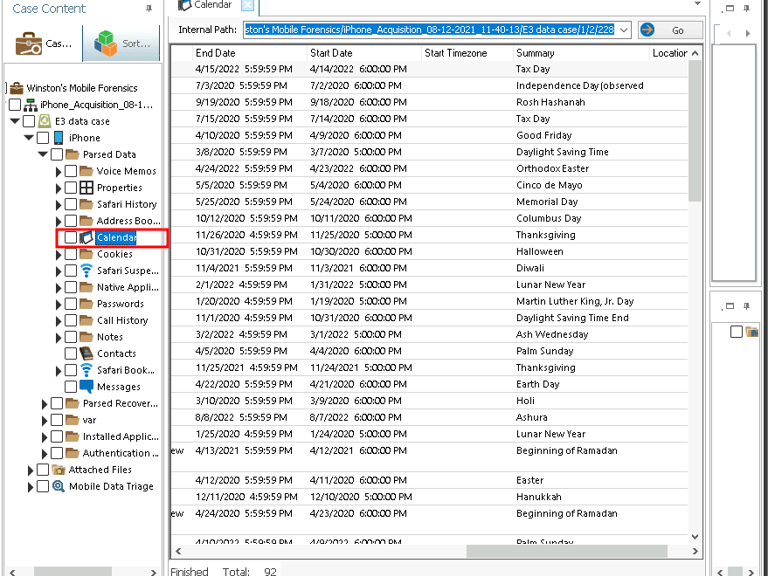
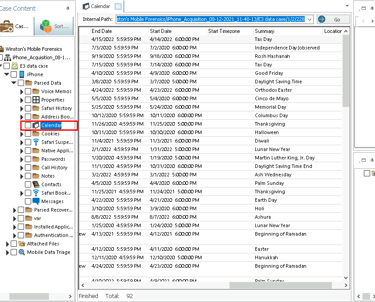
Step 3: Examining Calendar Events
The Calendar app contained a suspicious event with a car emoji in the description, suggesting it might be related to the planned car theft.
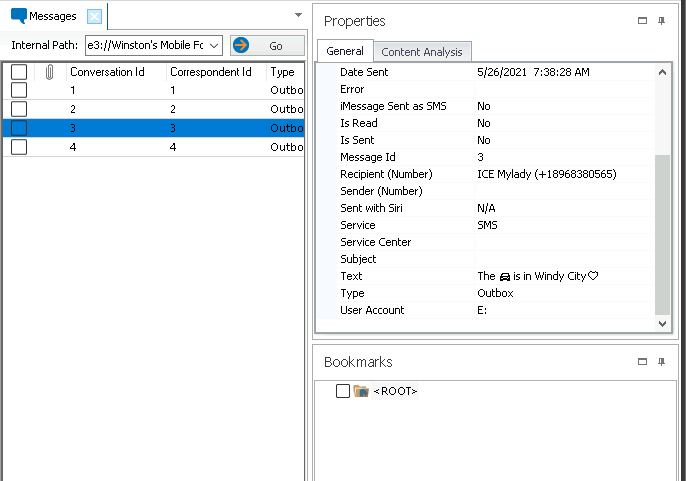
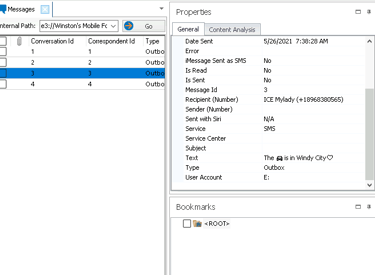
Step 4: Analyzing Messages
The Messages app provided incriminating evidence, including:
A text referencing a specific car.
A message mentioning “Windy City,” potentially linking the suspects to a known location.
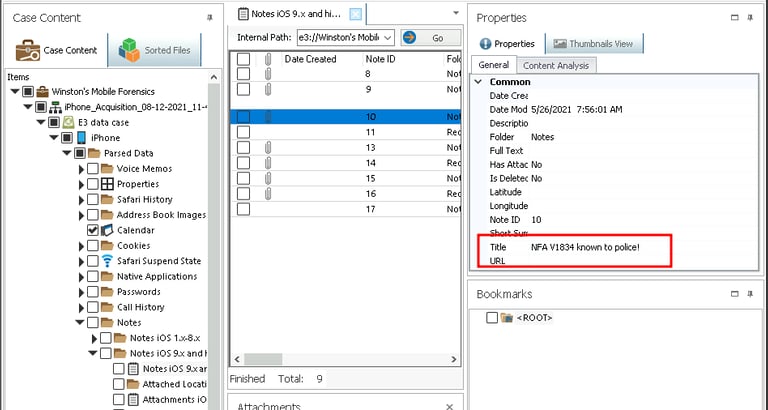
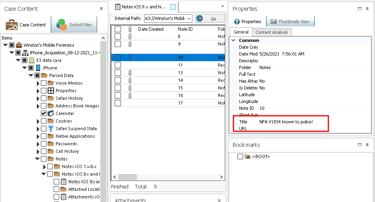
Step 5: Inspecting Notes
I reviewed the Notes app, which contained references to swapping license plates and a specific license plate flagged by law enforcement. These entries directly tied the suspects to their criminal activity.
Step 6: Analyzing Photos
Using the Content Analysis tool in E3, I located images of cars and license plates saved on the iPhone. These photos were bookmarked as evidence.
Step 7: Generating the Report
After analyzing the iPhone’s data, I bookmarked all relevant evidence (contacts, messages, calendar events, notes, and photos) and generated a detailed forensic report using Paraben E3.
Investigating the Android Device
Step 1: Importing Android Data
I imported the Android phone’s data into the same Paraben E3 case file. The tool automatically categorized the data into sections like contacts, messages, apps, and more.
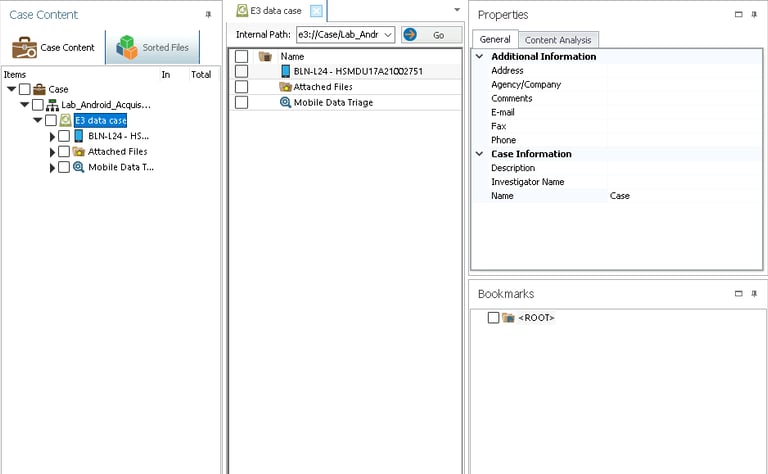
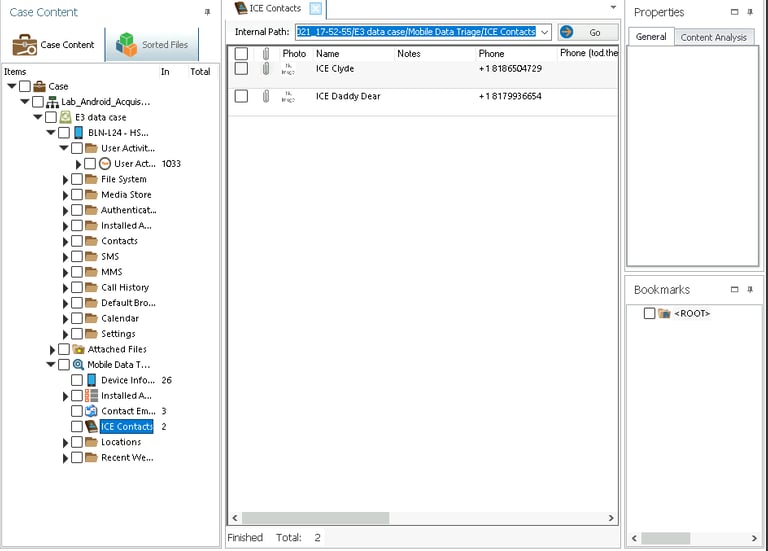
Step 2: Reviewing ICE Contacts
The device’s ICE (In Case of Emergency) contacts listed Clyde and Daddy Dear, confirming that the device belonged to Bonnie. This step linked the Android phone to the suspects.
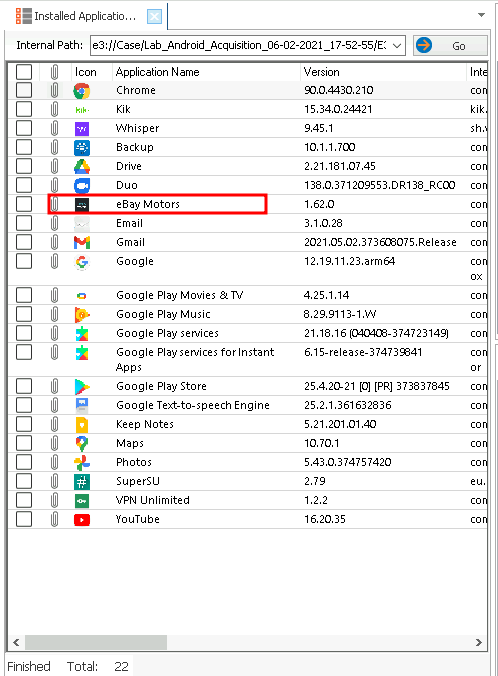
Step 3: Investigating Installed Apps
The installed apps included eBay Motors, a platform potentially used to sell stolen vehicles. This discovery tied the suspects to illegal sales.
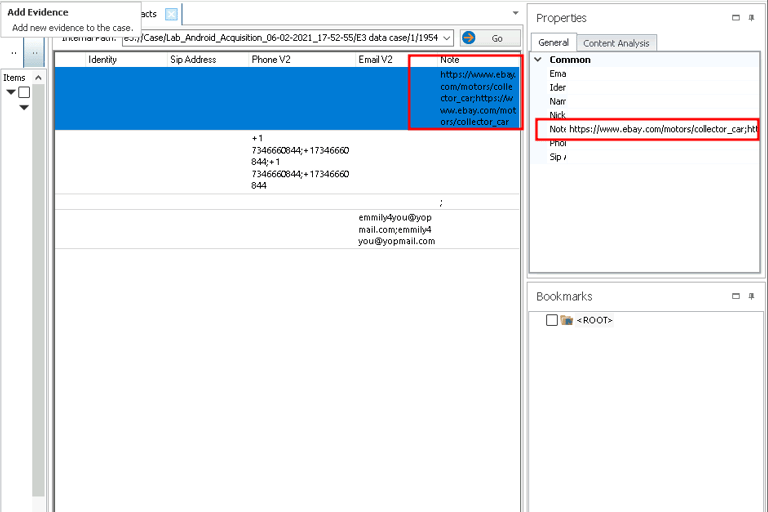
Step 4: Recovering Deleted Contacts
Using Paraben E3’s recovery tools, I retrieved deleted contacts. One of the recovered contacts contained a partially deleted eBay URL, reinforcing the connection to stolen vehicle sales.
Step 5: Analyzing User Activity Timeline
The User Activity Timeline in Paraben E3 provided a detailed view of app and browser activity during the suspected crime timeframe. It showed:
Anonymous communication on Whisper.
Searches for cars on Chrome.
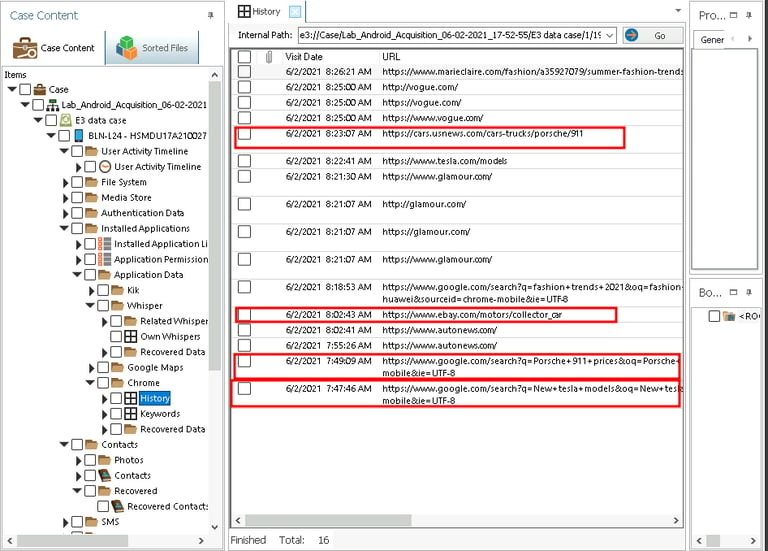
Step 6: Reviewing Browser and App Data
The Chrome browsing history revealed searches for car listings and online marketplaces, while the Whisper app contained discussions about specific cars.
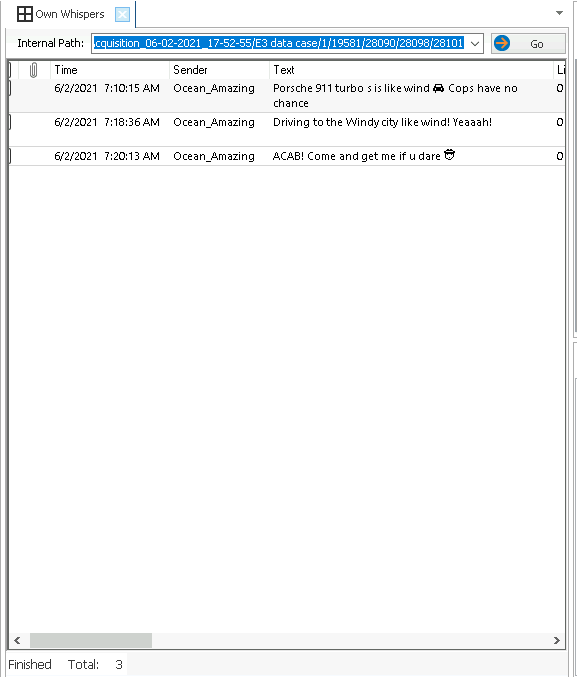
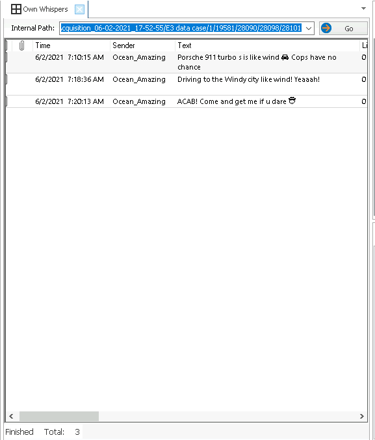
Step 7: Generating the Report
As with the iPhone, all evidence from the Android device was bookmarked and included in a forensic report. This ensured that the findings were well-documented and ready for presentation in court.
Key Takeaways from the Investigation
Detailed Workflow Is Essential: Following a structured process ensures that no critical evidence is overlooked.
Deleted Data Can Be Recovered: Even deleted contacts, messages, and files can hold valuable clues.
App Data Holds Clues: Reviewing installed apps and their activity often uncovers links to criminal behavior.
Timelines Tell the Full Story: The User Activity Timeline feature is invaluable for reconstructing events.
Final Thoughts
This investigation highlighted the power of mobile device forensics in uncovering hidden connections and activities.
