Stealthy GTPDOOR Linux malware targets mobile operator networks
BLOGS


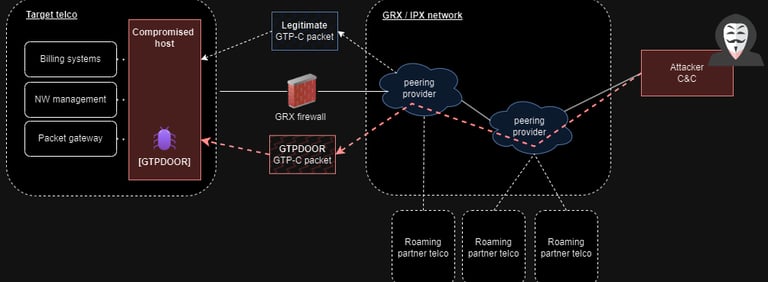
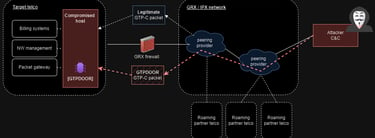
Security researcher HaxRob has uncovered a newly identified Linux backdoor named GTPDOOR, tailored for clandestine activities within mobile carrier networks. The threat actors associated with GTPDOOR are suspected to focus on systems neighboring the GPRS Roaming Exchange (GRX), such as SGSN, GGSN, and P-GW, which could grant them direct entry into a telecom's core network.
GRX, an integral part of mobile telecommunications, facilitates data roaming services across diverse geographical regions and networks. Meanwhile, the Serving GPRS Support Node (SGSN), Gateway GPRS Support Node (GGSN), and P-GW (Packet Data Network Gateway for 4G LTE) constitute crucial components within a mobile operator's network infrastructure, each fulfilling distinct functions in mobile communications.
Given that the IP address ranges of SGSN, GGSN, and P-GW networks are publicly available in documentation, the researcher suggests they are the probable targets for initiating access to the mobile operator's network, as they are comparatively more exposed to the public domain.
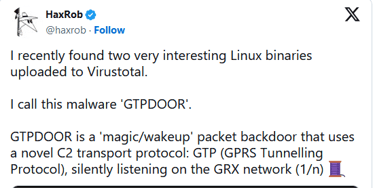
In his write-up, HaxRob Explained that GTPDOOR is likely a tool belonging to the 'LightBasin' threat group (UNC1945), notorious for intelligence-collection operations targeting multiple telcos worldwide.
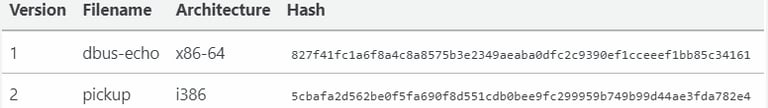
The researcher discovered two versions of the backdoor uploaded to VirusTotal in late 2023, both passing largely undetected by antivirus engines. The binaries targeted a very old Red Hat Linux version, indicating an outdated target.
The stealthy GTPDOOR operation
GTPDOOR is a sophisticated backdoor malware tailored for telecommunications networks, leveraging the GPRS Tunnelling Protocol Control Plane (GTP-C) for covert command and control (C2) communications.
It is designed for deployment in Linux-based systems adjacent to the GRX, responsible for routing and forwarding roaming-related signaling and user plane traffic.
Using GTP-C for communication allows GTPDOOR to blend with legitimate network traffic and utilize already permitted ports that aren't monitored by standard security solutions. For additional stealth, GTPDOOR can change its process name to mimic legitimate system processes.
The malware listens for specific GTP-C echo request messages ("magic packets") to wake up and execute the given command on the host, sending the output back to its operators.
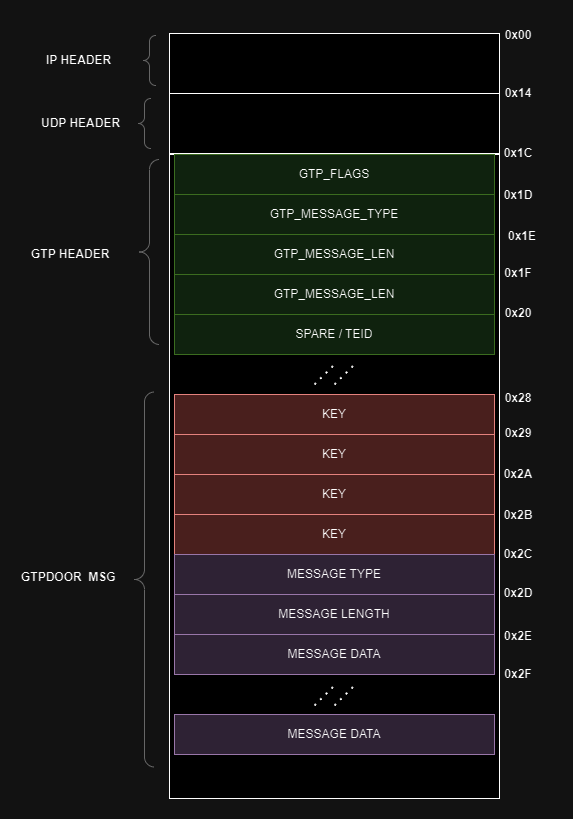

The magic GTP packets contain authenticated and encrypted contents, employing a basic XOR cipher to ensure that only authorized operators can manage the malware.
GTPDOOR v1 offers the following functionalities on compromised hosts:
- Setting a new encryption key for C2 communications
- Writing arbitrary data to a local file named 'system.conf'
- Executing arbitrary shell commands and returning the output
GTPDOOR v2 extends these capabilities with:
- Allowing specification of IP addresses or subnets permitted to communicate with the compromised host through an Access Control List (ACL) mechanism
- Retrieving the ACL list for dynamic adjustments to the backdoor's network permissions
- Clearing the ACL to reset the malware
Additionally, HaxRob emphasizes the malware's capability to be discreetly probed from an external network, triggering a response via a TCP packet transmitted through any port.
Detection and defense mechanisms entail vigilant monitoring for abnormal raw socket behaviors, unexpected process titles, and distinct indicators of malware, such as redundant syslog processes.
Outlined below are the recommended detection procedures:
- Utilize lsof to inspect for open raw sockets, which could signify a security compromise.
- Employ netstat -lp --raw to uncover unusual listening sockets that may indicate unauthorized activity.
- Identify processes imitating kernel threads by scrutinizing abnormal PPIDs.
- Search for the presence of /var/run/daemon.pid, a mutex file typically utilized by GTPDOOR.
- Investigate the existence of an unexpected system.conf file, potentially generated by the malicious software.


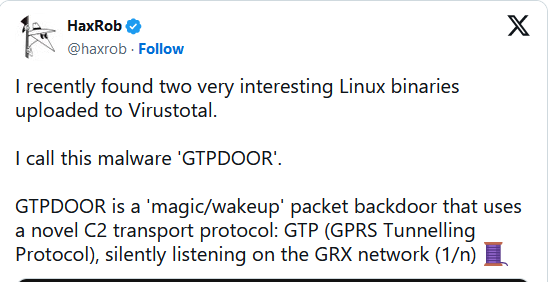
Write your text here...The following YARA rule for defenders to detect the GTPDOOR malware has also been provided.