Snapchat Phishing using Grayfish.
SOCIAL ENGINEERING


In this tutorial, we'll explore how malicious actors leverage freely available tools to execute Snapchat phishing attacks. Snapchat, a widely used social app, has unfortunately become a target for such attacks. Victims are often duped into divulging their Snapchat login credentials to fake websites, unknowingly falling prey to phishing scams.
Prerequisites:
1. A PC running any common operating system such as Windows or Linux.
2. A functional web server software installed on the PC.
3. Access to a target device, which can be of any type.
Grayfish Features:
- Templates are lightweight (under 20KB), ensuring fast webpage loading.
- Images are base64 encoded to avoid external and internal linking.
- Highly compressed codes with unnecessary elements removed.
- Victim cannot bypass the login form until all required inputs are filled.
- Custom preview link (image + title + description) when shared on any website.
- Includes an admin login panel designed for simplicity.
Steps for Snapchat phishing using Grayfish:
In this guide, we'll install and use Grayfish on Kali Linux.
Step 1: Installing XAMPP
To set up Grayfish for Snapchat phishing, we'll first install a web server software like XAMPP. The installation process is straightforward. Visit the XAMPP website, download the installer for your operating system, and then run the installer from the Downloads directory on Linux.

After the installation is complete, we can run the webserver and the required services using the command.
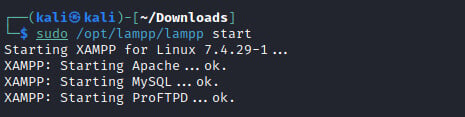
Step-2: Copy Grayfish files
We have to download grayfish files from its GitHub repository. We will move grayfish files to the htdocs folder that has been created after installing xampp. This folder can be found at /opt/lampp/htdocs on Linux.
Step-3: Provide required permissions for Grayfish to run
If we try to run grayfish, we may get an error due to a permissions issue, we have to give grayfish the required permissions for it to run from the htdocs folder for Snapchat phishing. To change the permissions we use the command.
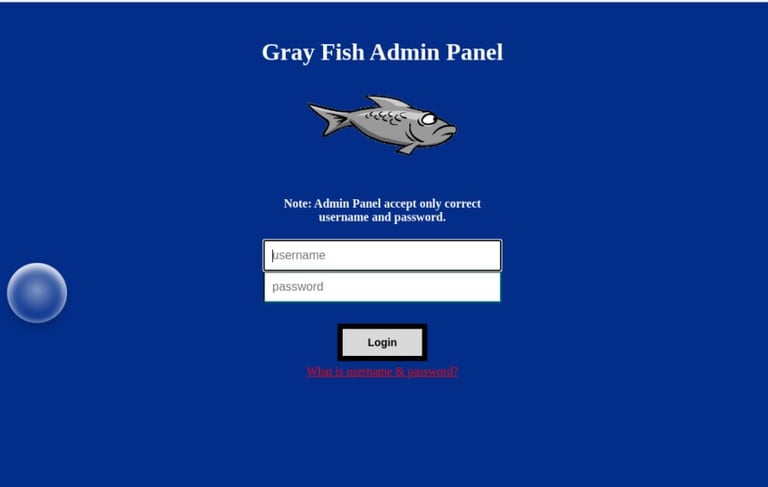
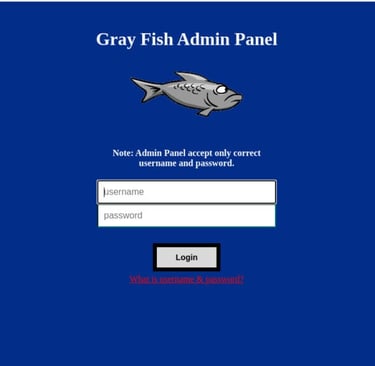
Step-4: Access Grayfish
We can now try to access the grayfish administration page by opening a browser and navigating to localhost/grayfish. If you have done each step shown above correctly, the grayfish login page should appear as shown in the image below. the default admin username is “fish” and the default password is “fish”.
Step-5: Phishing pages
Once logged in we can now launch a Snapchat phishing attack. Grayfish has phishing pages for several popular websites including Google, Microsoft, Instagram, Facebook e.t.c. On the main page, we can now be able to see links to different phishing pages for different popular websites as shown in the image below.
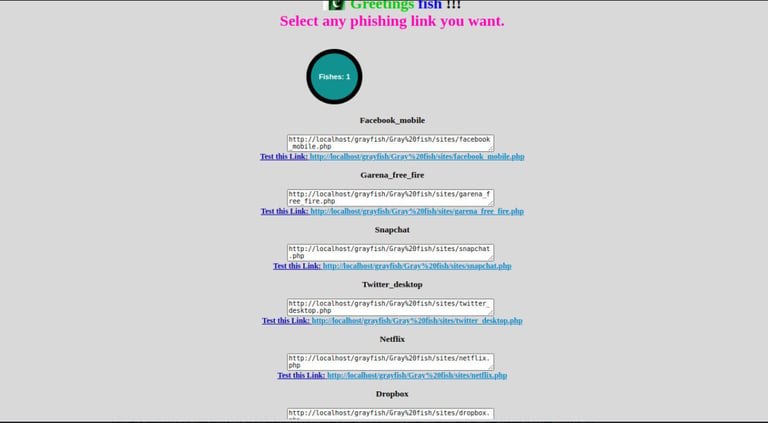
Step-6: Share the Snapchat phishing link
To carry out Snapchat phishing, you can copy and share the Snapchat phishing link with the victim. Once he/she clicks and provides the required information, the information will be logged on grayfish administration page. But that is not yet what we need. As you can see, the attack can only be carried out on targets within our network. If you want to do Snapchat phishing over the internet, we have to use ngrok to ensure our phishing webpage can be accessed over the internet.
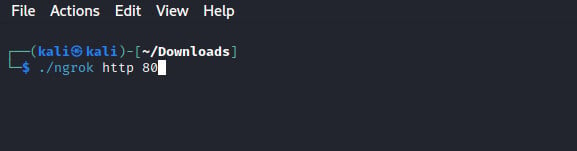
After running the command, we can access the grayfish admin panel using the link we generated on ngrok as shown in the image below.
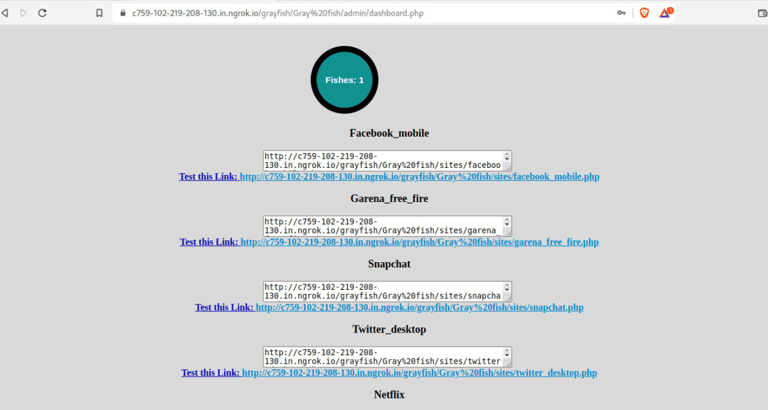
On the image above, we have phishing links which we can share over the internet depending on the site you want to phish passwords for. Since we are doing Snapchat phishing, we will share the respective phishing link with the victim. We can also use an URL shortening service to avoid raising alarms. Applying social engineering tactics will ensure the success of phishing. Below is the login page the victim will see once he/she clicks on the link sent to him/her.
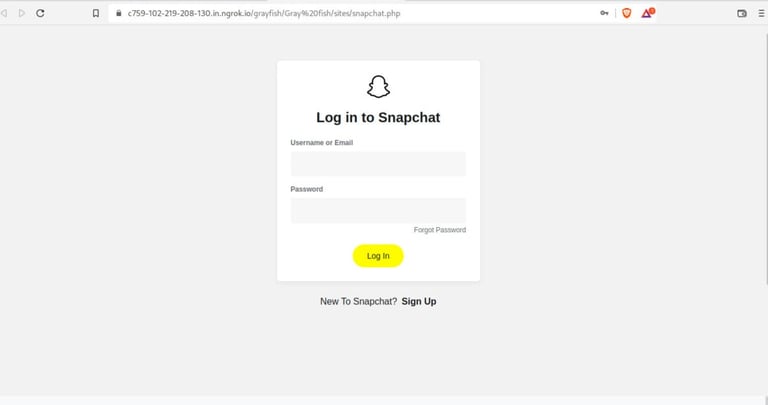
Step-7: Seeing captured credentials
The phishing victim is required to provide Snapchat login details on the Snapchat phishing page. Once the login credentials are submitted, we can view them on grayfish administration page as shown below. The login details include; the username or email, user password and the site used to phish the details.
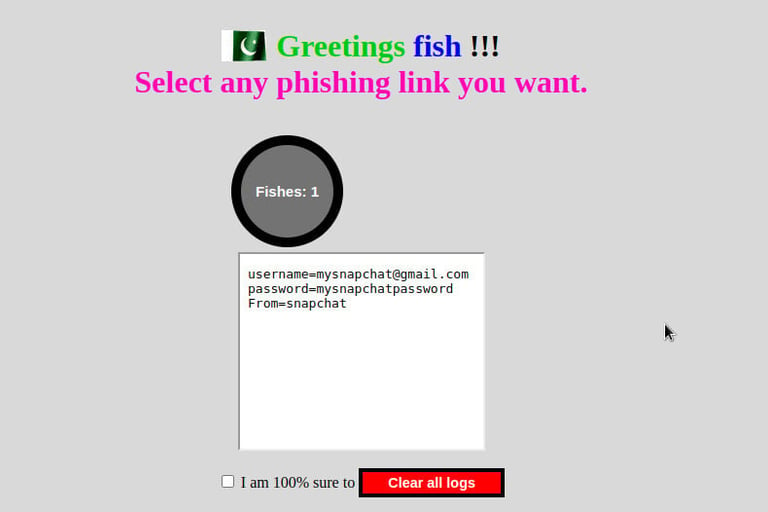
The main takeaway from the Snapchat phishing guide is that we all need to be better at spotting and avoiding fake websites. Over the years, phishing continues to be a major threat around the world. Many people are still falling victim to phishing methods that have been used over a long period of time. Protecting yourself from phishing attacks is an individual responsibility.s
The only way to protect yourself from Snapchat phishing is to only log in to Snapchat using the official app. If you are ever unsure if a website is really the official website, use the official app instead. This will help you avoid being tricked into sending your information.
