Russian government software has been tampered with to distribute the Konni RAT malware.
The installer for a tool believed to be utilized by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been compromised to distribute a remote access trojan known as Konni RAT (also referred to as UpDog).
BLOGS


The installer for a tool believed to be utilized by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been compromised to distribute a remote access trojan known as Konni RAT (also referred to as UpDog).
These findings have been reported by a German cybersecurity firm, DCSO, which has identified the activity as originating from actors associated with the Democratic People's Republic of Korea (DPRK), targeting Russia.
The Konni activity cluster, also known as Opal Sleet, Osmium, or TA406, has a history of deploying the Konni RAT against Russian entities. The threat actor has been linked to attacks on the MID since at least October 2021.
In November 2023, Fortinet FortiGuard Labs disclosed the use of Russian-language Microsoft Word documents to distribute malware capable of harvesting sensitive information from compromised Windows systems.
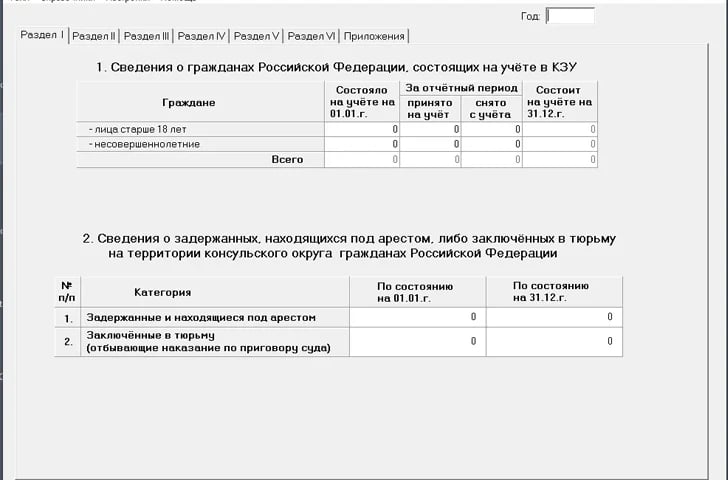
Based on the installation paths, file metadata, and user manuals included in the installer, it is apparent that the software is designed for internal use within the Russian Ministry of Foreign Affairs (MID). Specifically, it facilitates the transmission of annual report files from overseas consular posts (known as КЗУ — консульские загранучреждения) to the Consular Department of the MID through a secure channel.
The tampered installer is in the form of an MSI file. Upon execution, it triggers a sequence of infection to establish communication with a command-and-control (C2) server, where it awaits further directives.
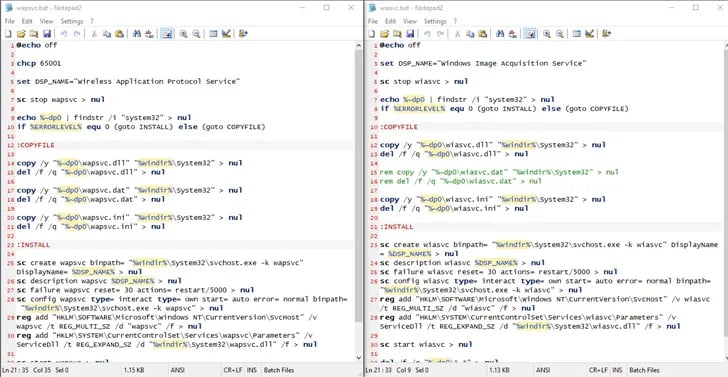
The remote access trojan, equipped with capabilities for file transfers and executing commands, is believed to have been utilized as early as 2014. It has also been attributed to other North Korean threat actors, including Kimsuky and ScarCruft (also known as APT37).
The method by which the threat actors acquired the installer, which is not publicly available, remains unclear. However, it is suspected that the extensive history of espionage operations targeting Russia may have aided in identifying potential tools for future attacks.
While North Korea's targeting of Russia is not unprecedented, this development coincides with an increasing geopolitical closeness between the two countries. State media from North Korea recently reported that Russian President Vladimir Putin gifted leader Kim Jong Un a luxury Russian-made car.
DCSO noted, "To some extent, this shouldn't come as a surprise; the deepening strategic relationship wouldn't necessarily eliminate existing North Korean intelligence needs. There's still a continued necessity for North Korea to assess and verify Russian foreign policy planning and objectives."
