Reverse Engineering Malware with strings and PEiD
BLOGS
When a suspicious .exe file lands in a forensic analyst's lap, the first question is: what does it do? Before detonating the sample in a sandbox, analysts often run quick static checks to extract basic intel. Tools like strings and PEiD provide a lightweight way to peek inside the file — without actually executing it. These tools help uncover hardcoded URLs, error messages, registry paths, and even indicators of packing or obfuscation. It's a first step that can often give away the malware's purpose. And it takes just a few seconds to get started.
strings scans the binary for readable ASCII and Unicode text, helping analysts pull out everything from hardcoded IPs to embedded scripts. If the malware contacts a C2 server, uses an internal username, or displays fake error messages, they’ll usually appear in the output. For instance, running strings invoice.exe | grep http might instantly expose a malicious domain like malicious-domain.net/steal.php. These breadcrumbs help blue teamers prepare firewall blocks or trace further activity. You don't need to know assembly — just read. It’s like eavesdropping on a conversation inside the file.
Meanwhile, PEiD is a Windows-based utility that detects the packer or compiler used in an executable. Malware authors frequently use packers like UPX or Themida to compress and hide the real payload. By loading the file in PEiD, you might see output like “UPX packed” or “Borland Delphi” — hints about how the malware was built. This information can help you decide if unpacking is needed before deeper analysis. Some compilers also indicate the use of older malware kits or automation tools. It’s a digital fingerprint, and one that often links samples to known families.
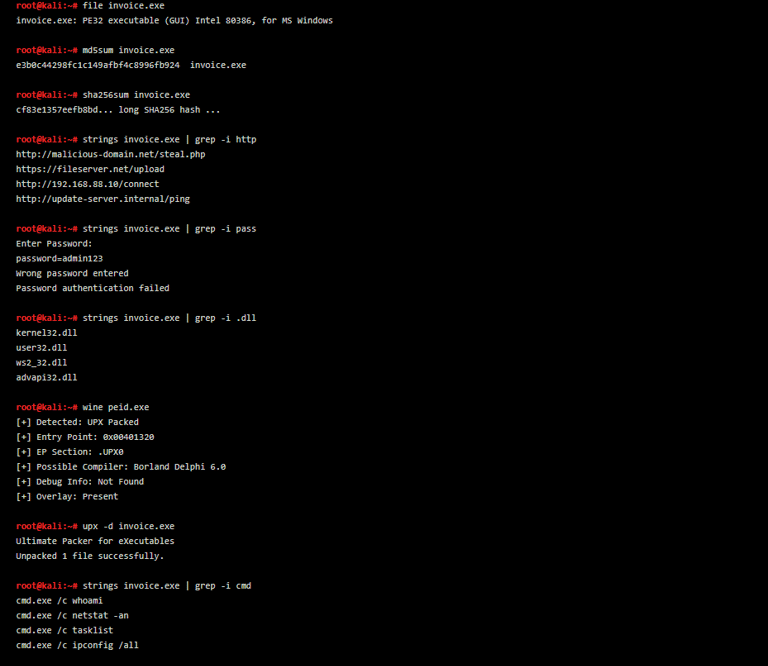
This type of analysis is especially helpful when working on live incident response. Instead of blindly executing malware, quick static techniques allow you to isolate threats without risk. They’re also great for analysts who aren’t reverse engineers but still need intel fast. Together, strings and PEiD form a powerful combo that gives clarity, speed, and control. So the next time you grab a suspicious .exe, don’t rush to run it. Open it with these tools — the malware may tell you everything you need.
