Ransomware group dumps massive collection of government employee data online
BLOGS


The Government Pensions Administration Agency (GPAA) in South Africa has become the latest victim of the ransomware group LockBit, which has a track record of targeting organizations for extortion.
LockBit issued a deadline of March 11, 2024, for the GPAA to meet their ransom demands, failing which they threatened to expose the stolen data on the dark web.
To substantiate their claim of data theft, LockBit shared a snippet of the compromised data on their dark web platform, including scans of passports belonging to senior government officials.
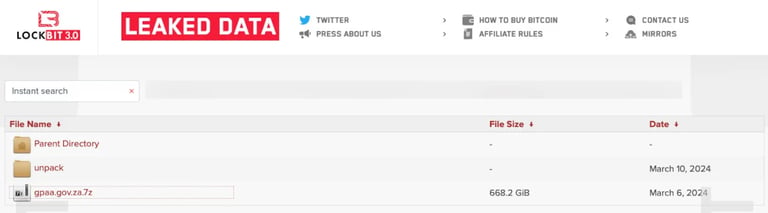
Despite the ultimatum, it seems that the GPAA opted not to comply with the ransom demands. Consequently, LockBit has proceeded to release a massive 668GB archive, allegedly containing data extracted from the agency.
LockBit operates as a cybercriminal group offering ransomware as a service (RaaS), allowing other threat actors to purchase and execute attacks. These attacks typically involve encrypting the victim's data and demanding payment, often coupled with the threat of exposing the data publicly if the demands are not met.
Recognized as one of the most prolific ransomware groups in 2022, LockBit was estimated to be responsible for 44% of all ransomware attacks worldwide in 2023.
In February 2024, MyBroadband reported a security breach at the Government Employees Pension Fund (GEPF) when an unauthorized entity attempted to access its systems.
The GEPF informed MyBroadband that its administrator, the Government Pensions Administration Agency (GPAA), had taken the precaution of shutting down the systems to contain the breach.
"While there was no outage, the systems were deliberately shut down by our administrator (GPAA) as a security measure in response to an attempted unauthorized access," stated the GEPF.
The GEPF clarified that the shutdown did not compromise their data integrity or disrupt pension payments.
However, during this period, an anonymous source informed MyBroadband that no payments had been made since February 12, 2024.
According to the source, "They are not even processing applications manually. No payments have been processed since February 12. The self-service site and call center remain inaccessible as of Wednesday, February 21, 2024."
Subsequently, the GEPF issued a statement indicating that its offices and call center were back in operation, emphasizing that no payments had been affected.
"The incident did not impact any payments, and pensioners and members will continue to receive their benefits as scheduled," the statement reassured.
The cause of the downtime was initially unclear, with the GEPF providing contradictory explanations between February 14 and 19.
Initially, the GEPF attributed the closure of its call center and walk-in center in Sunnyside, Pretoria, to technical issues. However, the subsequent day, it stated that the centers were closed due to a burst pipe causing disruptions to the water supply in its office buildings.


The GEPF initially announced that normal operations would resume on February 16, 2024, reassuring the public that all other GEPF offices and walk-in centers remained open.
However, the explanation for the outage shifted once again on Friday, February 16, when the GEPF disclosed that the GPAA's systems were offline.
"GPAA is currently unable to assist clients at our regional offices, call center, mobile offices, and co-locations with pension administration queries," the announcement stated, urging clients to refrain from visiting GEPF offices nationwide until they receive confirmation that the systems are fully functional.
In a subsequent update, the GEPF disclosed that an unauthorized attempt to access its systems had occurred, prompting them to shut down operations to contain the breach.
"The incident necessitated the GPAA to shut down all systems as part of their security measures to isolate affected areas and prevent further breaches," the GEPF stated.
Following the system shutdown, the GPAA immediately initiated measures to restore operations and prevent future incidents, while also assuring that members' personal information remained secure.
However, in light of LockBit's data release today, it seems the GEPF's reassurance may have been overly optimistic.
