Ransomware Attack Using Telegram as a C2
PROJECTS


Introduction
In this blog post, I'll explain a Python-based ransomware that can encrypt files, capture screenshots, and steal specific files—all controlled remotely through a Telegram bot. This malware runs silently in the background, making it difficult for victims to notice. It’s also added to the Windows Startup folder to ensure it runs automatically after every reboot. The goal of this blog is to showcase how ransomware operates to raise awareness about potential threats and cybersecurity.
Disclaimer: This project is for educational purposes only.
What is Ransomware?
Ransomware is a type of malware that locks or encrypts a victim's files and demands payment for their release. Attackers often use it to target personal or business data, causing significant financial and emotional damage. The Python ransomware in this project uses a Telegram bot for remote control, allowing the attacker to manage the malware from anywhere with simple commands.
Key Features of the Ransomware
This Python ransomware is packed with multiple features that allow it to perform malicious actions:
File Encryption: It encrypts files, making them unreadable without the decryption key.
Remote Control via Telegram: It can be controlled remotely using simple commands sent through Telegram.
Screenshot Capture: The ransomware can capture screenshots of the victim's screen.
File Theft: Specific files can be sent to the attacker via Telegram.
With all that being said, let's begin.
1. Ransomware Running in the Background
Once the ransomware is executed, it runs silently in the background, performing its tasks without alerting the user. This stealthy behavior ensures that the victim is unaware of the attack until it’s too late. Since the ransomware operates without any visible windows or notifications, it’s difficult for the victim to detect that something is wrong until the attack is complete.
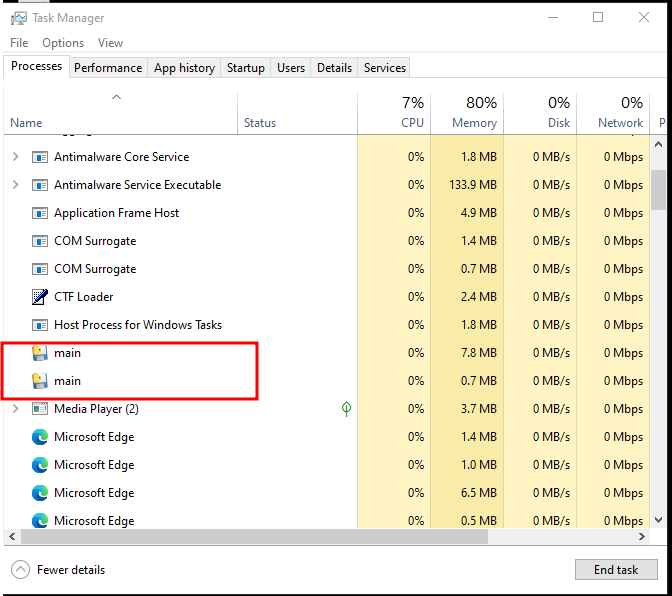
2. Ransomware Added to the Startup Folder
To make sure it remains active after the system is rebooted, the ransomware adds itself to the Windows Startup folder. This ensures that every time the victim turns on their computer, the ransomware will automatically run again. This persistence feature makes it much harder for the victim to remove the ransomware, as it is always lurking in the background after every restart..
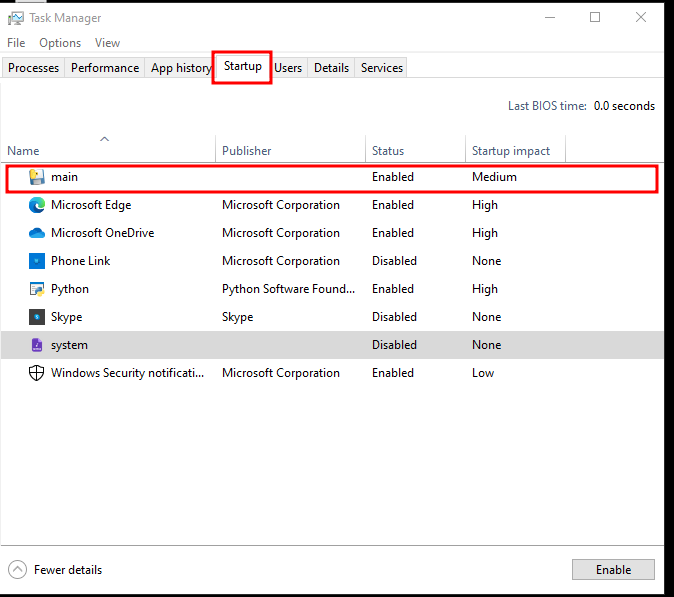
3. Controlling the Ransomware with Telegram
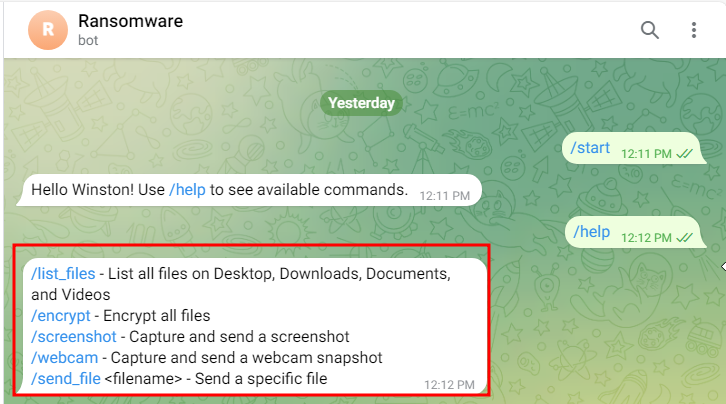
A unique aspect of this ransomware is its integration with Telegram for remote control. Once the ransomware is running, an attacker can control it via simple Telegram commands. These commands allow the attacker to encrypt files, capture screenshots, list available files, and even steal specific files from the victim's computer.
Commands Used in Telegram:
/encrypt: Encrypts the victim’s files in key directories like Desktop, Documents, and Pictures.
/screenshot: Captures a screenshot of the victim’s screen and sends it back to the attacker.
/list_files: Lists all files in certain folders (e.g., Desktop, Documents, Downloads).
/send_file [filename]: Sends a specific file from the victim’s computer to the attacker.
This is what it looks like when using Telegram to control the ransomware:
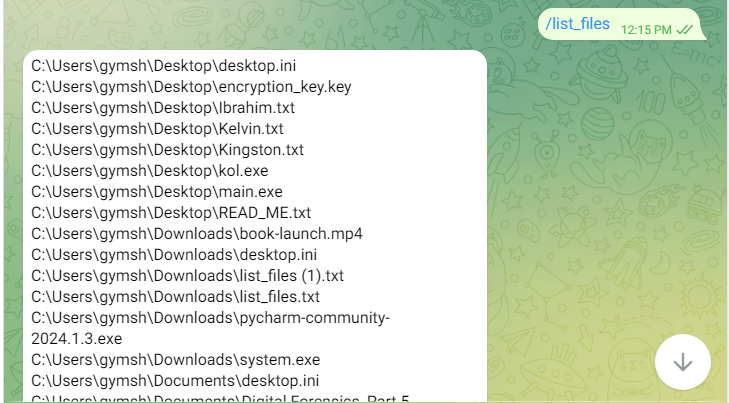
4. Listing Files with /list_files Command
The /list_files command allows the attacker to view all the files on the victim's computer in important folders such as Desktop, Documents, and Downloads. By scanning these directories, the attacker can quickly assess what valuable files are present on the system before deciding which ones to steal or encrypt. This command helps the attacker get a good overview of the victim's personal data and information.
5. Stealing Specific Files with /send_file Command
If the attacker finds a file they want to steal, they can use the /send_file [filename] command to remotely retrieve the file from the victim’s computer. This feature allows the attacker to download specific files, such as important documents, personal photos, or financial records. This is particularly dangerous as the attacker can steal sensitive information and personal data even before encrypting the victim's files, ensuring they get something valuable no matter what.
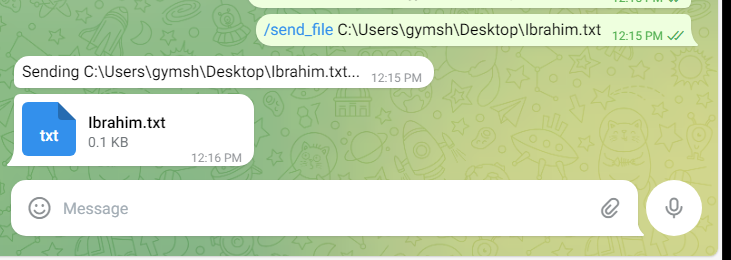
6. Encrypting Files on the Victim’s Computer
Once files have been stolen, the ransomware’s next step is to encrypt the victim's files, making them inaccessible without the decryption key. When the /encrypt command is issued, the ransomware searches for important files (e.g., .docx, .pdf, .jpg) and encrypts them using a secure encryption algorithm. After the files are locked, a ransom note is placed on the victim's desktop. This note informs the victim that their files have been locked and provides instructions on how to recover them—usually by paying a ransom.
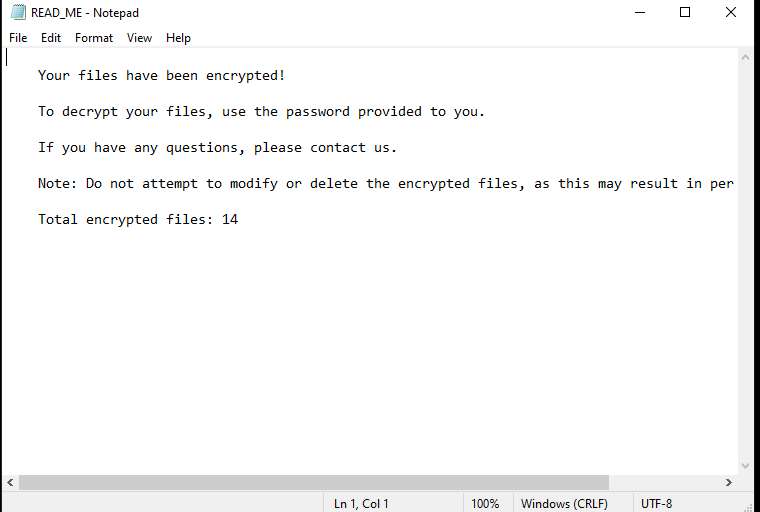
7. Viewing the Encrypted Files
After the ransomware has encrypted the files, they become unreadable and inaccessible to the victim. The encrypted files are now locked in a format that requires the correct decryption key to unlock. The victim will notice that their files can no longer be opened, and they are effectively unusable until the ransom is paid or the decryption key is provided.
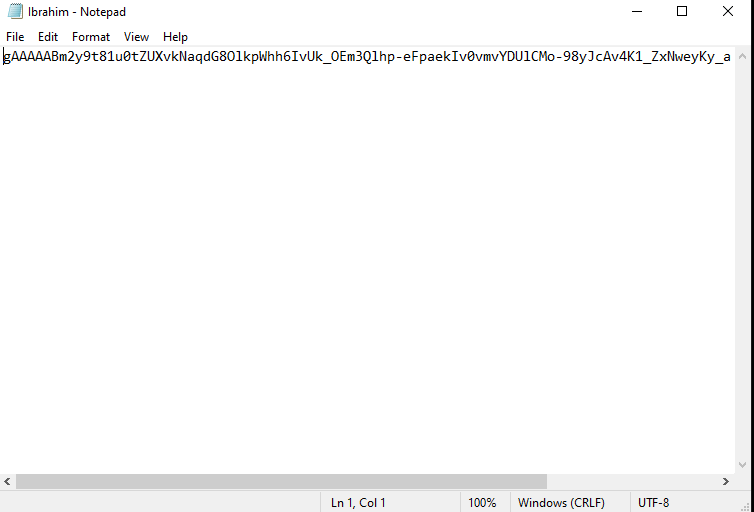
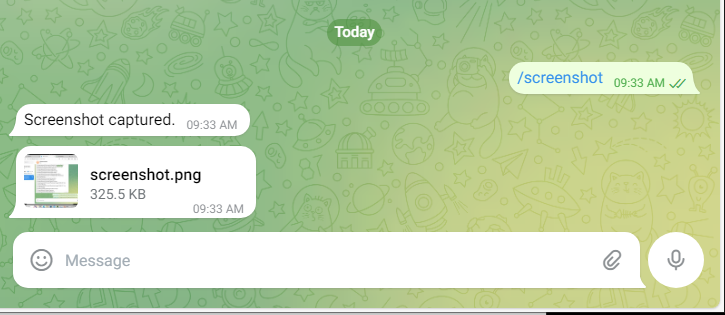
8. Capturing Screenshots Remotely with /screenshot Command
The /screenshot command allows the attacker to remotely take a screenshot of the victim’s computer screen and send it back to the Telegram chat. This can be used to spy on the victim's activities, such as checking what they are working on or viewing sensitive documents. By capturing screenshots, the attacker can gather real-time information about what the victim is doing on their computer.
9. Decrypting Files After Payment
If the victim agrees to pay the ransom or receives the decryption key, they can use a separate decryptor executable to unlock their encrypted files. The decryptor scans the system for encrypted files and uses the key to restore them to their original state. Once the decryption is complete, the files will be accessible again.
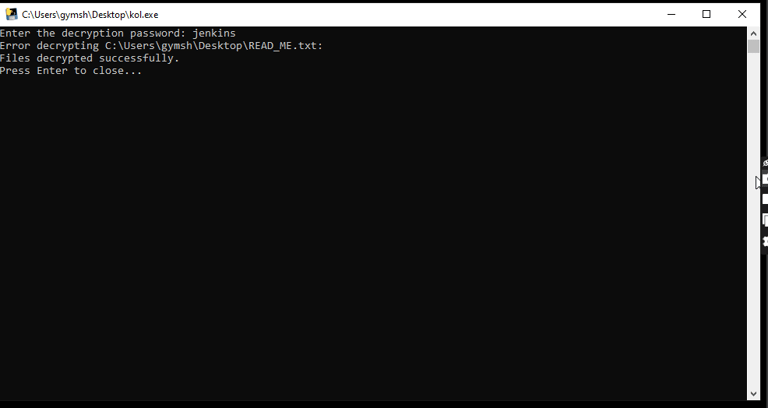
Note: The script failed to decrypt READ_ME.txt which contained the ransomware note because it was never encrypted.
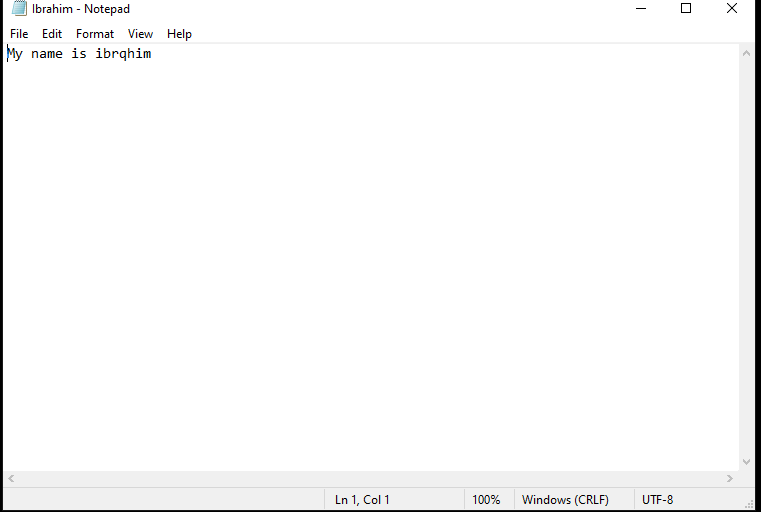
10. Viewing Decrypted Files
After running the decryptor, the files that were previously encrypted are restored to their original form and become usable again. The victim will be able to access and open the files just as they did before the attack.
Conclusion
This Python-based ransomware, controlled via a Telegram bot, demonstrates how easily a system can be compromised using simple, well-known techniques. By running silently in the background and ensuring persistence through the Startup folder, this malware can cause significant damage before the victim realizes what's happening. Understanding how ransomware works and taking steps to secure your system is essential for protecting against these types of attacks.
Key Takeaways:
Back Up Your Data: Regular backups can save you from losing your files in a ransomware attack.
Beware of Suspicious Software: Avoid running untrusted programs, especially from unknown sources.
Stay Informed: Knowing how ransomware works can help you protect your systems from being compromised.
By following these steps and staying vigilant, you can significantly reduce the risk of becoming a ransomware victim.

