Pegasus, Femtocells, and Stingrays: How Hackers Exploit Them to Infect Targets
BLOGS


Pegasus malware is one of the most sophisticated and alarming pieces of spyware ever created. Developed by the NSO Group, Pegasus is capable of infiltrating smartphones to extract sensitive information, monitor activities, and even control device functionalities. This malware has evolved significantly over time—from requiring user interaction to infect devices to achieving infection without any user action at all.
To understand the full impact of Pegasus, we must also explore the tools and methodologies that hackers use to deliver it. Two critical technologies—femtocells and stingrays—play a pivotal role in these operations. These tools allow attackers to compromise their targets’ devices with precision.
What Is Pegasus Malware?
Pegasus was first discovered in 2016 when Ahmed Mansoor, a human rights activist, received suspicious text messages. Upon investigation, researchers uncovered a zero-day exploit chain that could jailbreak an iPhone remotely and install spyware. Initially, Pegasus required the victim to click on a malicious link for infection, but its later iterations became far more advanced, eliminating the need for user interaction.
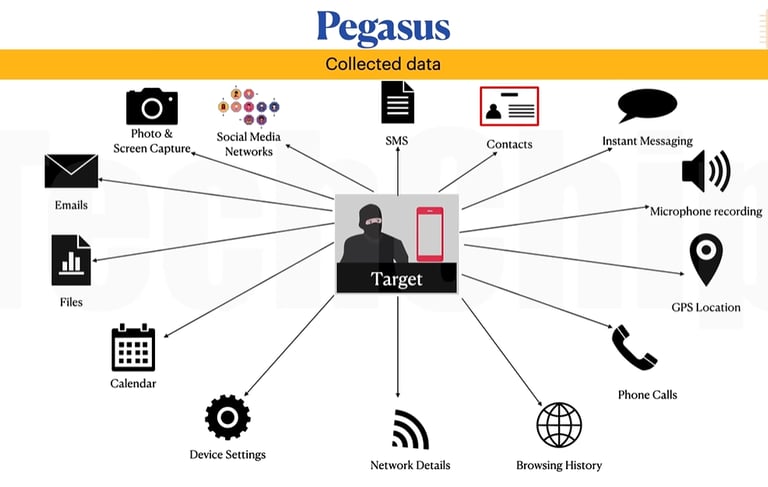
How Pegasus Has Evolved
Initial Version: The first version of Pegasus required user interaction. Victims needed to click on a link that directed them to a malicious website. Once clicked, the website exploited vulnerabilities in the device’s operating system, allowing Pegasus to be installed secretly.
Zero-Click Exploits: Later versions refined the attack vectors, enabling zero-click exploits. Pegasus could now infect devices through a simple missed call on messaging apps like WhatsApp or via malicious image files sent through SMS. This development marked a chilling evolution in malware sophistication.
Femtocells and Their Role in Targeting
Femtocells are small cellular base stations used to enhance mobile signal strength in limited areas. While their legitimate purpose is to improve connectivity, attackers can exploit femtocells to intercept and manipulate communication between a target’s device and cellular networks.
How Hackers Exploit Femtocells:
Interception: Hackers set up a rogue femtocell in the vicinity of the target. The femtocell captures all communications, including SMS and calls.
Injection: Using the captured data, attackers inject malicious payloads, such as Pegasus, into the communication stream. This allows for remote installation of spyware without the target’s awareness.


Stingrays: Surveillance on Steroids
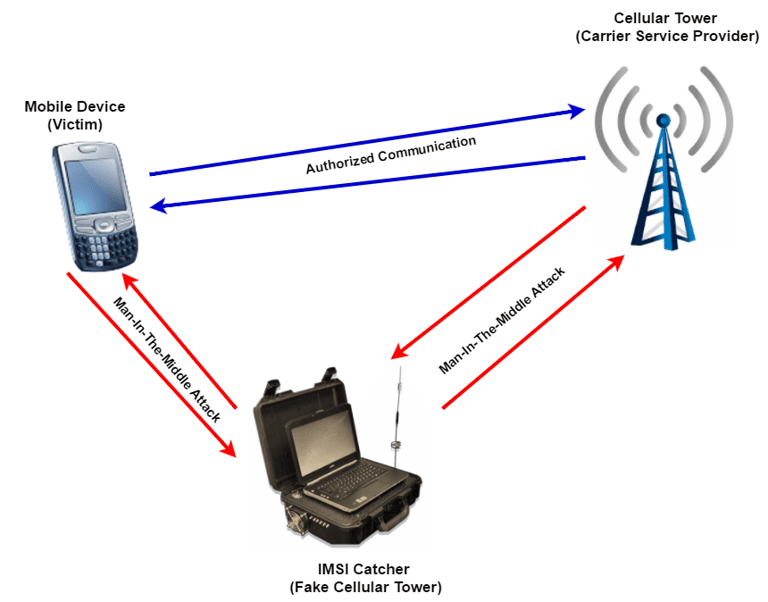
Stingrays, also known as IMSI catchers, are devices that mimic legitimate cell towers. They force nearby mobile devices to connect to them instead of genuine towers. Originally designed for law enforcement, stingrays are now used maliciously by hackers to exploit vulnerabilities in mobile networks.
How Hackers Use Stingrays:
IMSI Catching: Stingrays identify and track specific devices by capturing their International Mobile Subscriber Identity (IMSI).
Man-in-the-Middle Attacks: They intercept and manipulate data packets sent between the device and the network.
Spyware Delivery: Attackers use the stingray’s proximity to the target to push Pegasus onto the device, exploiting its capabilities for seamless infection.
The Evolution of Infection Without Interaction
The ability of Pegasus to infect devices without user interaction represents a significant leap in spyware technology. Zero-click attacks leverage flaws in widely used applications, such as messaging platforms, to execute code remotely. These vulnerabilities allow Pegasus to:
Access device microphones and cameras.
Retrieve stored passwords.
Extract call logs, messages, and photos.
The Broader Implications
The combination of Pegasus, femtocells, and stingrays has raised alarms worldwide about the state of mobile security. These technologies highlight the vulnerabilities in existing systems and emphasize the importance of proactive cybersecurity measures. Governments, activists, journalists, and even ordinary citizens are at risk of surveillance.
How to Protect Yourself
Keep Devices Updated: Regular updates often patch known vulnerabilities.
Use Encrypted Communication Apps: Choose apps with strong end-to-end encryption.
Be Cautious with Links: Avoid clicking on links from unknown sources.
Monitor Your Device: Watch for unusual activity, such as rapid battery drain or overheating.
Conclusion
Pegasus, combined with tools like femtocells and stingrays, demonstrates the dangerous intersection of malware and hardware exploitation. Its progression from requiring user interaction to zero-click attacks highlights the evolving sophistication of cyber threats. Understanding these tools and techniques is essential for defending against them and preserving privacy in an increasingly connected world.
