New Wi-Fi Vulnerabilities Expose Android and Linux Devices to Hackers
Cybersecurity researchers have identified two authentication bypass flaws in open-source Wi-Fi software found in Android, Linux, and ChromeOS devices that could trick users into joining a malicious clone of a legitimate network or allow an attacker to join a trusted network without a password.
BLOGS


Cybersecurity researchers have uncovered two authentication bypass vulnerabilities in open-source Wi-Fi software utilized by Android, Linux, and ChromeOS devices. These flaws, identified as CVE-2023-52160 and CVE-2023-52161, were found during a security assessment of wpa_supplicant and Intel's iNet Wireless Daemon (IWD), respectively.
According to Top10VPN's research, conducted in collaboration with Mathy Vanhoef, who has previously discovered Wi-Fi vulnerabilities such as KRACK, DragonBlood, and TunnelCrack, these vulnerabilities could allow attackers to deceive users into connecting to malicious networks or gain unauthorized access to secure networks without a password.
CVE-2023-52161 specifically enables unauthorized access to protected Wi-Fi networks, potentially exposing users and devices to malware infections, data theft, and business email compromise (BEC) attacks. It affects IWD versions 2.12 and below.
Meanwhile, CVE-2023-52160 impacts wpa_supplicant versions 2.10 and earlier and is considered more critical because it is the default software used in Android devices for handling wireless network login requests.
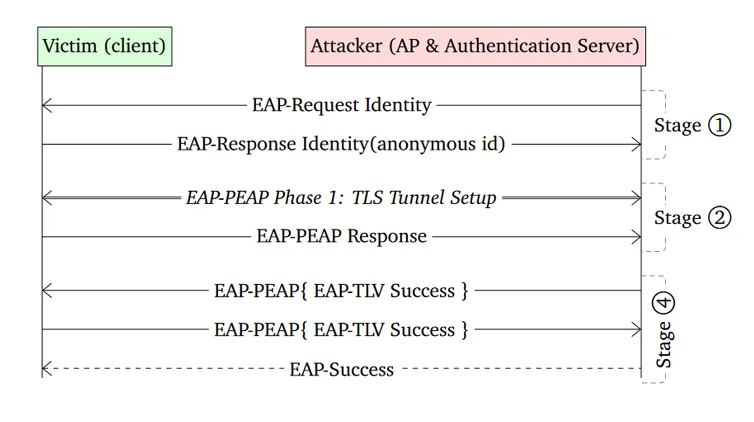
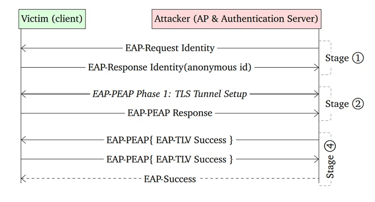
That said, it only impacts Wi-Fi clients that aren't properly configured to verify the certificate of the authentication server. CVE-2023-52161, however, affects any network that uses a Linux device as a wireless access point (WAP).
Exploiting CVE-2023-52160 hinges on the attacker possessing the SSID of a Wi-Fi network previously connected to by the victim and being physically close to them.
One conceivable scenario involves the attacker scanning for networks while walking around a company's premises before targeting an employee leaving the office, as stated by the researchers.
Several major Linux distributions, including Debian, Red Hat, SUSE, and Ubuntu, have issued advisories regarding these vulnerabilities. While the wpa_supplicant issue has been addressed in ChromeOS versions 118 and beyond, fixes for Android are still pending.
In the interim, it's crucial for Android users to manually configure the CA certificate of any saved enterprise networks to thwart potential attacks, advises Top10VPN.
