New DEEP#GOSU Malware Campaign Targets Windows Users with Advanced Tactics
BLOGS
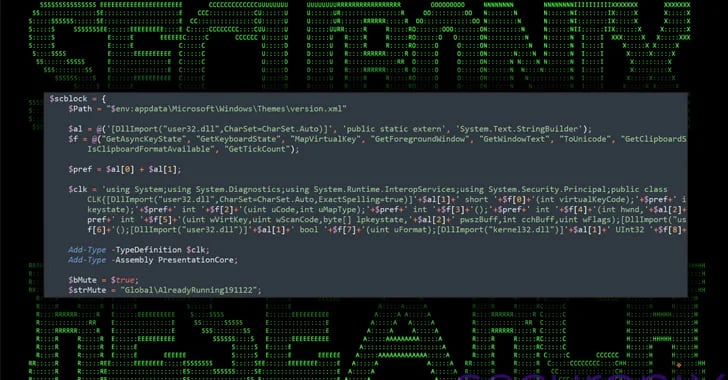
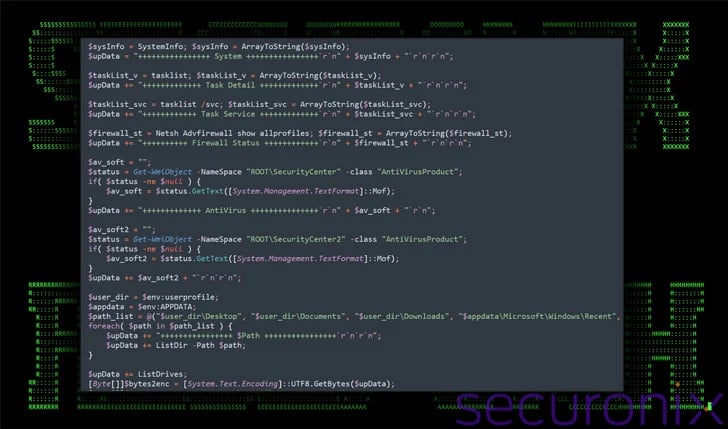
A newly detected sophisticated attack campaign, named DEEP#GOSU by cybersecurity firm Securonix, is believed to be linked with the North Korean state-sponsored group known as Kimsuky. The campaign utilizes PowerShell and VBScript malware to infect Windows systems and gather sensitive data. Notably, the malware employs various techniques including keylogging, clipboard monitoring, dynamic payload execution, and data exfiltration. It utilizes legitimate services like Dropbox or Google Docs for command-and-control (C2) purposes, allowing the threat actor to evade detection within regular network traffic. The attack starts with a malicious email attachment containing a disguised ZIP archive with a rogue shortcut file (.LNK) posing as a PDF file ("IMG_20240214_0001.pdf.lnk"). This .LNK file contains a PowerShell script and a decoy PDF document, with the script connecting to an actor-controlled Dropbox infrastructure to retrieve and execute additional PowerShell and VBScript scripts. The retrieved scripts further fetch a .NET assembly file from Dropbox, which acts as a remote access trojan (TruRat) capable of recording keystrokes and facilitating remote control. Additionally, a VBScript retrieved from Dropbox is used to execute arbitrary VBScript code, including another PowerShell script, and to set up scheduled tasks for persistence using Windows Management Instrumentation (WMI).
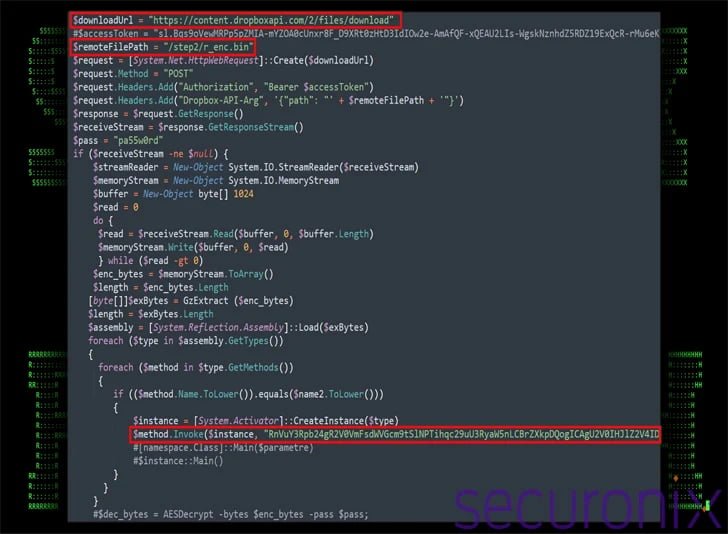
Another significant aspect of the VBScript is its utilization of Google Docs to dynamically obtain configuration data for the Dropbox connection, enabling the threat actor to modify account information without altering the script itself.
The PowerShell script retrieved as a result is designed to collect comprehensive system information and transmit it via a POST request to Dropbox. According to researchers, this script serves as a means for periodic communication with a command-and-control (C2) server through Dropbox, with its primary functions including data encryption, exfiltration, or downloading.
Essentially, it functions as a backdoor to manage compromised hosts and continuously log user activity, encompassing keystrokes, clipboard contents, and active window details.
This development coincides with security researcher Ovi Liber's revelation of ScarCruft, a North Korea-linked group, embedding malicious code within Hangul Word Processor (HWP) lure documents in phishing emails to disseminate malware such as RokRAT.
Liber revealed that the email includes an HWP Doc containing an embedded OLE object in the form of a BAT script. When clicked, the OLE object executes the BAT script, triggering a PowerShell-based reflective DLL injection attack on the victim's machine.
Additionally, Andariel recently exploited the legitimate remote desktop solution MeshAgent to deploy malware like AndarLoader and ModeLoader, both JavaScript malware intended for command execution. This marks the first confirmed use of MeshAgent by the Andariel group, which has a history of leveraging asset management solutions for malware distribution.
Andariel, a sub-cluster of the infamous Lazarus Group, is known for orchestrating cyber espionage and financial gain attacks. Recently, it was observed laundering a portion of stolen crypto assets from the HTX exchange hack through Tornado Cash, following common crypto-laundering patterns.
Despite sanctions, Tornado Cash's continued operations have made it an appealing option for the Lazarus Group to conceal their transaction trail, particularly after the shutdown of Sinbad in November 2023. As a decentralized mixer, Tornado Cash operates through smart contracts on decentralized blockchains, making it immune to seizure and shutdown.
