Lockphish V2.0 PIN phishing attack
SOCIAL ENGINEERING

Many devices use a PIN to protect user privacy. In this guide, we will use the Lockphish tool to phish for PIN locks on various target operating systems. Lockphish is the first tool to use an HTTPS link to phish for unlock credentials on different operating systems, including Android, Windows, and iOS. The attack is delivered to the victim using Ngrok tunneling, which also facilitates the delivery of captured credentials. Lockphish automatically captures the victim's IP address.
Key features of Lockphish include:
- Automatic Device Recognition: Lockphish detects the target device and displays the appropriate PIN request page automatically. Users do not need to select the operating system of the target device when launching the attack.
- IP Tracker: Lockphish captures the target’s IP address, which is crucial for further information gathering.
- Ngrok Tunneling: Ngrok is used to port forward, allowing the attack to be launched over the internet and the captured credentials to be delivered back.
- Pre-made Phishing Websites: Lockphish includes pre-made phishing pages for Android, iOS, and Windows lock screen.
Note: This guide has been made for educational purposes only. The authors will not be held responsible for any damages.In this guide, we will be launching attacks on all the mentioned devices. i.e. android and windows devices.
Step 1: Installing lockphish
To ensure no errors while installing lockphish, we will first update the pre-installed packages on the running instance using the below command.
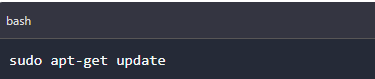
After the update is complete, we will now download lockphish tool from its official GitHub repository. We can either download the tool as a zip file or clone from GitHub using the below command.
Step 2: Running lockphish
If you downloaded the zip file, you need to first extract the files using the command


After unzipping we move into the directory so that we can launch our pin code phishing attack.


To run lockphish we first need to give the lockphish.sh file permission to execute as root on the system. We will use the below command.
We can now generate our attacking link by running the file using the command.

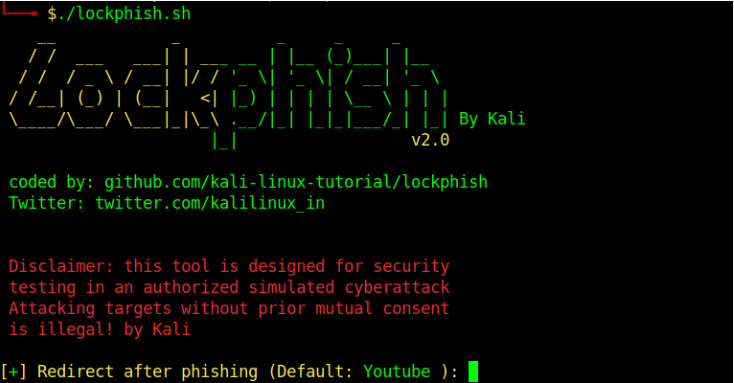
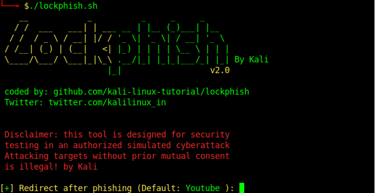
Before launching an attack , you are required to specify the link to which the victim will be redirected after providing the attacker with the PIN to their devices. For our case, we will be using the default redirect page on our attack hence we just click enter to start to generate the phishing link. Lockphish will first download Ngrok if it is not installed and automatically launch the attack. A phishing link to send to the target will be provided.
In our case, the phishing link was not displayed on the terminal. We have to open the Ngrok webpage on “localhost:4040” to get our phishing link as shown on the below image.
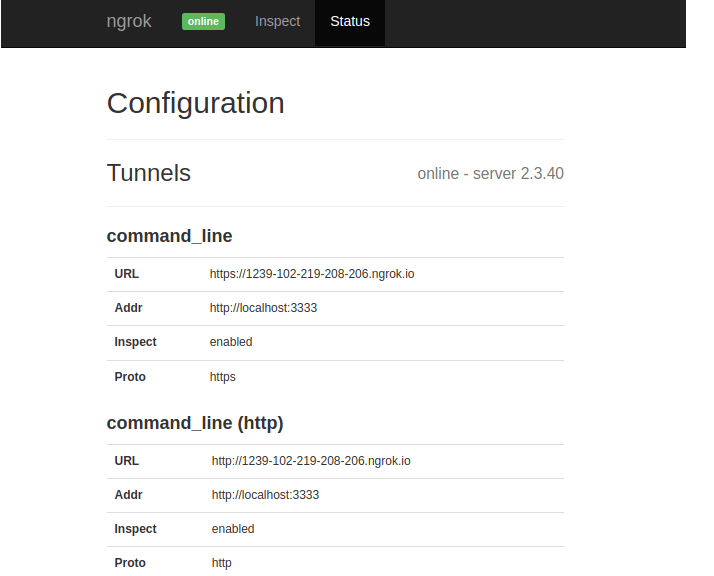
Step 3: Sending phishing link to the victim
Now we have to send the phishing link to the target, we need to employ some of the social engineering tactics to lure our victims into clicking the phishing link. Once the user clicks on the link, he/she will be taken to a page where he/she will be needed to click in order to view the YouTube video. When the link is opened a lock screen appears depending on the device requiring the user to provide his/her PIN. An extra step is included at the end of this guide on how to send the phishing link using an email to our targets.
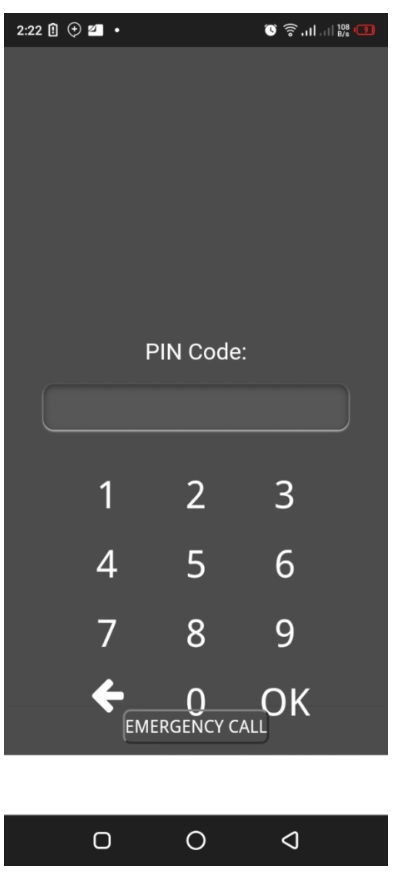
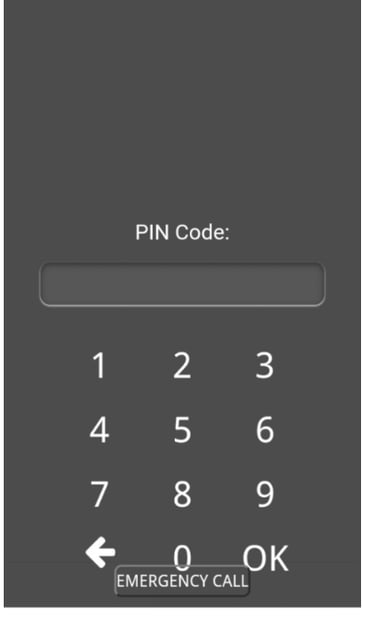
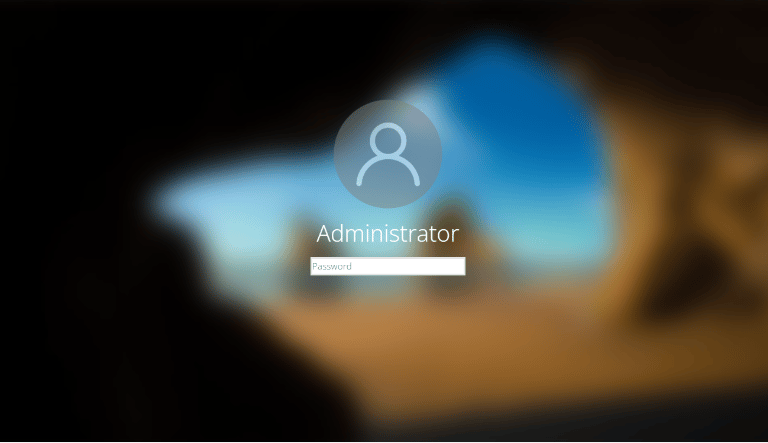

Step 4: Getting the captured PIN
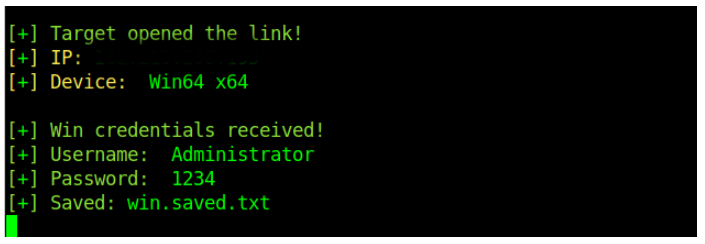
After the PIN has been provided by the victim, we can be able to view it from our lockphish terminal. Lockphish will capture the user credentials such as the PIN, the operating system of the target and the target’s IP address. A hacker is now able to use the PIN code he/she acquired using lockphish. An example of the captured credentials is as shown on the image below.
Lockphish page on android device
Lockphish page on a windows machine
Extra step: Sending phishing email using social engineering
On our extra step we will learn on how to use a free online email service to send a phishing email to our target. We will embed the phishing link we generated to an email we will send to the victim. As we learned earlier, emails can be spoofed easily to look like they come from a legitimate source. In this step we will use a free tool (emkei.cz) available online to send the email. We open the webpage and everything required is on the home page as shown below.
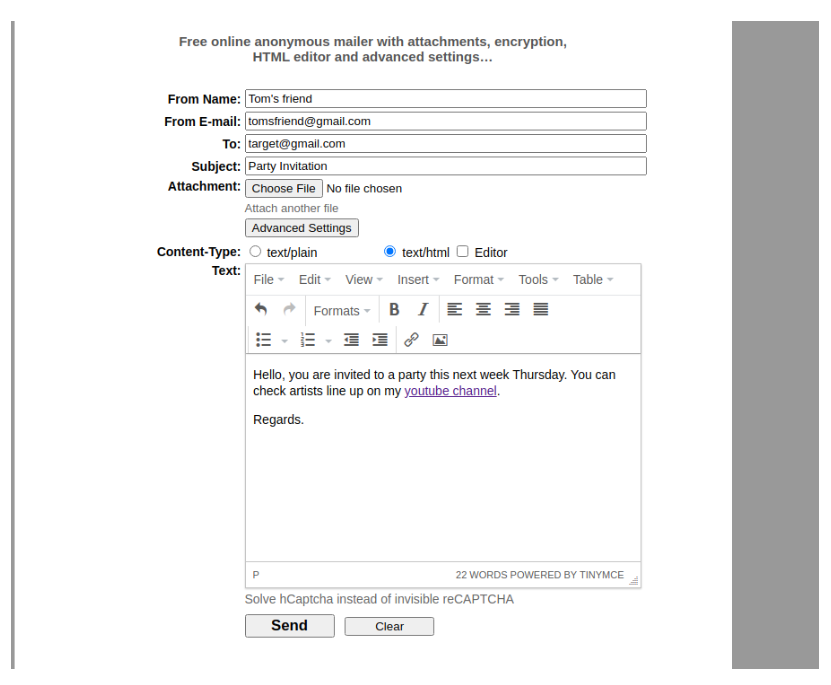
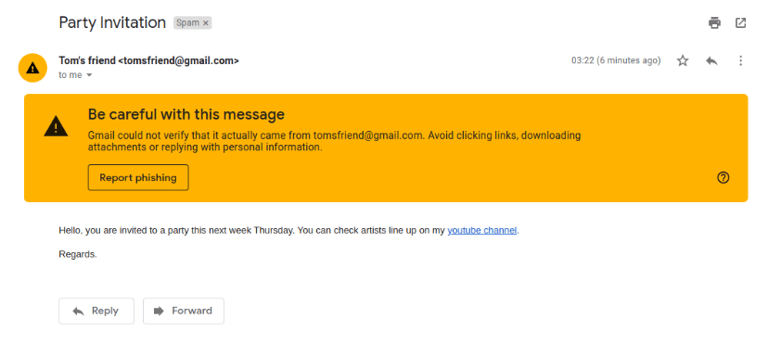
The user received an email in his spams folder as shown on the screenshot below. Once the user clicks on the link he/she will be redirected to the PIN phishing email. As you can see, the email has already been flagged as a spam since it contains the malicious link and also has been sent from a spoofed email.