I Performed a DDoS Attack Using a Botnet
PROJECTS
As part of a professional cybersecurity engagement, I recently carried out a real-world, authorized Distributed Denial-of-Service (DDoS) to evaluate the resilience of a web server infrastructure under traffic stress. This was not a theoretical or sandboxed exercise — it was a live test conducted with full permission, designed to measure how a production-like environment would respond under sustained attack conditions.
With the growing frequency of DDoS attacks in both scale and sophistication, this type of exercise is critical for organizations seeking to understand their vulnerabilities and plan effective mitigation strategies.
Why Perform a DDoS Attack?
Many organizations rely heavily on the availability of their digital services. Yet few have ever tested how their systems respond when bombarded by large volumes of traffic. The goal of this exercise was to:
Observe how the server handled high concurrent HTTP requests
Identify performance bottlenecks under load
Test auto-recovery mechanisms after a traffic spike
Improve incident response protocols
Because this was a legally sanctioned test, every part of the test was executed within scope, with safety, ethics, and transparency as top priorities.
How the exercise Was Conducted
The engagement was composed of three coordinated components, all developed and deployed specifically for this test:
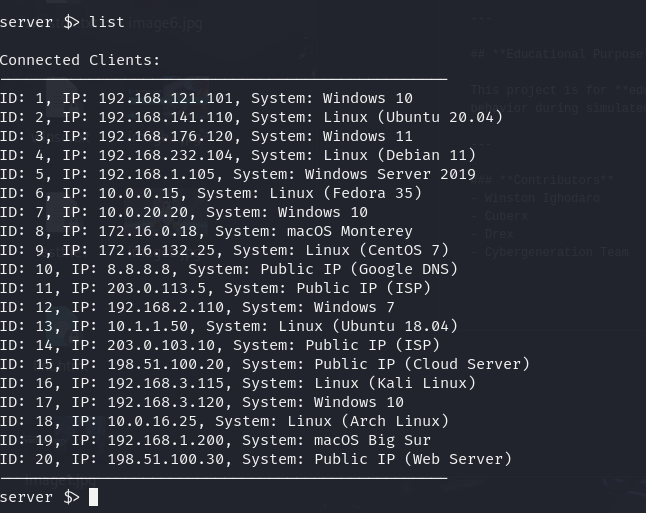
1. Client Network (Botnet)
To successfully carry out the exercise, I created a distributed set of client nodes — of different machines ranging from Windows Servers to IoT Devices a unique user with distinct IP addresses and system details. These clients sent legitimate HTTP requests at scale, with the aim of bringing down the site.
2. Command & Control Server
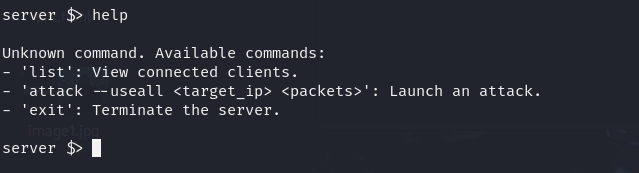
A central control script managed the clients and orchestrated the simulation. From here, I could:
View the status and details of each client
Launch synchronized attacks with precise packet counts
Monitor progress and output in real time
For example:
attack --useall 192.168.1.200 100
This command would trigger 100 coordinated requests from all clients to the target’s website.
3. Target Website
The target server was a professionally built production website. It featured typical business-facing pages such as:
Home (/)
About (/about)
Services (/services)
Contact (/contact)
But apparently the developers weren't worried about the site's security when they made the site.
Key Outcomes
The engagement provided valuable, actionable insights:
✅ Confirmed the point at which the server became unresponsive
✅ Successfully shut down the site
✅ Measured request handling performance under stress
✅ Identified areas for load balancing and traffic filtering improvements
Ethical Considerations
This simulation was conducted legally, ethically, and with explicit written permission from the infrastructure owner. No third-party systems or services were affected.
Conclusion
In cybersecurity, prevention is critical — but so is preparedness. By performing a real-world DDoS attack in a controlled, authorized context, I was able to provide clear visibility into system behavior under attack. These insights are now being used to improve the architecture, enhance failover mechanisms, and strengthen the organization's ability to withstand future threats.