I Built a Python-Based Phishing Script for Security Awareness
PROJECTSBLOGS


Phishing remains one of the most common attack vectors in cybersecurity — not because it's technically advanced, but because it works.
As part of a recent red team exercise / security awareness project, I worked on a Python-based phishing toolkit designed to execute real-world phishing campaigns within an organization.
This blog will walk through the techniques used, challenges faced, and how the tool was able to bypass spam filters and land directly in user inboxes.
Features of the Script
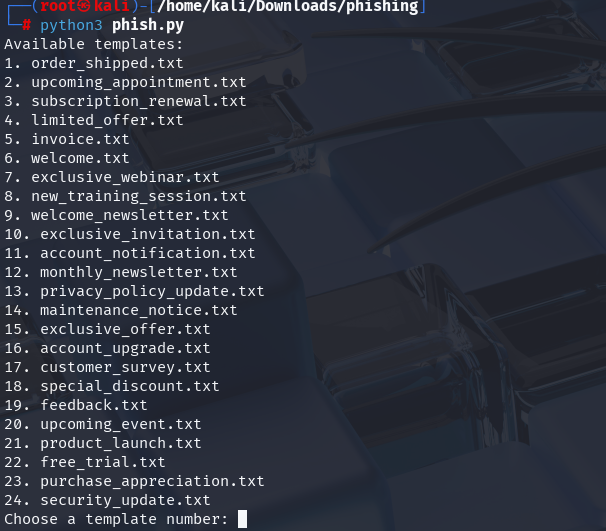
1. Template Engine
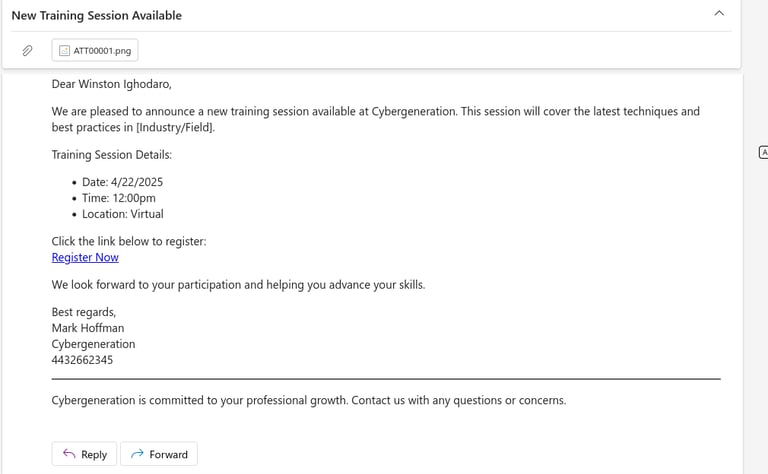
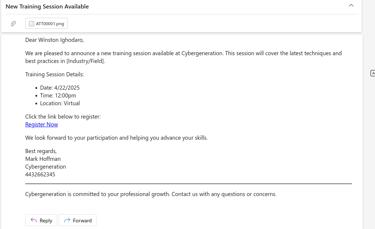
The script allows operators to choose from over 20 phishing email templates, such as:
Fake password reset notifications
Fake invoice emails
Event registration emails
Security alert emails
HR policy updates
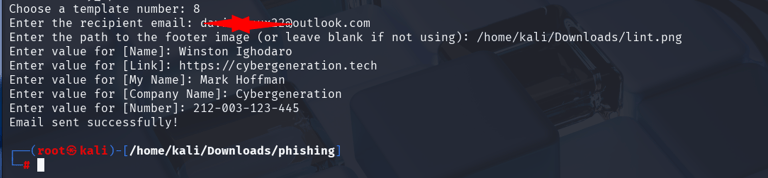
Templates are customizable for:
Sender name
Recipient name (if you know it)
Companies name
Companies phone number (one you have control over).
Hidden malicious link (behind anchor text like "Register Now" or "View Document").
2.Spam Filter Evasion Techniques
To increase the delivery success rate (into inbox, not spam), the script uses several techniques:
Randomized email headers
Customizable "from" fields
Use of legitimate-looking domains for links (with hidden redirects)
Clean HTML formatting
Avoiding common phishing keywords (like "urgent", "click immediately", etc.)
3. Link Obfuscation
Instead of showing the raw malicious URL, links were embedded behind clean anchor text.
Ethical Reminder
Phishing is dangerous. This project was for education, awareness, and security testing only.
Organizations should use phishing simulations to:
Train employees to spot suspicious emails
Improve reporting habits
Strengthen security culture
