How to use SpiderFoot
Blog post description.
INFORMATION GATHERING


Introduction to Spiderfoot:
Spiderfoot is a robust and versatile open-source reconnaissance tool designed to gather intelligence about a target. It streamlines various OSINT (Open-Source Intelligence) tasks, making it indispensable for security professionals and penetration testers.
One of Spiderfoot's key strengths lies in its ability to collect information from a diverse array of sources. From search engines and social media platforms to WHOIS and DNS records, Spiderfoot can extract a wealth of data with minimal effort. Moreover, its modular architecture allows users to tailor search modules to their specific requirements, enhancing its efficacy.
Another standout feature of Spiderfoot is its user-friendly interface. Intuitive and accessible, the interface offers multiple result formats, including HTML, CSV, and JSON, facilitating easy sharing and integration with other tools.
Spiderfoot can collect information about various targets, including:
- Domain names
- IPv4 and IPv6 addresses
- Sub-domains/Hostnames
- Subnets
- Bitcoin addresses
- Email addresses
- Phone numbers
- Usernames
- Official names
- Network ASN (Autonomous System Number)
Requirements:
- Active internet connection
- Kali Linux installed on a PC (Virtualbox installation is an option)
- Docker installed on the PC
Installation of SpiderFoot:
In this guide, we'll utilize Docker to set up Spiderfoot. Begin by downloading the tool from its GitHub repository using the command provided below.
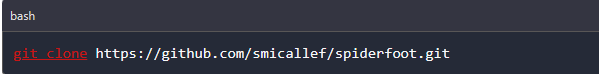
git clone https://github.com/smicallef/spiderfoot.git
We then navigate into the newly created folder containing the tool’s files and using the dockerfile supplied with Spiderfoot, we create an image that will be used to run the container using the below command.
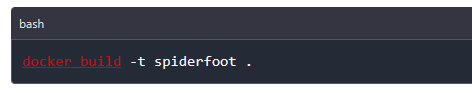
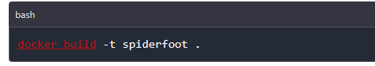
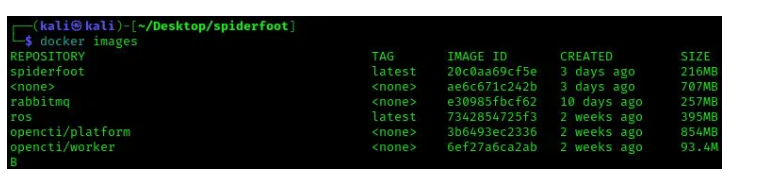
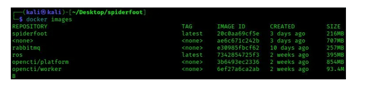
Once the image creation is over, we can check if the image has been created by running the below command. As shown in the image below, we can see Spiderfoot image has been created.


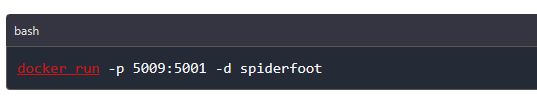
In order to connect to it from outside the container, we need to map a port on the server that runs the container to that port using the below command. The -p argument will achieve that. As you can see we are mapping port 5009 here on the local server to port 5001 which is the port Spiderfoot is listening to within the container.
After mapping the tool successfully we can connect to it via the port as shown below.
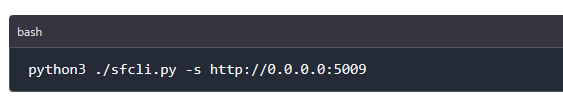
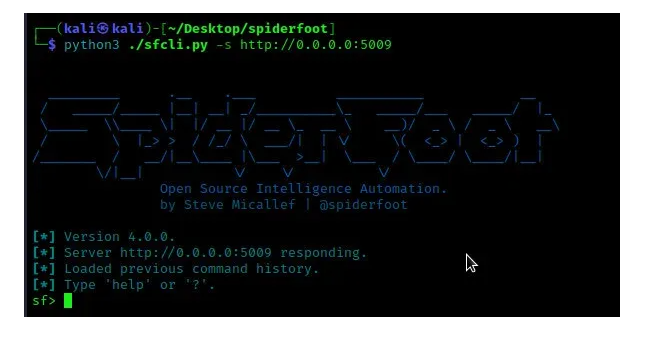
After connecting, we can use our favourite web browser to access Spiderfoot GUI by visiting http://0.0.0.0:5009 from where we can be able to add new and view already completed scans.
Using Spiderfoot to perform a scan
To perform a scan using Spiderfoot, we have to provide the domain name of our target as shown in the image below. The tool allows different ways to perform reconnaissance. Depending on the type of reconnaissance, we can choose to scan by use case, the required data or by the modules available on the tool. In this guide, we will be using an online version of OWASP juice-shop.
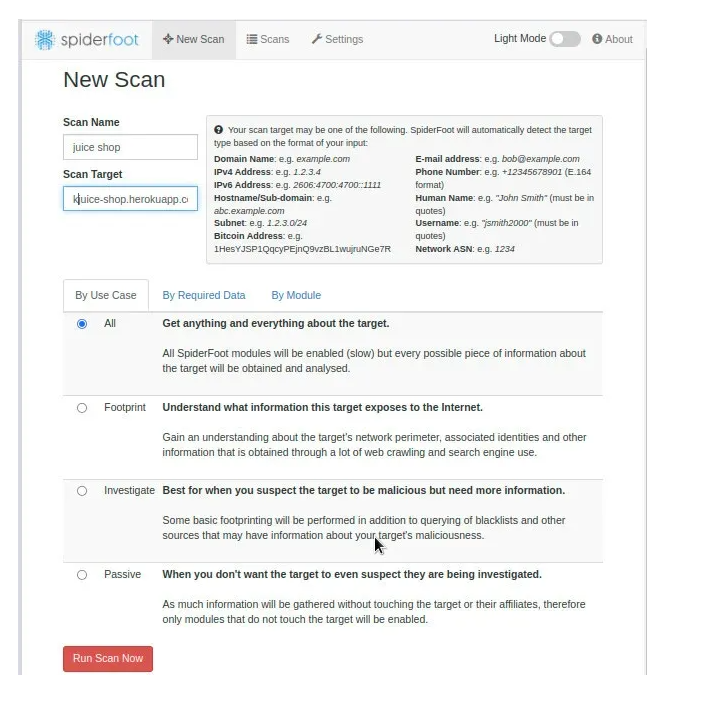
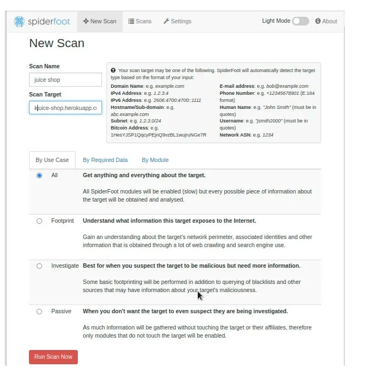
Once we have provided the required information, we can run the scan to start reconnaissance. A new task is added as shown in the image below.
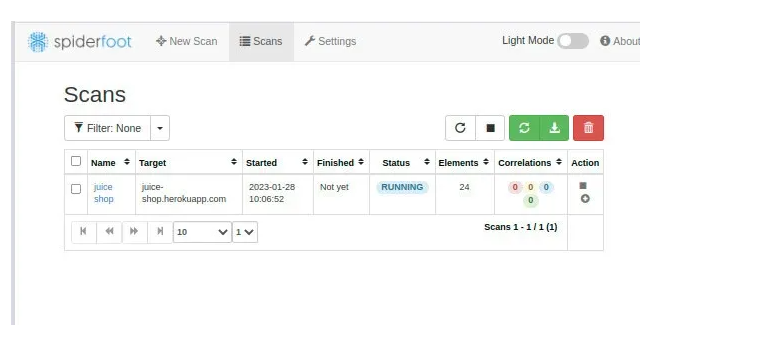
When initiating a scan, Spiderfoot diligently searches the internet to uncover any information relevant to the specified target. Moreover, Spiderfoot offers an automation feature that streamlines the process by automatically scanning the target's IP address range, extracting DNS records, and scouring various websites for specific keywords. This automation significantly reduces the time and effort required by users.
Reporting:
Spiderfoot automates the process of report creation and generation. Leveraging the collected information, the tool organizes and presents it in various formats for easy comprehension.
By accessing the project name, users can delve into specific projects to examine scan details. Each project offers options to view a summary report, correlations, elements, and a graphical representation of the project's findings.
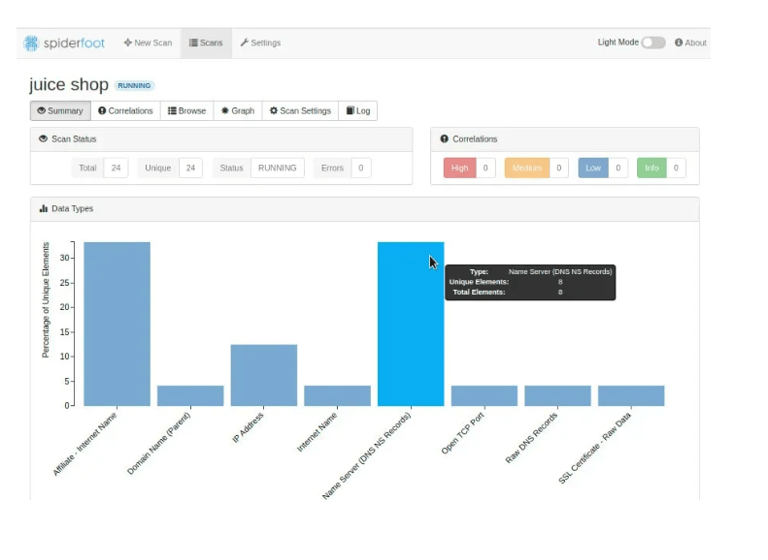
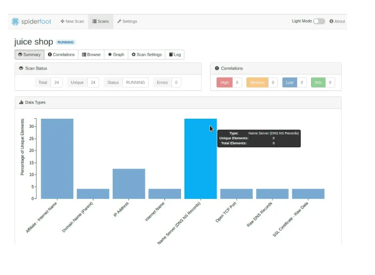
Summary Report:
The summary page provides insights into different information uncovered about the target. Spiderfoot retrieves internet-derived information related to the target, with different types of data color-coded based on their severity level.
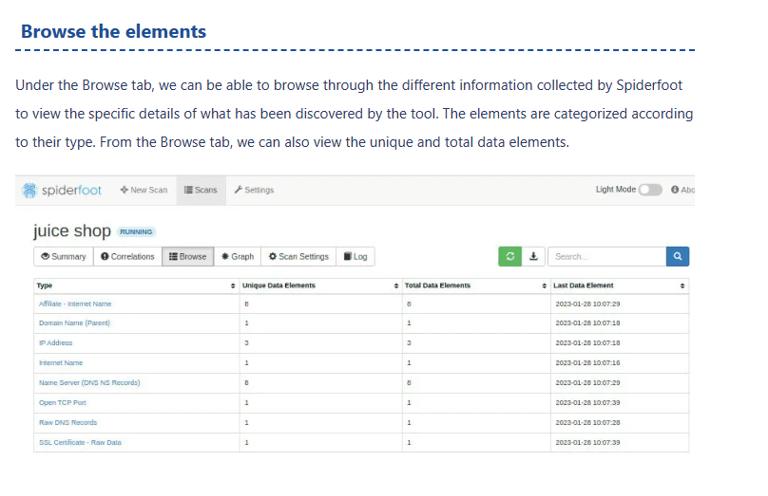
Browse the elements
Under the Browse tab, we can be able to browse through the different information collected by Spiderfoot to view the specific details of what has been discovered by the tool. The elements are categorized according to their type. From the Browse tab, we can also view the unique and total data elements.
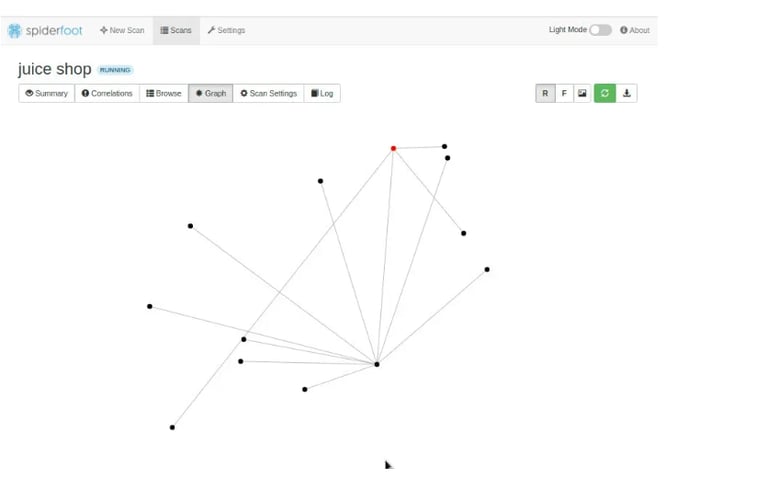
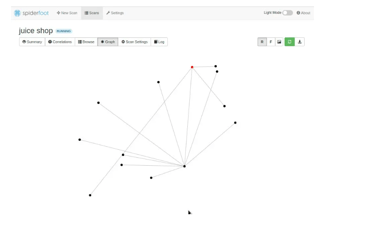
Graph
The tool has a graphical interface from where the user can view how each of the discovered elements relates.
Moreover, Spiderfoot boasts a built-in reporting functionality, simplifying the presentation of reconnaissance results to others. The reports are customizable and can be exported in PDF, HTML, and CSV formats.
Conclusion:
To sum up, Spiderfoot emerges as a potent and adaptable reconnaissance tool adept at collecting intelligence on a target. Its capacity to extract information from diverse sources, coupled with its user-friendly interface and automation capabilities, renders it indispensable for security professionals and penetration testers alike. With Spiderfoot, acquiring the necessary information for a successful reconnaissance mission becomes effortlessly achievable.
