How I Caught a Hacker Stealing Logins from HTTP POST Requests
HACKS
In many real-world breaches, the initial compromise happens silently. No ransomware, no malware, just a browser, a form, and credentials silently exfiltrated. That’s exactly what happened in today’s case.
A user reported suspicious browser behavior. Our team captured network traffic with Wireshark and began analyzing. What we found looked like nothing at first just normal browsing to a login page. But buried inside a few packets was a single HTTP POST request carrying raw usernames and passwords in plaintext.
This blog post shows exactly how we uncovered the credential theft using tshark, strings, and PCAP carving techniques.
Step 1 — Extract the Suspicious PCAP File
We start by isolating a 3-minute PCAP capture from the user’s machine. The file was named capture_1106.pcapng and opened in both Wireshark and CLI tools.
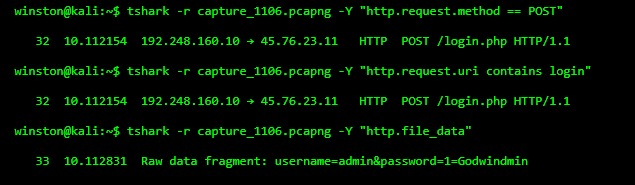
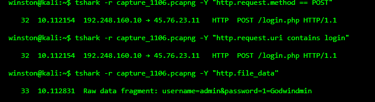
http.file_data reveals form submissions — in this case, a username and password being POSTed in plaintext. That’s a major data leak. No SSL, no TLS, and an attacker sniffing the wire could steal credentials just like this.
Step 2 — Carving Cleartext Artifacts with strings
Now that we know something suspicious was POSTed, let’s carve through the PCAP file itself using strings and grep.
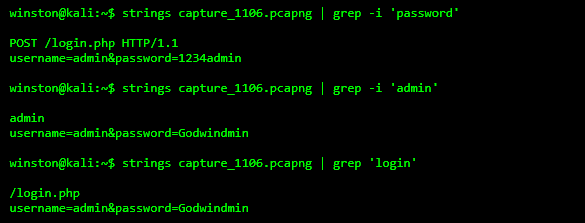
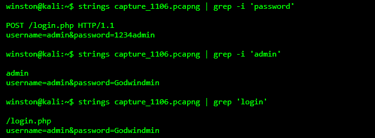
You don’t need fancy tools to find leaked credentials. A simple strings + grep combo can uncover everything, especially if SSL is not enforced. This is exactly how attackers scan PCAPs harvested from MITM or infected systems.
