How Hackers Use Mimikatz to Steal Passwords
ARTICLES


Mimikatz is one of the most powerful post-exploitation tools used by hackers to extract authentication credentials from Windows machines. It allows attackers to retrieve stored passwords, steal NTLM hashes, dump Kerberos tickets, and escalate privileges to gain complete control over a system. Originally developed as a research tool, Mimikatz has been adopted by cybercriminals, making it a significant threat to organizations and individuals alike.
Hackers do not need a username and password to move through a network once they have access to a single compromised machine. With Mimikatz, they can extract authentication data from memory and reuse it to gain unauthorized access to other systems. This technique is commonly used in targeted attacks, ransomware campaigns, and advanced persistent threats (APTs). Understanding how this tool works provides valuable insight into how attackers operate and how systems can be better protected against credential theft.
Running Mimikatz and Enabling Privileges
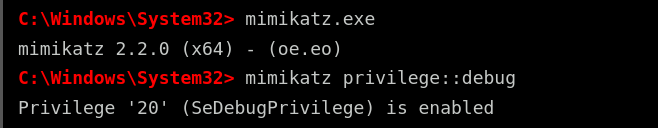
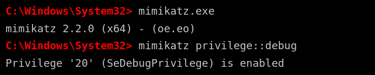
To execute Mimikatz successfully, an attacker needs administrative privileges. Once they gain access to a Windows system with elevated permissions, they can run Mimikatz from the command line. The first step is to execute the tool by typing:
mimikatz.exe
If Mimikatz is available on the system, it will start, displaying version information and a command prompt for further execution. The next step is to enable debug privileges, which are required to extract sensitive authentication data from memory. The attacker types:
mimikatz privilege::debug
If successful, Mimikatz returns a message indicating that the privilege has been enabled. This is a critical step because, without debug privileges, Mimikatz cannot access the necessary parts of Windows memory where credentials are stored.
Extracting Windows Login Credentials
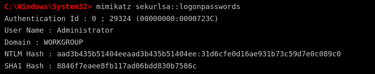
Once debug privileges are enabled, the attacker can proceed to extract stored login credentials. Windows temporarily stores authentication data in memory, allowing Mimikatz to retrieve usernames, NTLM hashes, and in some cases, even plaintext passwords. The attacker types:
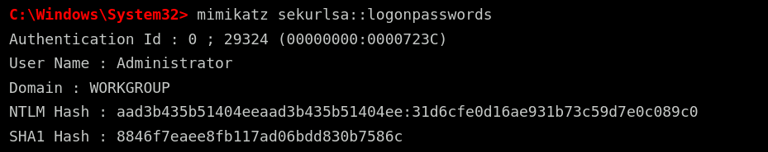
mimikatz sekurlsa::logonpasswords
After executing this command, Mimikatz scans the memory and displays authentication details of all logged-in users. The output includes session authentication IDs, usernames, domains, NTLM password hashes, and other security tokens that can be used for further exploitation.
If the attacker finds an NTLM hash instead of a plaintext password, they can still use it in a pass-the-hash attack. This allows them to authenticate to other machines on the network without ever knowing the actual password. This method is highly effective because many organizations fail to implement strong protections against hash-based authentication.
Extracting Kerberos Tickets
Many corporate environments use Active Directory and Kerberos for authentication. Mimikatz can extract Kerberos tickets stored in memory, allowing an attacker to impersonate legitimate users. This is known as a pass-the-ticket attack. By obtaining a valid Kerberos ticket, the attacker can move laterally across a network without needing additional authentication.
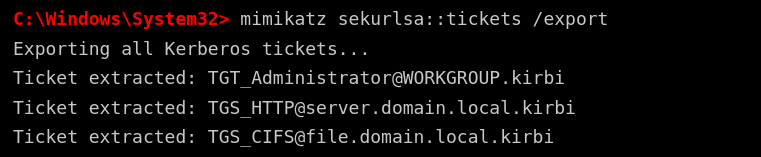
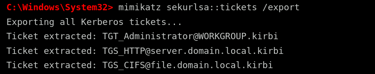
To extract Kerberos tickets, the attacker types:
mimikatz sekurlsa::tickets /export
Mimikatz scans the system for cached Kerberos tickets and saves them as .kirbi files. These tickets can then be used to access network resources as if the attacker were the legitimate user.
Escalating Privileges to Gain Full Control
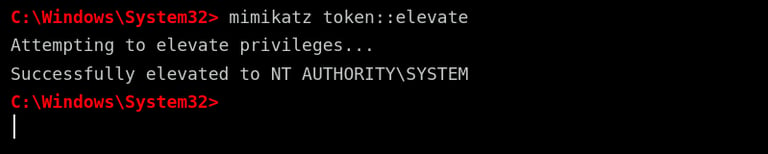
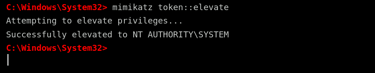
If the attacker needs to escalate privileges, they can use Mimikatz to impersonate a higher-privileged account, such as NT AUTHORITY\SYSTEM. This provides full administrative control over the machine. To elevate privileges, the attacker types:
mimikatz token::elevate
Upon execution, Mimikatz attempts to assign a system-level token to the attacker’s session. If successful, they gain full control over the Windows machine, allowing them to disable security protections, install persistent malware, and execute additional commands with the highest level of access.
Defending Against Mimikatz Attacks
Understanding how Mimikatz works is crucial in defending against it. The best way to protect systems from credential dumping is by implementing strong security measures.
One of the most effective defenses is enabling Credential Guard, a security feature in Windows that protects authentication secrets from being dumped from memory. Additionally, disabling debug privileges for non-administrators makes it significantly harder for attackers to execute Mimikatz successfully.
Organizations should enforce multi-factor authentication (MFA) to prevent attackers from reusing stolen credentials. Even if an NTLM hash is compromised, MFA can block unauthorized access attempts. Regular patching and updating Windows systems can also help, as Microsoft frequently releases security updates that make it harder for Mimikatz to extract credentials.
Monitoring security logs for suspicious activity, such as unauthorized privilege escalation and Kerberos ticket requests, can help detect Mimikatz usage early. Implementing endpoint detection and response (EDR) solutions can also help stop credential dumping before it leads to a full network compromise.
