Hackers Use Weaponized PDF Files to Deliver Byakugan Malware on Windows
BLOGS


Because of their extensive trust and widespread use, hackers often utilize weaponized PDF files as a means of attack.
Even PDF documents have the potential to harbor malicious code or exploits that capitalize on vulnerabilities within PDF readers.
Upon being unwittingly opened by a user, these nefarious PDFs execute their payload, breaching the system's defenses.
Cybersecurity researchers at Fortinet recently identified that hackers have been actively using weaponized PDF files to deliver Byakugan malware.
Technical analysis
FortiGuard Labs discovered a Portuguese PDF file distributing the multi-functional Byakugan malware in January 2024.
The malicious PDF tricks people into clicking a link by presenting a blurred table.
This in turn activates a downloader that puts a copy (requires.exe) and takes down DLL for DLL-hijacking.
This runs require.exe to retrieve the main module (chrome.exe). In particular, the downloader behaves differently when called require.exe in temp because malware evasion is evident.
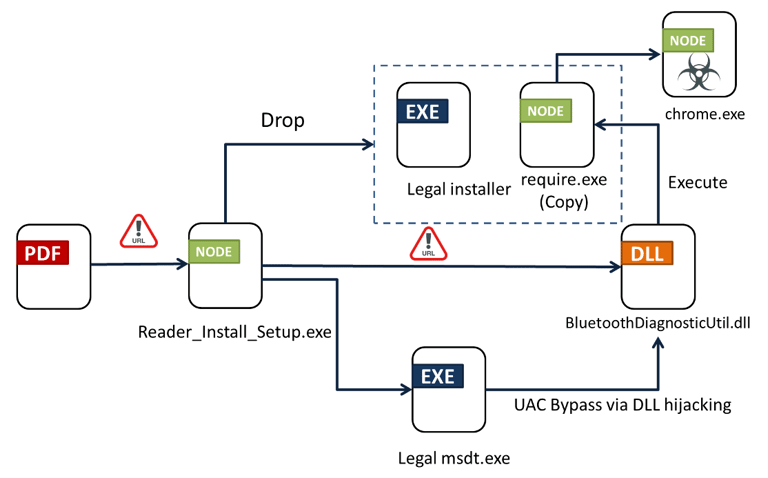
A blurred table is displayed on the victims’ screens, prompting them to click a link that enables them to download a DLL for DLL-hijacking and drop a copy (require.exe) that starts a downloader.To fetch the main module (chrome.exe), require.exe is run.
However, its behavior slightly varies depending on whether it has been renamed or not while being placed in the temp folder, which signifies its evasiveness.
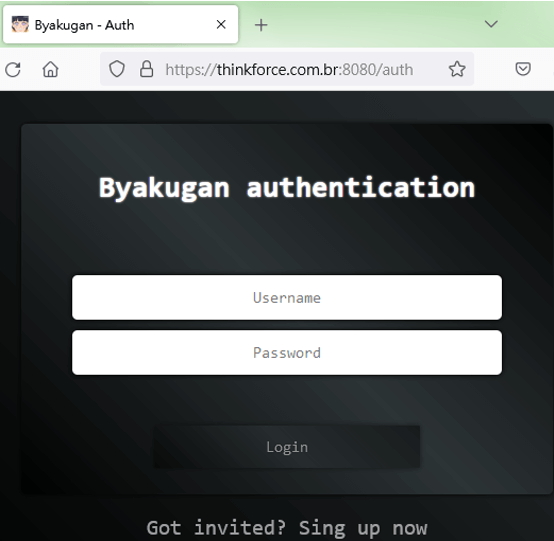
The login page (Source - Fortinet)
The login page (Source – Fortinet)
This is a malicious package built on node.js that can be executed using pkg. It comprises the primary script along with several auxiliary libraries.
As per a report from Fortinet shared with Cyber Security News, the act of downloading additional files from the %APPDATA%ChromeApplication directory, which is generated by malware, underscores its adaptability and persistence.
Byakugan features
Listed below are all the features of Byakugan:
- Screen monitoring
- Screen capturing
- Mining capabilities
- Keylogging functionality
- File manipulation capabilities
- Theft of browser information
- Anti-analysis measures
- Persistence mechanisms
This represents a growing trend of integrating malicious functionalities into malware, thereby complicating accurate identification due to increased noise.
However, the downloaded files revealed significant insights into Byakugan's inner workings, facilitating the analysis of the Trojan's harmful modules.
IoCs
Git repository
github[.]com/thomasdev33k
github[.]com/fefifojs
github[.]com/wonderreader
C2 Server
blamefade.com[.]br
thinkforce.com[.]be
Files
PDF
c7dbb5e9e65a221a5f78328b5a6141dd46a0459b88248e84de345b2a6e52b1d9
c6fe9169764301cadccb252fbed218a1a997922f0df31d3e813b4fe2a3e6326d
c9a27dbae96afb7d083577d30b2947c8ba9d1a6cb7e10e5f259f0929ef107882
exe
9ef9bbfce214ee10a2e563e56fb6486161c2a623cd91bb5be055f5745edd6479
4d8eac070b6b95f61055b96fb6567a477dbc335ef163c10514c864d9913d23cb
30991c9cac5f4c5c4f382f89055c3b5e9bb373c98ce6a5516d06db3f8a478554
