How Hackers Bypass Authentication Using Session Fixation and IDOR
BLOGS


In modern web applications, even simple oversights can lead to dangerous vulnerabilities. Two common ones are Session Fixation and IDOR (Insecure Direct Object Reference). Individually, they’re harmful — but when used together, they allow a hacker to log in as someone else, even an admin. And all of it can happen without knowing a single password. The attack doesn’t require brute force or malware — it relies purely on how sessions and user IDs are handled by the website. For this example, we’ll use a simulated target modeled after vulnerable-site.com.
Session Fixation occurs when the attacker can manually assign a session ID to a victim, and the application fails to change it after login. For instance, the attacker can trigger a link like https://vulnerable-site.com/set_session?user=admin, which sets a session cookie such as sessionid=admin1234. If the site doesn’t rotate this session upon login, it’s vulnerable. Then comes IDOR: the attacker simply changes numeric IDs in the URL or API endpoints to access data belonging to other users. By chaining both, the attacker first becomes someone else — then pivots through the platform using user IDs. It’s like stealing one key, then trying it in every door.
Once the attacker sets the session ID to admin1234, they access the admin dashboard and enumerate other users. Below is a real terminal demonstration showing the exact commands and results used during the exploit.
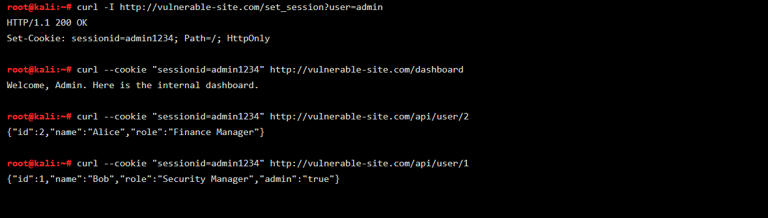
What’s Happening in the Screenshot
The first curl command sets a malicious session by visiting /set_session?user=admin. The response includes a Set-Cookie header confirming sessionid=admin1234. In the next line, the attacker uses that session cookie to access the /dashboard page — and the response proves it worked: “Welcome, Admin.” Then the attacker uses the same session cookie to hit /api/user/2 and /api/user/1. These API endpoints reveal private profile data of other users, including their names, roles, and privileges. In a real-world app, this would include email addresses, internal data, or even passwords — all exposed through insecure ID references.
How to Protect vulnerable-site.com (and any site)
The best defense against this kind of attack is strong session handling and access control. First, always rotate session IDs after login. Second, never trust client-side identifiers — always confirm the logged-in user on every request. Third, enforce strict backend authorization for every API endpoint. Don’t assume that because a user requested /user/1, they have permission to view it. Validate everything on the server — especially when session cookies and user IDs are involved.
