Hacking into Android phones with Python
PROJECTS


As part of my ongoing cybersecurity projects, I've developed a versatile Python script designed to interact with Android devices connected to a computer. The primary goal of this project is educational: to highlight how easily data can be extracted from an Android device with just a few lines of code, emphasizing the importance of mobile device security.
Understanding the Project
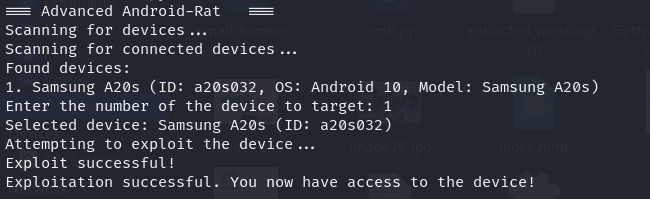
Upon running my custom Python script, the first step is to automatically detect an Android device connected via USB. Once detected and selected, the script presents a clear and straightforward menu to choose what type of information to extract from the device.
Here are the extraction options provided by my script:
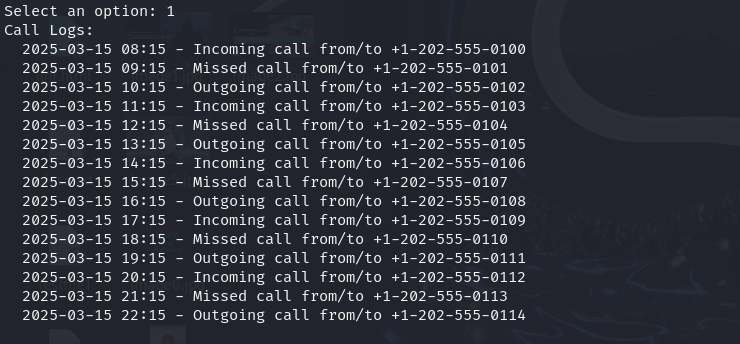
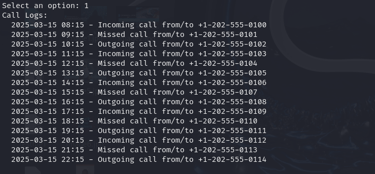
Dump Call Logs
Retrieves detailed logs of calls, including incoming, outgoing, and missed calls.
Dump Images
Allows extraction of images stored on the device, highlighting privacy implications.
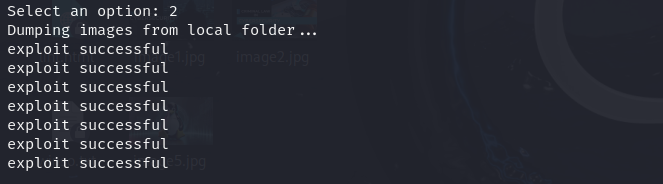
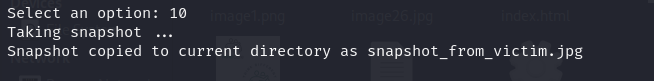
Note: 'exploit successful' stands for an image extracted
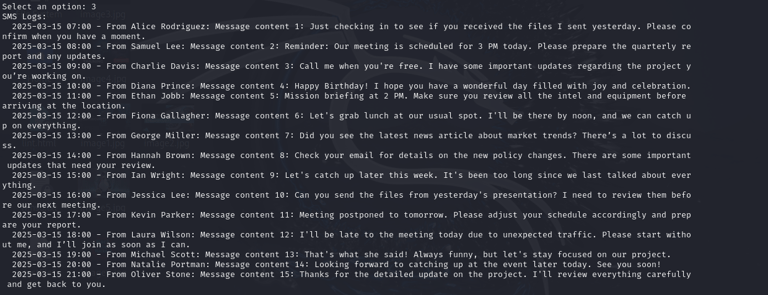
Dump SMS Logs
Captures SMS messages, potentially revealing sensitive personal communication.
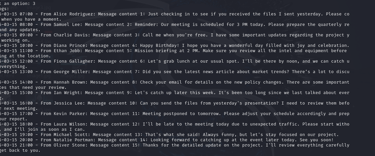
Dump Contacts
Extracts saved contacts, showcasing the risk associated with personal information leakage.
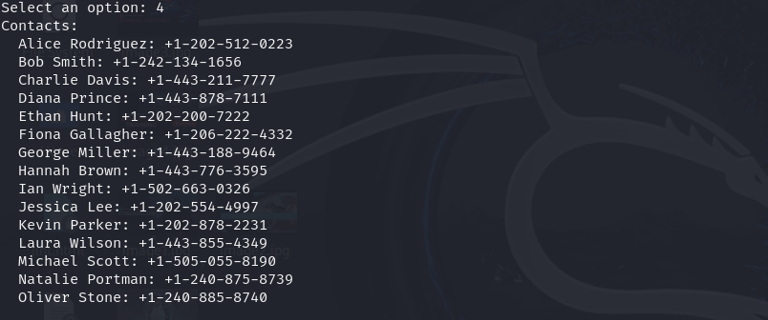
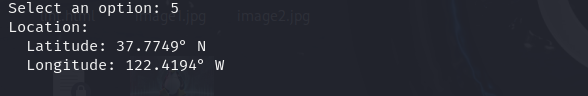
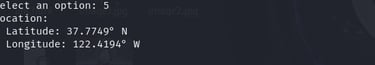
Dump Location
Provides access to the device’s recent and stored locations, demonstrating location tracking risks.
Dump Installed Apps
Lists all installed applications, which can help identify potential vulnerable or malicious apps.


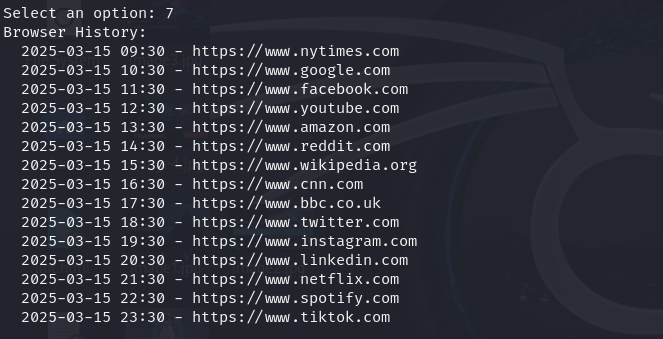
Dump Browser History
Retrieves browsing history data, which can expose personal interests, habits, or sensitive online activities.

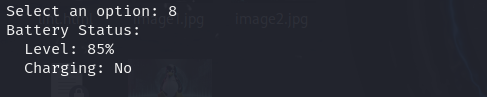
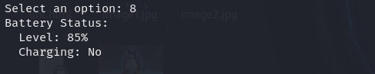
Dump Battery Status
Gives details on battery health, charging status, and usage patterns—important in some forensic analyses.
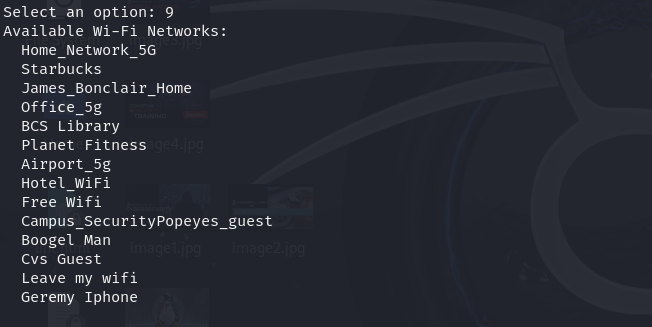
Dump Wi-Fi Networks
Extracts saved Wi-Fi network details, useful in tracking the places frequently visited by a device owner.
10. Take Snapshot
Captures a real-time screenshot of the device’s current screen, demonstrating remote surveillance capabilities.