Hacking a Vulnerable Mail Server
PROJECTS


Disclaimer: The activities described in this post were carried out in a controlled lab environment with proper authorization for educational research purposes. Unauthorized hacking is illegal and unethical.
Introduction
I’ve always been fascinated by the techniques hackers use to breach systems, and during a routine investigation, I came across a mail server that appeared to have glaring security weaknesses. Intrigued, I decided to see if I could exploit these flaws to gain unauthorized access. What I discovered was a stark reminder of how even critical systems can be compromised when proper security measures aren’t in place.
My Discovery
While scanning network traffic and running some initial tests, I noticed unusual patterns in the server’s responses. The login page was accepting unusual SQL-like input, and the server logs hinted at a lack of proper input sanitization. I suspected that this mail server was insecure—and I was determined to prove it.
Exploiting the Server
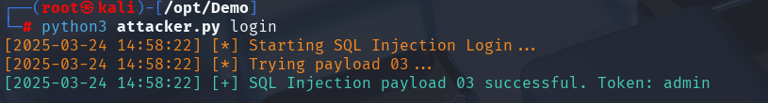
Bypassing Authentication
I started with the login. Instead of using a normal username and password, I tried entering some unusual strings into the login form. Think of it as entering secret codes that the system wasn’t expecting. I tested 11 different variations of these codes one by one. After a few tries, one of these “secret codes” worked and I got access to the server.
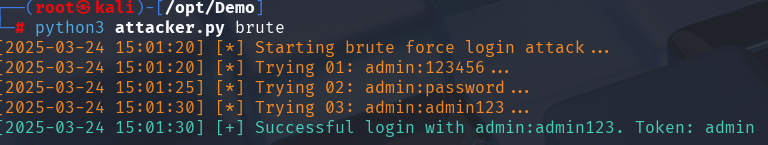
Trying Common Passwords
At the same time, I also tried using a list of common passwords for a few likely usernames. I simply tried them one after the other—almost like guessing the combination on a safe. One of the combinations worked, and I logged in.
Sending Emails
After I got in, I moved on to see how the server handled sending emails. I set up my tool to send several spam messages in a row. Although my tool showed “Sent” for every message, I later checked the server logs and saw that the server had actually processed each message—just like a real email system would.
Overwhelming the Server
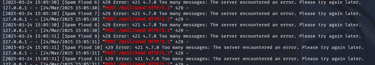
Next, I wanted to see what would happen if I sent too many emails too quickly. I launched what I call a "flood attack"—basically sending a lot of emails at the same time using many small programs (threads). While my tool still reported every email as “Sent,” the server itself was clearly overwhelmed. Its log messages showed errors like:
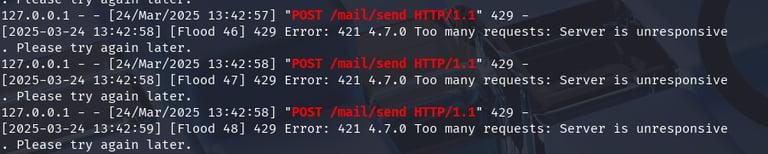
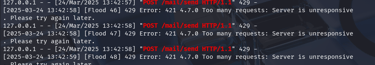
In another test, when I sent spam messages rapidly, the server’s log specifically mentioned the target email being flooded:
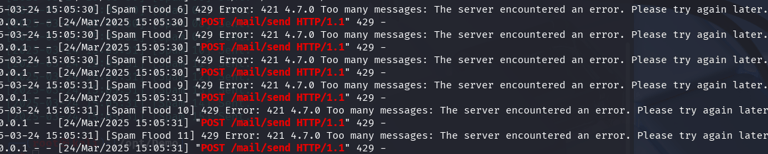
What I Learned
Breaking the Login:
By testing different secret codes and common passwords, I was able to bypass the login. This shows how dangerous it is when a system does not protect against unusual inputs or weak passwords.Email Overload:
The server couldn’t handle too many messages in a short period. When it got flooded, it started showing error messages. This tells me that proper limits and safeguards are crucial to keep a system running smoothly.Real World Impact:
Even though my tool said “Sent” every time, the real proof was in the server logs. The error messages in the logs showed that the system was overwhelmed and could crash under such conditions.
Note: Please if you are viewing on a mobile device tilt your device for a better view
