Hackers Using Cracked Software on GitHub to Spread RisePro Info Stealer
BLOGS
Cybersecurity researchers have recently discovered numerous GitHub repositories offering cracked software, serving as a delivery mechanism for an information stealer known as RisePro. Dubbed the "gitgub" campaign, this operation involves 17 repositories linked to 11 separate accounts. These repositories have since been removed by the Microsoft-owned subsidiary following the findings by G DATA, a German cybersecurity company.
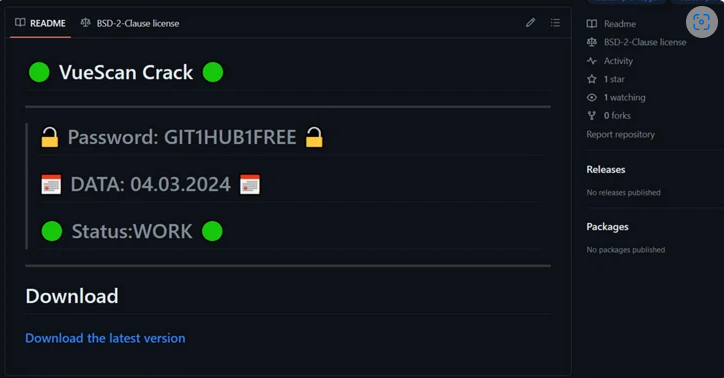
The repositories share a similar structure, each featuring a README.md file promising free cracked software. Notably, the threat actors behind the gitgub campaign added four green Unicode circles to the README.md, mimicking the status indicators often seen on GitHub. This tactic aims to lend an air of legitimacy and recent activity to the repositories.
The list of repositories includes titles such as "AVAST," "Sound-Booster," "fabfilter," and others, with download links pointing to a domain ("digitalxnetwork[.]com") hosting RAR archive files. These archives, protected by passwords disclosed in the README.md files, contain an installer file. This installer, upon execution, unpacks a next-stage payload—a 699 MB executable file aimed at thwarting analysis tools like IDA Pro. Despite its size, the actual payload within amounts to only 3.43 MB, serving as a loader to inject RisePro (version 1.6) into either AppLaunch.exe or RegAsm.exe.
RisePro first gained attention in late 2022 when it was distributed through a pay-per-install (PPI) malware downloader service named PrivateLoader.
Written in C++, this malware is crafted to gather sensitive data from compromised hosts and transmit it to two Telegram channels, commonly utilized by threat actors for data extraction purposes. Intriguingly, recent findings from Checkmarx have revealed the potential for intercepting and redirecting messages from the attacker's bot to another Telegram account.
This development coincides with Splunk's detailed analysis of Snake Keylogger, characterizing it as a multifaceted stealer malware employing various tactics for data exfiltration. Splunk highlights the use of FTP for secure file transfers, SMTP for sending emails containing sensitive data, and integration with Telegram for real-time communication and immediate transmission of stolen information.
Stealer malware has witnessed a surge in popularity, often serving as the primary vector for ransomware attacks and other significant data breaches. According to a recent report by Specops, RedLine, Vidar, and Raccoon have emerged as the most prevalent stealers, with RedLine alone responsible for the theft of over 170.3 million passwords in the past six months.
Flashpoint emphasized in January 2024 that the increasing prevalence of information-stealing malware underscores the evolving landscape of digital threats. While financial gain typically drives the use of such malware, stealers continue to evolve, becoming more accessible and user-friendly.
