Hackers Exploit Job Boards, Stealing Millions of Resumes and Personal Data
Employment agencies and retail companies chiefly located in the Asia-Pacific (APAC) region have been targeted by a previously undocumented threat actor known as ResumeLooters since early 2023 with the goal of stealing sensitive data.
BLOGS
Employment agencies and retail companies primarily situated in the Asia-Pacific (APAC) region have become targets of a previously unreported threat actor named ResumeLooters since early 2023, aiming to pilfer sensitive data.
According to Group-IB, headquartered in Singapore, the hacking group focuses on job search platforms, aiming to steal resumes. Between November and December 2023, the group compromised approximately 65 websites.
It's estimated that the stolen files contain 2,188,444 user data records, with 510,259 sourced from job search websites, encompassing over two million unique email addresses.
Security researcher Nikita Rostovcev explained, "By utilizing SQL injection attacks on websites, the threat actor seeks to pilfer user databases containing names, phone numbers, emails, DoBs, as well as details about job seekers' experience, employment history, and other sensitive personal data."
The pilfered data is subsequently offered for sale by the threat actor in Telegram channels.
Group-IB also discovered instances of cross-site scripting (XSS) infections on at least four legitimate job search websites. These XSS infections are engineered to load malicious scripts responsible for deploying phishing pages capable of harvesting administrator credentials.
ResumeLooters is the second hacking group, following GambleForce, to be identified staging SQL injection attacks in the APAC region since GambleForce's disclosure in late December 2023.
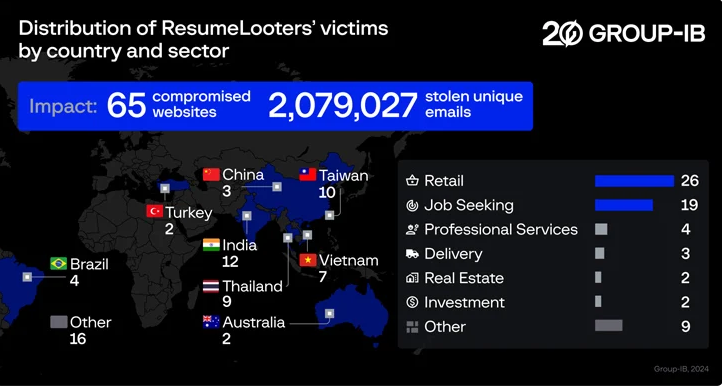
The majority of compromised websites are located in India, Taiwan, Thailand, Vietnam, China, Australia, and Turkey, with reported compromises also occurring in Brazil, the U.S., Turkey, Russia, Mexico, and Italy.
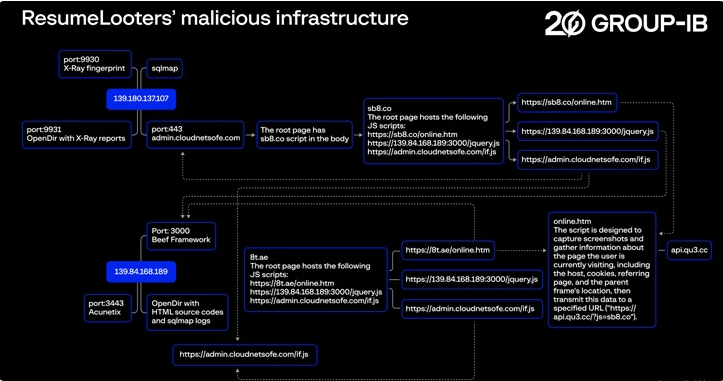
ResumeLooters' modus operandi involves leveraging the open-source sqlmap tool for SQL injection attacks. They drop and execute additional payloads such as the BeEF (Browser Exploitation Framework) penetration testing tool and rogue JavaScript code to gather sensitive data and redirect users to credential harvesting pages.
Analysis of the threat actor's infrastructure reveals the presence of other tools like Metasploit, dirsearch, and xray, along with a folder hosting the stolen data.
The campaign appears to be financially motivated, with ResumeLooters operating two Telegram channels named 渗透数据中心 and 万国数据阿力 to sell the information.
According to Rostovcev, "ResumeLooters is another example of the significant damage that can be inflicted using publicly available tools. These attacks are fueled by poor security practices and inadequate database and website management."
"It's notable to observe the persistence of old yet effective SQL attacks in the region. However, ResumeLooters' resilience stands out as they explore various methods of exploiting vulnerabilities, including XSS attacks."
