Gathering Information Using SEER
INFORMATION GATHERING

Introducing Seer, the cutting-edge OSINT (Open Source Intelligence) tool designed to revolutionize your information gathering capabilities. Seer is a python-based script which helps Cybersecurity Enthusiasts, Penetration Testers and Security Analysts gather in formations on domains and servers with ease.
Key Features:
1.IP Lookup: Seer has the ability to lookup Ip addresses to determine its location using a library known as Geoip.
2. Port Scanning: Seer can be used to scan the Ip addresses to discover open ports.
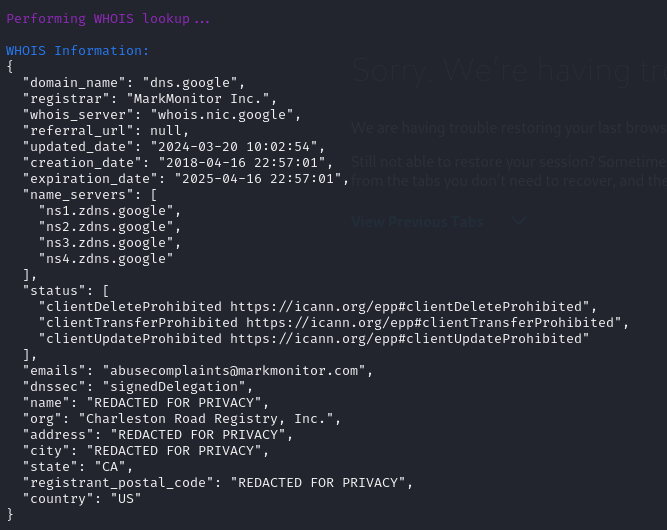
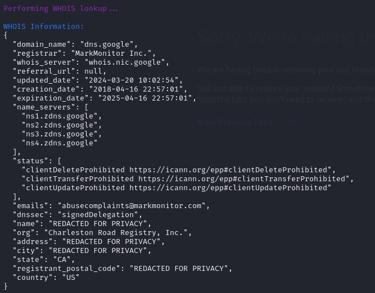
3. Whois Lookup: Seer has the ability to perform an Whois scan to get information about a domain or server.
Here's a walkthrough on how you can use Seer.
STEP 1
We Update our repository
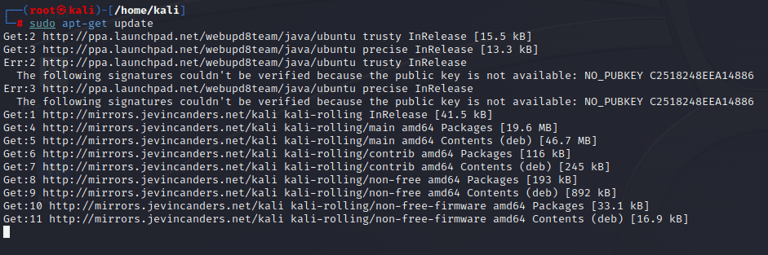
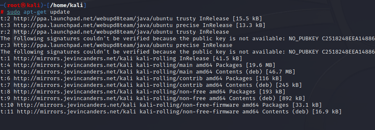
STEP 2
Clone Seer repository from Github
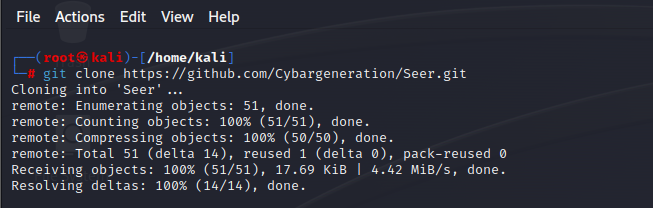
STEP 3
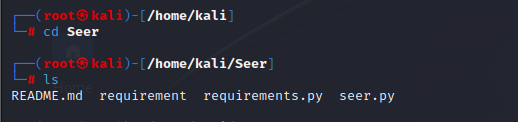
Navigate to the tools Directory using cd
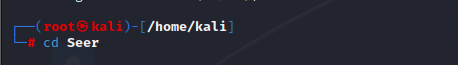
STEP 4
We use ls to view the contents of the directory
STEP 5
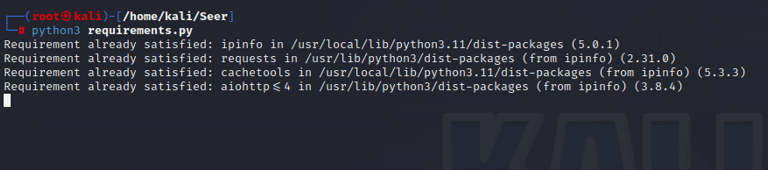
So, before we can use Seer, we have to install the required modules. we can do that by running the "requirements.py" script.
STEP 6
Now we can run Seer.py with ease.
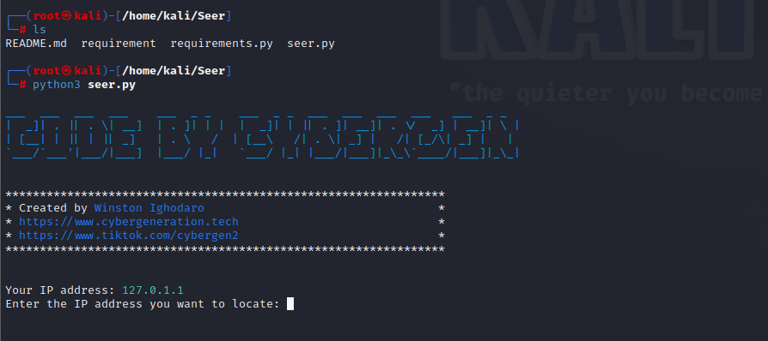
STEP 7
At this point, all we have to do is just provide the script with the Ip we want to get info on. For this tutorial I will be using google.
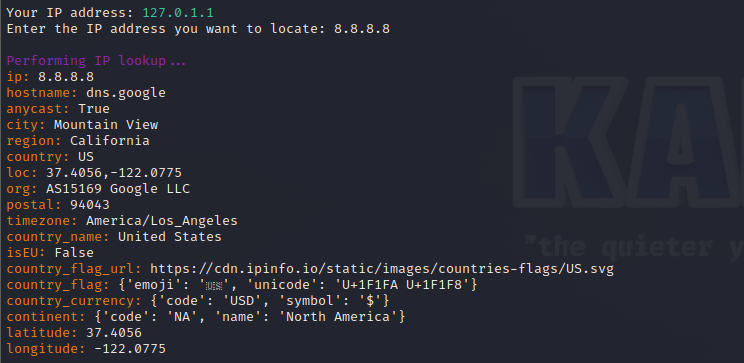
Port Scanning
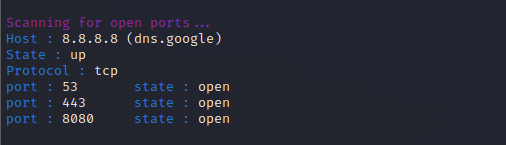
Whois Lookup