Conducting Forensic Investigations on Windows Systems
BLOGSARTICLES


Introduction
Microsoft Windows is the most widely used operating system, which makes it a primary focus for forensic investigations. As investigators, uncovering hidden evidence within the system is critical. This blog provides an in-depth exploration of various built-in tools on a Windows system, with a particular emphasis on the Windows Registry and the wealth of information it holds.
Step 1: Investigating System Processes with Task Manager
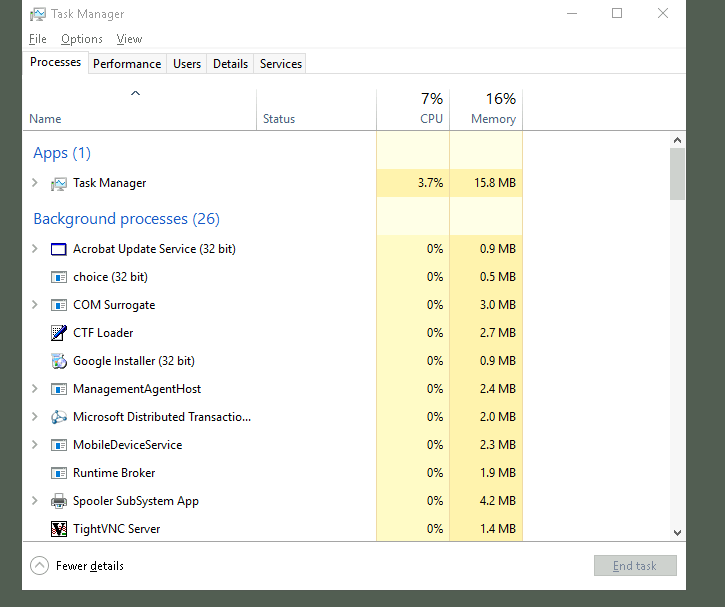
We start our investigation by utilizing Task Manager, a built-in utility in Windows that provides a snapshot of currently running processes. To access Task Manager, right-click on the taskbar and select "Task Manager," then switch to the "Processes" tab. This tab displays running applications, background processes, and essential system services.
Common processes like System (ntoskrnl.exe), winlogon.exe, explorer.exe, and lsass.exe are vital for Windows to function correctly. However, attackers often mimic these processes to hide malicious activities. By adding the "Command line" column in Task Manager, you can view the full path of each process. This makes it easier to identify anomalies, such as an explorer.exe process running from a temporary folder, which could indicate a potential threat.
Step 2: Monitoring Network Activity with Resource Monitor
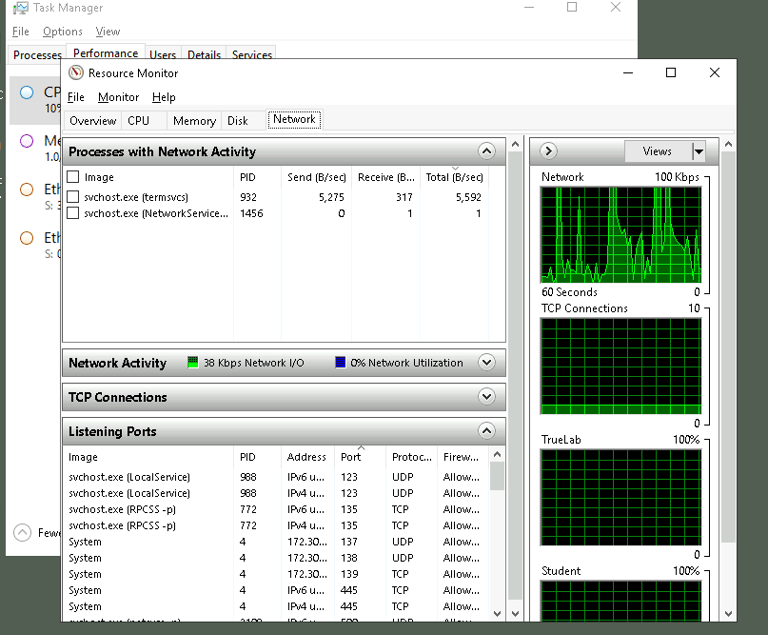
After reviewing the system processes, we move on to monitoring network activity. In Task Manager, navigate to the "Performance" tab and click "Open Resource Monitor" to launch a utility that provides real-time information about network connections and the processes using them.
By selecting the "Network" tab, we can examine the "Listening Ports" section. Malicious software often opens ports to create backdoors to external servers. Identifying unknown processes listening on ports can be an early indication of a security breach. For example, if a process is communicating with a suspicious IP address or using an unusual port, it warrants further investigation.
Step 3: Uncovering File System Information Using Command Prompt
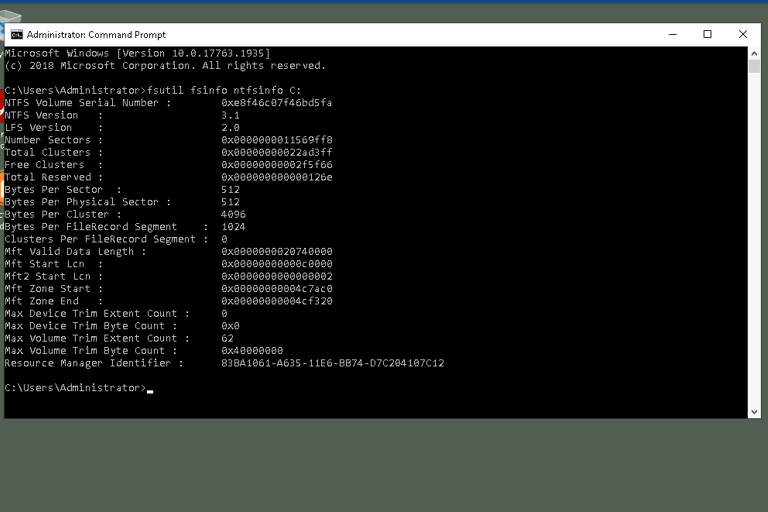
The next step involves using the Command Prompt to delve into the system's file structure. By executing the command fsutil fsinfo ntfsinfo C:, we retrieve detailed information about the file system, such as cluster sizes, free space, and serial numbers. This data can help detect irregularities, such as hidden data in areas of the drive marked as "bad clusters." Understanding the total and free clusters allows us to identify if any space is potentially being used to hide information.
Another useful command is fsutil usn queryjournal C:, which accesses the USN (Update Sequence Number) journal. This journal logs file system changes, including additions, deletions, and modifications. It provides a chronological record of file activities, enabling investigators to reconstruct user actions and detect attempts to cover tracks.
Step 4: Deep Dive into the Windows Registry
The Windows Registry is a hierarchical database that contains system and user information, including software settings, hardware configurations, and security policies. It serves as a goldmine of data for digital forensic investigations. This section explores several critical registry keys and how they can be used in investigations.
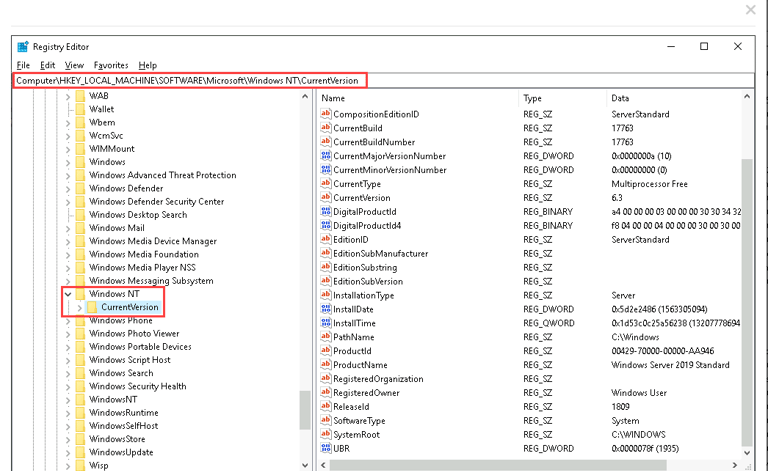
1. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion
The HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion key provides detailed information about the Windows installation. Key values such as ProductName, InstallDate, and CurrentBuild offer insights into the operating environment.
ProductName identifies the specific Windows version (e.g., "Windows 10 Pro"), helping investigators understand the system environment.
InstallDate, stored as a hexadecimal value, can be converted into a human-readable date. This is crucial for building a timeline of events. An unusual or recent installation date could indicate an attempt to reinstall the system to cover up malicious activities.
CurrentBuild reveals the Windows build number, which can provide clues about potential vulnerabilities targeted by specific exploits or malware.
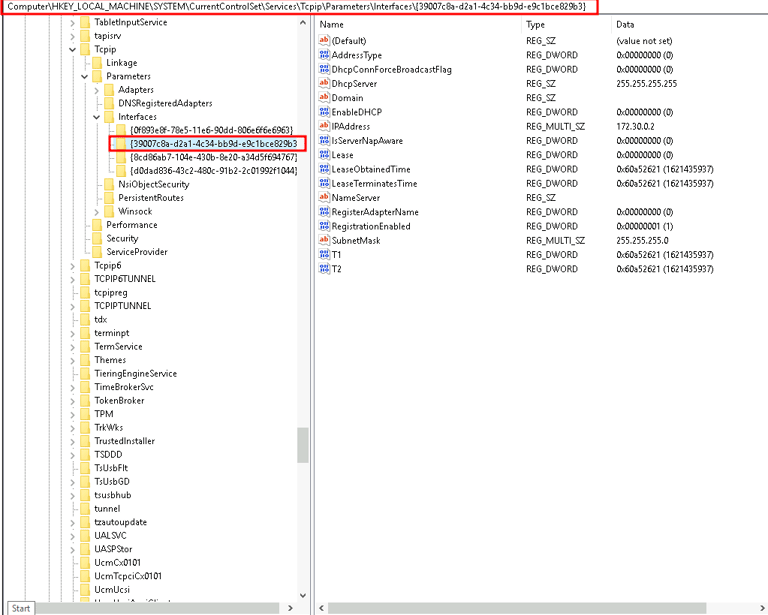
2. HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters\Interfaces
This registry key contains network-related information, including settings for network interfaces on the system. Inspecting this key provides valuable details about the machine's network configurations, which can be critical in network-based investigations.
IPAddress lists the IP addresses assigned to network adapters. Comparing these addresses with known IP ranges can reveal unauthorized network connections.
DefaultGateway shows the network's default gateway, aiding in mapping the system's network connections.
DNS Server indicates the DNS servers in use. Attackers sometimes alter DNS settings to reroute network traffic for malicious purposes. Identifying changes here can uncover potential external threats.
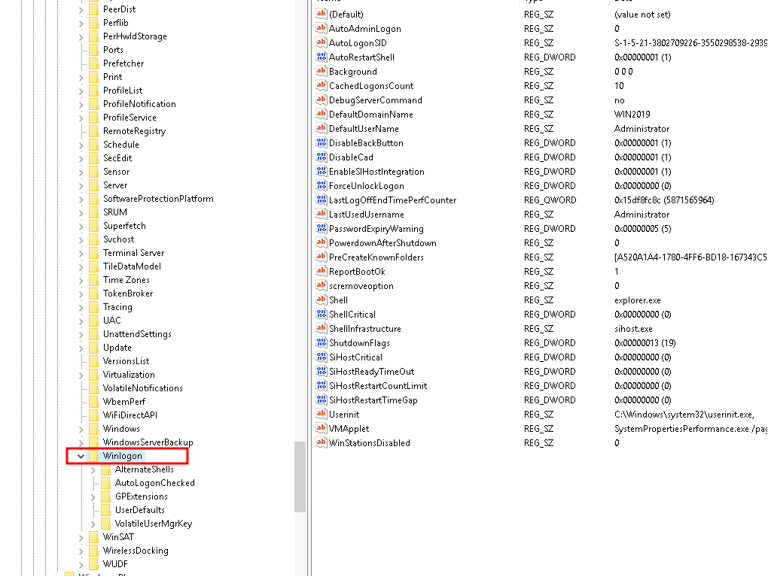
3. HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
The Winlogon key is a vital component of the Windows logon process, containing information about user logins, startup applications, and security settings.
Shell is usually set to explorer.exe, which specifies what runs after a user logs in. If this value points to a non-system path, it might indicate that malware is running during login.
Userinit, typically set to C:\Windows\system32\userinit.exe, may be modified by attackers to execute malicious code during the logon process.
Identifying modifications to the Shell or Userinit values can reveal how malware establishes persistence on the system, providing critical clues in a forensic investigation.
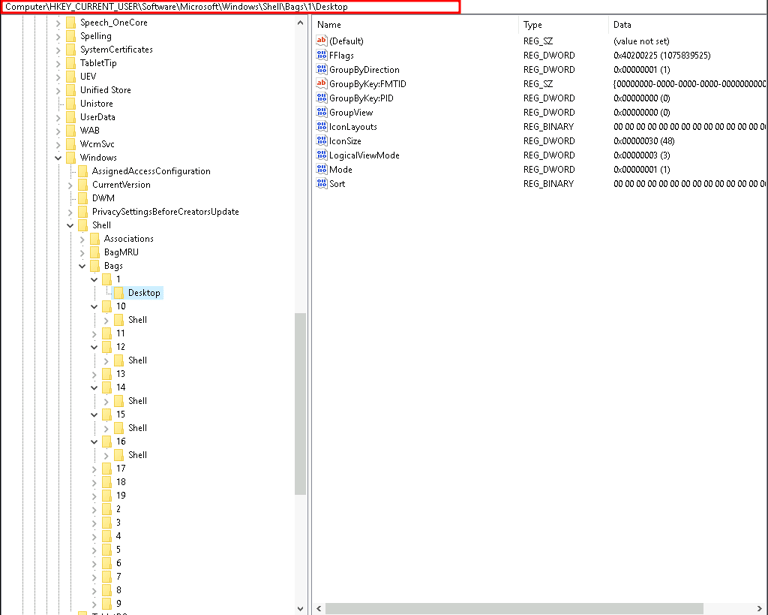
4. HKEY_CURRENT_USER\Software\Microsoft\Windows\Shell\Bags
ShellBags record folders accessed by the user, including layout settings in Windows File Explorer. They do not directly store file names but keep records of folder paths and display settings. This information can be parsed using tools like ShellBags Explorer to reconstruct a user’s folder navigation history.
The presence of ShellBags can provide evidence that a user accessed certain folders, even if those folders have been deleted. This can be crucial in proving user awareness and access to specific directories containing sensitive content.
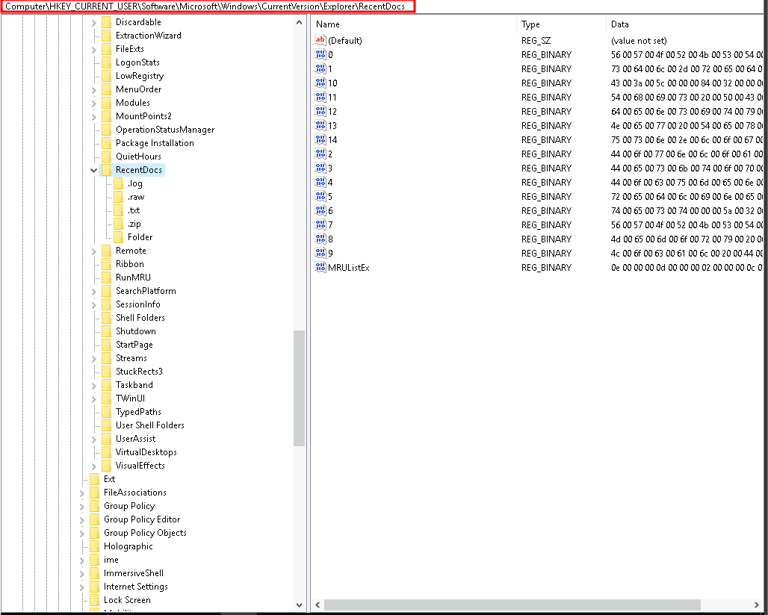
5. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\RecentDocs
The RecentDocs key logs the files recently accessed by the user through File Explorer, including both file names and paths. This trail of user activity is invaluable, especially when files have been deleted or moved, as the registry retains these references.
For instance, finding references to files named "bank_account_details.docx" or "password_list.txt" in this key can indicate suspicious activity, especially if these files are no longer present on the system.
Conclusion
In this forensic exploration, we utilized various tools to uncover critical information on a Windows system. The Windows Registry, in particular, revealed vital clues. By examining keys such as CurrentVersion and Interfaces, we gathered information about system setup and network configurations. The Winlogon key provided insights into potential malware persistence mechanisms, while the ShellBags and RecentDocs keys offered a glimpse into the user's activities, even if attempts were made to conceal them.
Understanding the significance of each registry key and knowing how to analyze them is essential in conducting a thorough forensic investigation on Windows systems.
