Footprinting with Nmap in Kali Linux
INFORMATION GATHERING
Footprinting encompasses the process of gathering crucial information about a target network or computer system, including OS versions, kernel details (for Linux-based systems), and web hosting software versions (for server targets). This reconnaissance can be both active and passive. Active Footprinting entails direct interaction with the target, such as conducting Nmap scans. Conversely, passive footprinting methods aim to gather information without alerting the target.
Various tools are available for conducting footprinting on different networks and systems, with popular options including Nessus, Weblister, Harvester, and Nmap. However, this article will focus specifically on Nmap.
Nmap, an open-source network exploration tool, excels in swiftly scanning large networks and retrieving diverse information. One of its most valuable features is the port table, which provides an overview of available ports and their statuses: open, closed, or filtered. Additionally, Nmap offers DNS information, OS guesses, MAC addresses, and more.
The primary functionality of Nmap centers around port scanning. Here are the available port statuses in Nmap:
1. Open: Indicates that an application on the target actively accepts TCP connections, UDP datagrams, or SCTP associations on the port. Open ports present opportunities for exploitation.
2. Closed: Respond to data requests, but no application is listening on them. Nmap uses closed ports to determine the OS or scan the provided IP address for live hosting.
3. Filtered: Nmap cannot ascertain whether these ports are open or not as they are shielded by dedicated firewalls or router rules. Sometimes, they respond with ICMP error messages to confuse potential exploiters.
4. Unfiltered: Accessible ports where Nmap cannot determine whether they are open or closed, typically occurring in ACK scans.
5. Open | Filtered: Port state when Nmap is unable to distinguish whether the port is open or filtered, often encountered when an open port does not respond.
6. Closed | Unfiltered: Nmap cannot determine whether the port is closed or unfiltered, commonly observed in IP ID idle scans.
Nmap offers various scan types, each tailored for different purposes:
1. TCP Scan: Checks and initiates a three-way handshake between sender and target. This scan type can be noisy.
2. UDP Scan: Determines whether a UDP port is open on the target system. Unlike TCP scans, UDP scans lack a positive acknowledgment response, potentially leading to false positive responses.
3. SYN Scan: Similar to TCP scan, but Nmap itself crafts the SYN packet.
4. ACK Scan: Identifies whether a port is filtered or not.
5. FIN Scan: A stealth scan method that sends TCP FIN packets instead of SYN requests.
6. NULL Scan: Clears all connections and resets everything.
7. IDLE Scan: The stealthiest Nmap scan, utilizing a third-party host's open ports for reconnaissance.
Nmap's basic syntax is:
With numerous options available, users can customize their Nmap scans based on specific requirements and objectives.
Scan types available in Nmap are:
TCP scan: Used to check and perform a three-way handshake between sender and target. It is very noisy.
UDP scan: This scan is performed to check whether a UDP port is open on the target system or not. Unlike TCP scan, this does not have a positive acknowledgment response so, it might sometimes give false positive responses.
SYN scan: This is another way of a TCP scan; the Nmap itself creates the SYN packet only difference being that Nmap itself creates the SYN packet.
ACK scan: Used to determine whether a post is filtered or not.
FIN scan: It is a kind of stealth scan, which send TCP FIN packets rather than SYN requests.
NULL scan: Clears all the connections and clears everything to clean.
IDLE scan: This is the stealthiest scan of Nmap thus far.
Commands in Nmap
Let’s discuss various options that could be used according to one’s needs, with Nmap
1. Options with scanning techniques: Nmap provides the following options with scans:

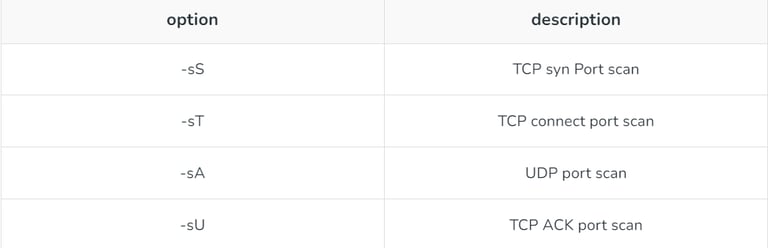
2. Options related to HOST discovery: Following list gives options associated with HOST discovery:
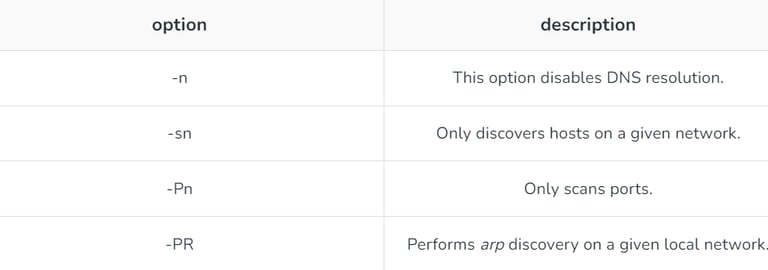
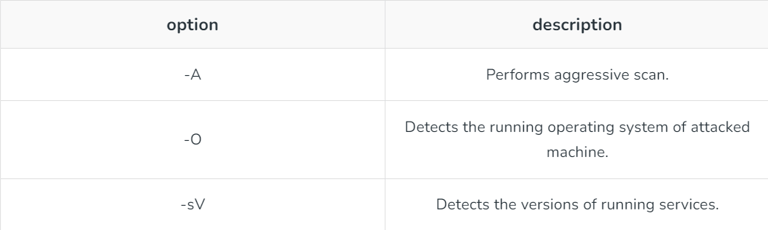
3. Options for detecting OS and version of running services: List of options used for detecting OS and versions of running services:
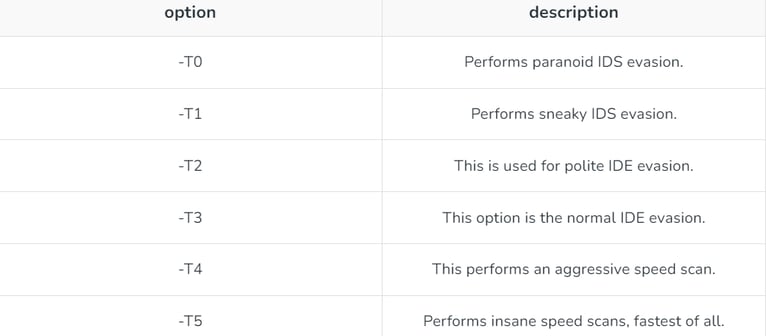
4. Timing and Performances options: These options decide the time and performances of the performed scanning.
5. Port specifications: Options provided with port scanning.
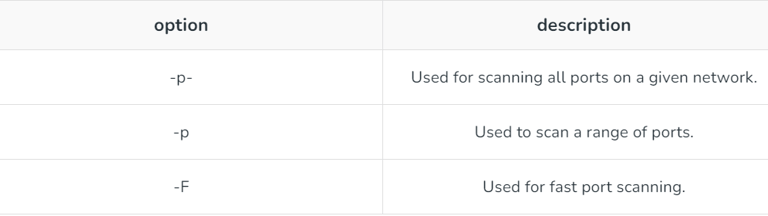
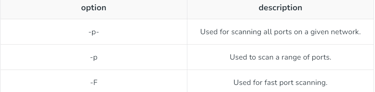
Example of Nmap scan
Let us use a result of a Nmap scan to understand and interpret that result. The following command was used and its output is saved in a file named nmap_res.txt.

The output of this command should be something like this
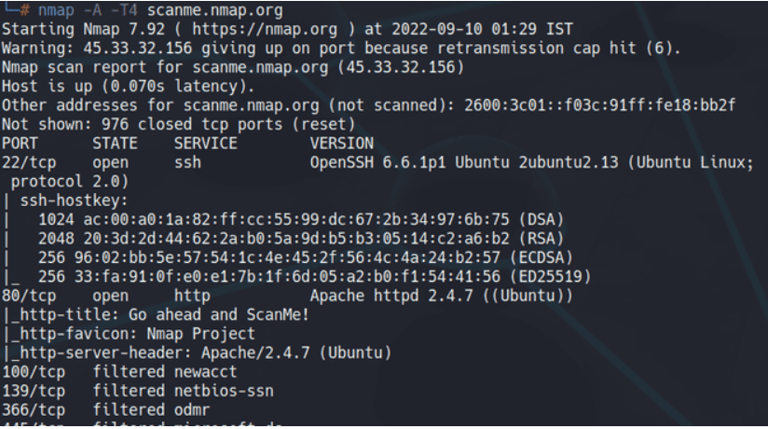
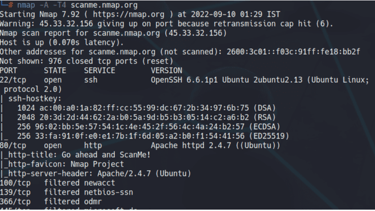
Now, let us go one by one through different parts of the result and understand them.
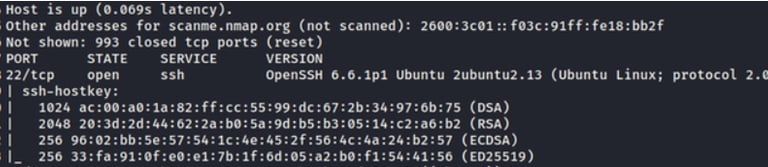
In this scenario, Nmap confirms the operational status of the provided domain and provides its IPv4 and IPv6 addresses. Moving on to the ports, which are arguably the most informative aspect of Nmap's output. It immediately reveals that TCP port 22 is open, indicating that SSH is active. Additionally, Nmap discloses the version of OpenSSH in use. This information can be leveraged to search for specific exploits targeting this version or to utilize the SSH keys provided to exploit the network. Now, let's proceed to the next section.
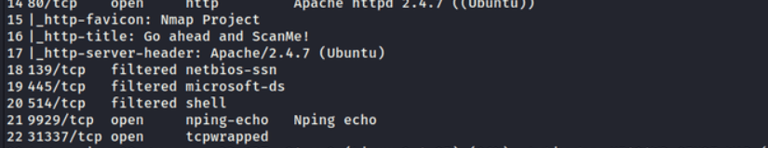
Now, we get more port information such as ports 139, 445, and 514 are filtered. However, ports 80, 9929, and 31337 are open. Now, here port 80 is an HTTP port, which could be exploited as we also get the version of the server it is running on ‘Apache httpd 2.4.7 (Ubuntu)’. One can use any exploit for this version.
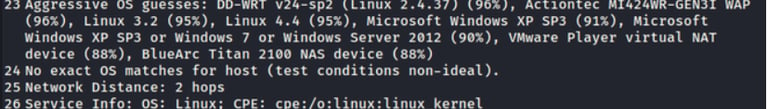
Here, Nmap gives us guesses of the possible OS running on the backend machine. It gives the probability for the different OS as the target has filtered it from the enumeration.


