Defending Your Network: Using Infection Monkey for Simulated Attacks
ARTICLESBLOGS


In this blog, we’ll explore a powerful tool called Infection Monkey and see how it helps us understand network security. Infection Monkey simulates cyberattacks on a network, allowing us to spot weaknesses and learn how to defend against them before a real attacker gets the chance.
Why Use Simulated Attacks?
Imagine trying to fix leaks in a boat. Instead of waiting until you’re out at sea, it’s better to splash water on the boat to find the leaks and patch them up while you’re still on shore. That’s what we do with Infection Monkey. It’s like having a skilled hacker on your side, pointing out weaknesses without doing any damage. This way, you can test your security and fix problems before a real attack happens.
Getting Started with Infection Monkey
Infection Monkey is a tool designed for Breach and Attack Simulation (BAS). It mimics the tactics of a real hacker, testing your network’s defenses by trying different methods to break in. Let’s see how it works step by step.
1. Launching Infection Monkey
We begin by accessing the Infection Monkey interface through a web browser. From here, we configure the tool to simulate an attack. You have options to choose the type of attack and set the targets.
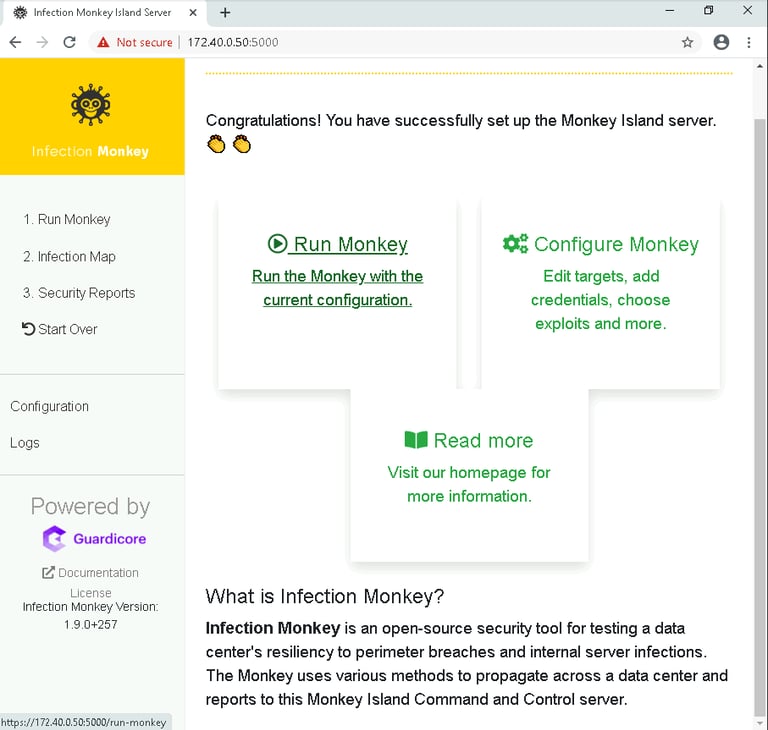

Think of this as setting up a controlled test. Infection Monkey is like an ethical hacker probing the network for weak spots. It checks for vulnerabilities like outdated software, open ports, and weak passwords.
2. Watching the Attack Spread with the Infection Map
Once we start the simulation, we can track the progress using the Infection Map. This visual map shows how the simulated malware spreads from one device to another, like a virus moving through a population.
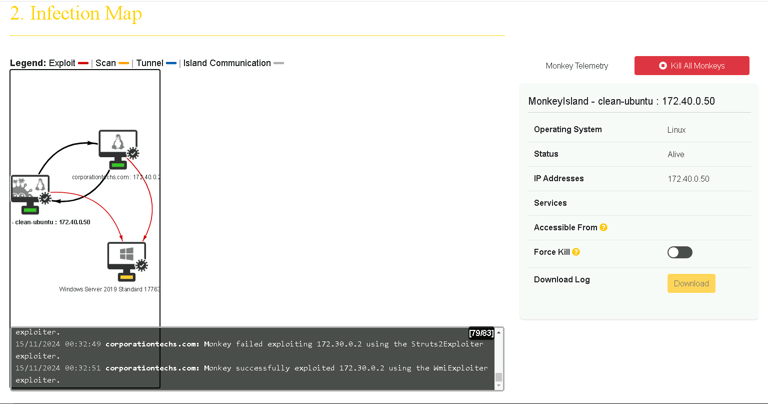
The Infection Map helps us understand how quickly an attack could spread across a network. It gives us a clear view of which devices are compromised and how they were infected, providing valuable insights for improving our defenses.
3. Reviewing the Attack Timeline
The next step is to look at the Exploit Timeline, where we can see each attempt made by Infection Monkey. It lists every exploit used, showing which ones succeeded and which failed.
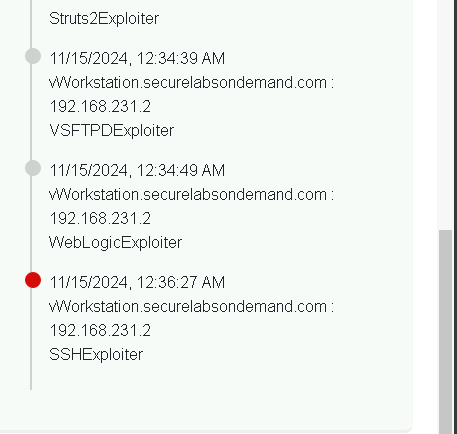
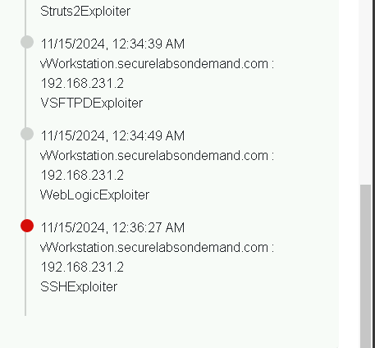
The timeline is like a play-by-play of the attack. It tells us what techniques were tried, such as brute force attacks or exploiting outdated software. Understanding these methods helps us know what defenses need strengthening.
4. Analyzing the Security Report
Infection Monkey also provides a detailed Security Report after the simulation. This report includes a list of vulnerabilities found and recommendations on how to fix them.
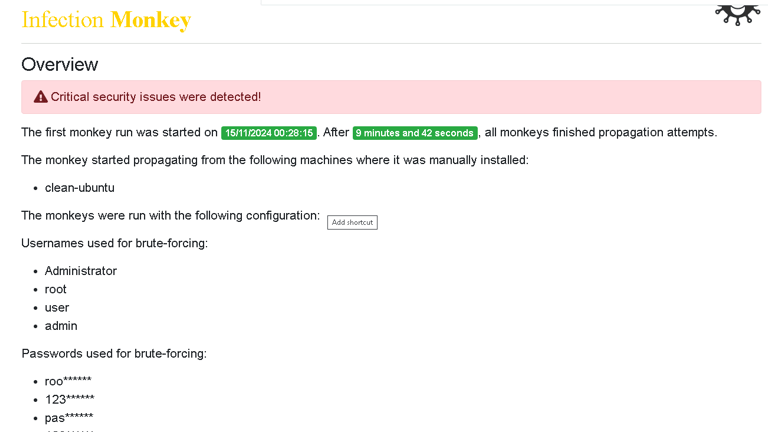
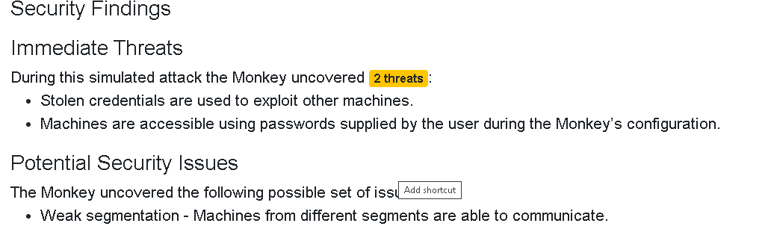
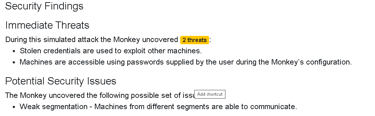
The report is like a checklist for improving your network’s security. It might suggest patching software, changing configuration settings, or blocking certain network traffic. Following these recommendations can significantly boost your defense against real threats.
Responding to the Attack: Using Antivirus and Patches
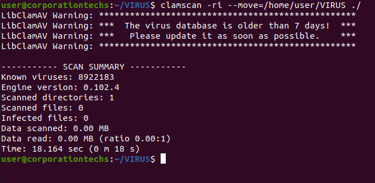
After running the simulation, it’s time to clean up and fix the issues discovered by Infection Monkey. We use antivirus tools like ClamAV to scan for and remove any suspicious files left behind.
1. Scanning for Malware with ClamAV
ClamAV is an antivirus tool that scans the system for malicious files. It’s like having a digital security guard inspect every corner of your network.
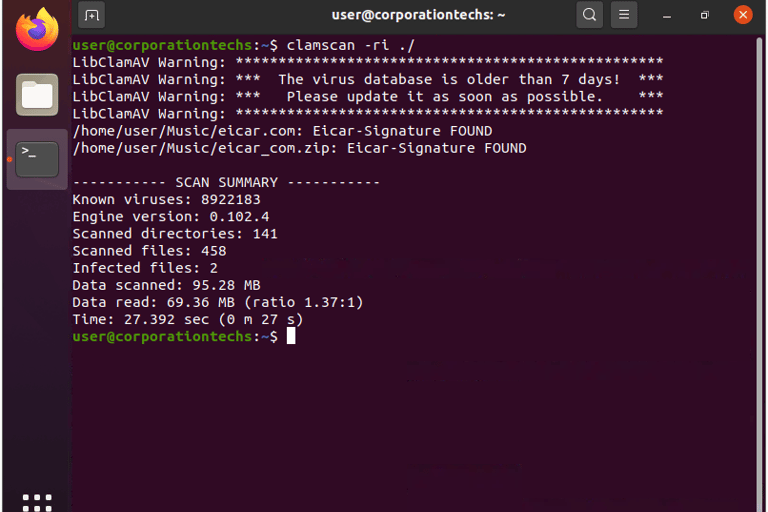
The scan identifies any suspicious files that need attention. This helps us isolate and remove potential threats, keeping the network safe from further damage.
2. Quarantining and Removing Infected Files
Once the malware is detected, we quarantine it by moving the infected files to a secure folder. This step ensures that the malicious files can’t spread or cause more harm.
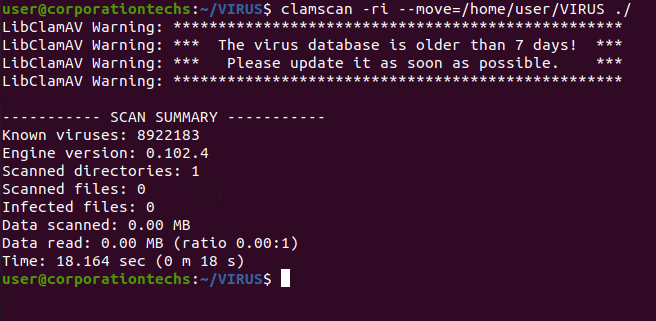
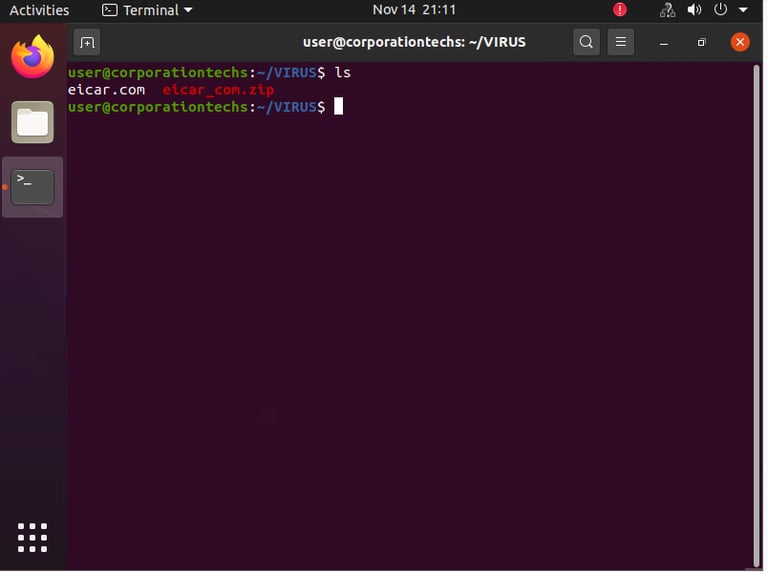
Quarantining is like locking the infected files in a secure vault. It’s a safe way to handle potential threats without accidentally deleting important files.
3. Applying Security Patches
One of the best defenses against attacks is keeping your software up to date.
Patches are like repairs for your software. They close security holes that attackers might use to get in. By applying these updates, we reduce the risk of similar attacks happening in the future.
